Active Directory (AD)
What is Active Directory?
Active Directory is a proprietary directory service developed by Microsoft® to provide secure access to corporate networks. Active Directory stores information related to user accounts, computer objects, groups, policies and other resources on the network. It also provides an efficient way for administrators to manage the security settings of their organization's IT infrastructure.
AD was developed to manage the authentication and authorization of users and machines on a Windows domain network.
With Active Directory, administrators can easily control who has access to what resources on the network. They can also set up automated processes for managing user and computer permissions across multiple systems with ease.
Active Directory was first released in 2000 and runs on Windows Server. Since then, it has become the umbrella brand for a broad assortment of directory-based identity services from Microsoft.
Microsoft introduced Azure AD to support cloud-hosted infrastructures. Azure AD Connect was then introduced to help bridge the on-prem AD with cloud-hosted Azure AD.
Note: Active Directory and Azure AD are not the same. This glossary page is on Active Directory.
What are the primary components of Active Directory?
These are the six main components of AD: Active Directory Domain Services, Domain Controller, Lightweight Directory Services, Federation Services, Rights Management Services, and Certificate Services.
- Active Directory Domain Services (AD DS): Active Directory Domain Services (AD DS) provides directory services for managing Windows-based computers on a network. AD DS stores information about objects such as users, groups, computers, and other resources, and provides authentication and authorization services.
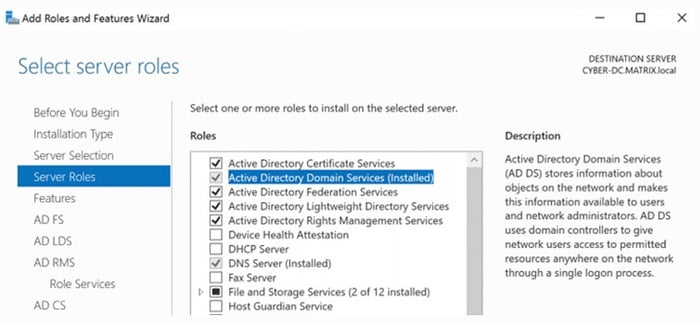
AD Server Roles
Active Directory uses a structured data store, which organizes directory information and is optimized to enhance query performance, making it easy for network users to quickly find and utilize any information they need. - Domain Controller: A domain controller (DC) is a network server that responds to security authentication requests and authorizes host access to domain resources. This server enforces security policies, authenticates registered users, and stores important user account information. Domain controllers manage and secure domain networks by only allowing authorized users access to directory services while denying unauthorized access.
- Lightweight Directory Services (AD LDS): AD LDS is a Lightweight Directory Access Protocol (LDAP) directory service that offers dedicated data storage and APIs for accessing stored information. It functions independently of Active Directory and can function as a standalone data store or can replicate data.
- Federation Services (AD FS): Active Directory Federation Services (AD FS) is a service that allows the secure sharing of identity information between trusted business partners. It is based on industry standards and facilitates federations across extranets, enabling trusted partners to share sensitive identity data.
- Rights Management Services (AD RMS): AD RMS enables users and admins to control access permissions for sensitive documents, workbooks, and presentations. By utilizing IRM policies, unauthorized individuals are prevented from duplicating and disseminating the restricted information.
- Certificate Services (AD CS):
Active Directory Certificate Services (AD CS) is a Windows server designed to issue digital certificates. AD CS offers digital certificates that have a wide range of applications, including the encryption and digital signing of documents and messages, as well as authenticating computer, user, or device accounts on a network. Certificates granted by AD CS are valid for a specified period and can be renewed or revoked as needed, providing granular control over the certificates' lifespan.
How is data organized in Active Directory?
Data is stored in Active Directory as objects and organized by name and attributes. A group of objects that share the same Active Directory database is called a domain. One or more domains with a common schema and configuration constitute what is known as a tree. The top tier of Active Directory’s logical structure is a forest, which is made up of a group of trees. A forest constitutes Active Directory’s security boundary.
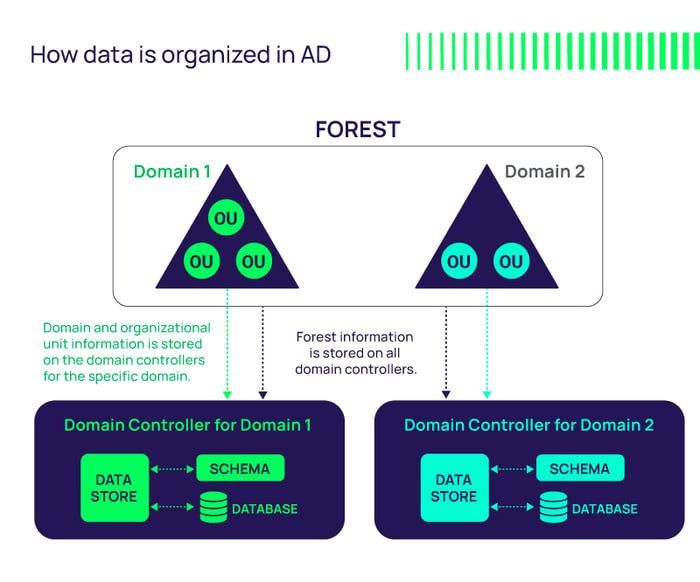 Source: AD Structure - Source Microsoft.com Docs
Source: AD Structure - Source Microsoft.com Docs
- Domains are fundamental data structures in Active Directory, representing a collection of related objects (such as users and devices) that share the same database. A unique DNS name, like company.com, identifies each domain.
- Trees, on the other hand, are collections of one or more domains that possess a contiguous namespace. This means that all the domains within a tree share a common DNS root name, such as marketing.company.com, engineering.company.com, and sales.company.com.
- Forests, which consist of one or more trees, serve as the security boundary within an enterprise network. They share a common schema, global catalog, and directory configuration. Unlike trees, forests need not have a contiguous namespace, allowing for flexibility in structuring an enterprise network.
- Organizational units (OUs) provide a way to group objects within a domain for simplified administration and policy management. OUs are created by administrators to mirror functional, geographical, or business structures within an organization. They assist in delegating control over resources to various administrators and allow for the application of group policies specific to each OU.
By employing these data structures, Active Directory effectively organizes and manages network user data, resource information, and administrative policies within a hierarchical framework.
Why is Active Directory a target for attackers?
For attackers, Active Directory is the keeper of the crown jewels. When threat actors compromise a network, they typically try to elevate their privileges so they can move to more critical systems, access sensitive data, and gain a broader foothold in the environment to maintain persistence. As a result, attacking Active Directory and obtaining administrator-level access is one of the attackers’ chief goals.
What tools are used by Active Directory attackers?
Attacks are usually commenced by using tools such as BloodHound, which is an open-source application used for analyzing the security of Active Directory domains and revealing the potential for escalating access entitlements. Once the cyber attackers have uncovered hidden or complex attack paths that can potentially compromise the security of the network, they then use tools like Mimikatz to steal the necessary credentials.
How does Privileged Access Management help protect Active Directory?
The targeting of Active Directory by attackers makes Privileged Access Management (PAM) a vital part of enterprise security.
PAM tools fall into three categories:
- Privileged Account and Session Management (PASM)
- Privilege Elevation and Delegation Management (PEDM)
- and secrets management software
Ideally, these capabilities should be fully integrated into an underlying platform to avoid the silos that come from point solutions.
Is Active Directory a Privileged Access Management tool?
Active Directory, on its own, cannot be considered a PAM tool. While it enables administrators to manage permissions and control access to network resources, a comprehensive PAM strategy requires additional support.
However, with the right tool, it is possible to integrate Active Directory with privileged systems, which allows for the streamlining of access management within an organization. So, while Active Directory alone does not fulfill the role of a PAM tool, it can be combined with other tools to enhance PAM capabilities.
Tools that Privileged Access Management brings to protect Active Directory
With Privileged Access Management, organizations can use a suite of tools to provide an extra layer of protection for privileged accounts. These protections should be part of a layered approach to security that also involves continuous monitoring of Active Directory for suspicious activity.
Privileged Access Management tools include:
Session monitoring: Session monitoring for PAM helps organizations secure their systems and networks by providing visibility into user activities. It allows administrators to monitor, detect, and respond to suspicious activity associated with privileged accounts. Session monitoring provides an audit trail of all activities performed using privileged accounts.
Granular access controls: Granular access controls for PAM provides fine-grained control over which users have access to what resources. It allows administrators to set up different levels of permissions according to the sensitivity and importance of each resource, ensuring that only authorized personnel can make changes or view data.
Password vaulting: Within the context of enterprise IT and critical infrastructure, password vaulting refers to taking highly-privileged, administrative accounts and passwords out of the direct control of IT staff, and storing them securely in a software vault. The vault then controls who is allowed access, when, and for how long. This reduces the risk of such passwords being abused by internal or external threat actors.
The passwords are protected in the vault with access controlled via a role-based access control mechanism. The vault may include additional security features, such as scheduled password rotation and a workflow-based access request and approval mechanism to support a Just-in-Time access control model.
Other directory services on the market that provide similar functionality to Active Directory and attract cybercriminal attacks
IBM Red Hat Directory Server: IBM’s Red Hat Directory Server is a network-based registry that functions independently of operating systems, enabling administrators to store application and user identity data. Red Hat DS provides a centralized location for IT administrators to manage profiles and user credentials.
Apache Directory: ApacheDS™ is an extensible and embeddable directory server entirely written in Java. Apache directory has been certified LDAPv3 compatible by the Open Group.
Lightweight Directory Access Protocol: LDAP is a software protocol designed to allow individuals to easily locate information about various resources in a network, including organizations, individuals, files, and devices. It can be used on both public Internet and private intranet networks
LDAP is efficient and uses less code compared to other protocols. LDAP also functions as an Identity and Access Management (IAM) solution supporting Single Sign-On (SSO), Secure Sockets Layer (SSL), Kerberos, and Simple Authentication Security Layer (SASL).
More AD Resources:
Blogs
Active Directory Security and Hardening: An Ethical Hacker’s Guide to Reducing AD Risks
Securing Active Directory to Reduce Ransomware Attacks: A Quick Primer
AD Bridging: If you're only using it for authentication, you're missing a ton of value
How to Keep Active Directory Active in a Hybrid IT World
Protect Active Directory from Cyberattacks with Server PAM
Videos
Whitepapers
Active Directory Security and Hardening
Advanced Active Directory Bridging
Tools
Weak Password Finder Tool for Active Directory
Service Account Discovery Tool for Windows Active Directory
Product: Secret Server
Discover Local and Active Directory Privileged Accounts

FREE WHITEPAPER
Active Directory Security and Hardening