Identity security controls for cyber insurance
Challenge
Cyber insurers now demand proof of identity security maturity before issuing or renewing a policy.
Risk
Without demonstrable identity security controls, you risk delays, higher premiums, or outright denial of coverage.
Solution
When providers see you have the industry-leading identity security solution, they grant and renew policies faster.
Almost 70% of organizations currently invest in insurance, and just under 20% are considering cyber insurance to improve their cyber resilience. Whether you’re part of an organization that already has cyber insurance or contemplating investing, you should be prepared to show providers evidence of your identity security controls and their effectiveness.
Start by downloading our sample Cyber Insurance Readiness Checklist. It guides you through the top questions most insurance companies ask when you apply for cyber insurance.
Identity security solutions for cyber insurance
Control privileged access and manage enterprise passwords
Privileged Access Management (PAM) solutions, such as Delinea’s Secret Server, give you the ability to automatically discover, manage, protect, and audit privileged account access. With an industry-leading vault at the core of the platform, Delinea manages all types of secrets for human and machine identities, including domain administrators, application accounts, database accounts, third parties, and business users.
Reporting is also a crucial component of demonstrating compliance to insurers that want to see how well policies are followed. Secret Server’s out-of-the-box and customizable reporting features make reviews and audits painless.
Protect and govern server access
Cyber insurers expect to see multiple layers of control over how privileged access is used on servers, not just secure authentication. Delinea enforces MFA at server login and privilege elevation, applies least privilege policies to limit what users can do once connected, and manages just-in-time access requests for temporary privilege elevation. Every privileged session can be recorded and audited, giving you verifiable evidence of control and accountability, a key factor insurers evaluate when assessing cyber risk
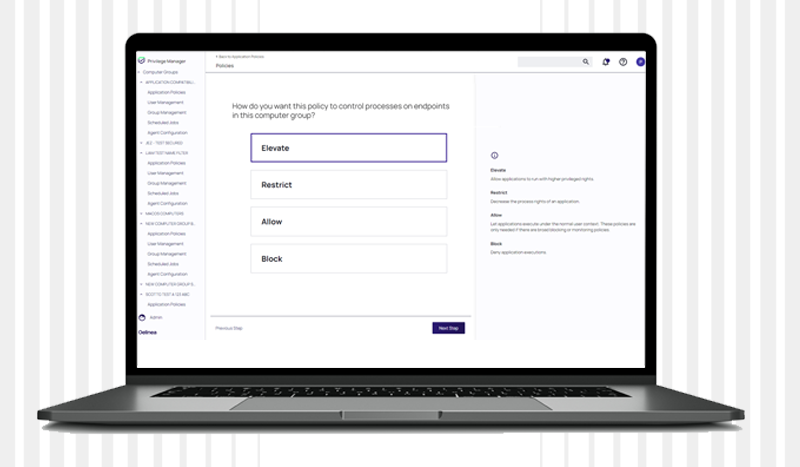
Manage workstation privileges with application control
Govern service accounts from start to finish

Identity Security Solutions for Cyber Insurance
See how Secret Server secures, identifies, manages, monitors, and audits your privileged account credentials and more.
Try an interactive demo
Explore key capabilities of Delinea Privilege Manager at your own pace.
Try an interactive demo
The 2025 Cyber Insurance Report by Delinea explores how identity maturity, AI adoption, and regulatory readiness are shaping insurability.
Download the toolkit