Identity Governance and Administration (IGA)
What is Identity Governance and Administration?
Identity Governance and Administration (IGA) combines Identity Governance and Identity Administration to reduce the risk of identity-based attacks. Below you’ll find a detailed definition of IGA and learn more about the ways IGA can help you reduce complexity and protect your organization.
Identity Governance refers to the policies and procedures that enable you to have oversight of all the identities in your organization (human and machine) as well as demonstrate that oversight to auditors, cyber insurance companies, and compliance bodies.
To govern identities in a secure way, you must align with security frameworks and best practices. That includes segregating duties and following the principle of least privilege, in which identities are given only the access and permissions to devices, servers, applications, and other IT resources they need to do their job.
Demonstrating identity governance requires you to document your processes and approvals—through certification or attestation—so you can provide that evidence to auditors.
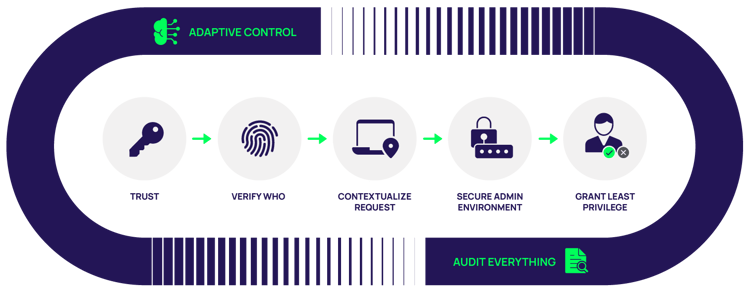
Above: Managing identities according to least privilege
The second aspect of IGA, Identity Administration, refers to the day-to-day management of identities in your organization. Typically, IT teams provision enterprise identities and associated credentials, assign access permissions and entitlements, and continually manage all these steps as business and technology requirements change. IGA solutions automate and orchestrate governance and administration to save time and effort and eliminate mistakes that happen through manual work.
What’s the difference between IGA and IAM?
You can consider IGA a subset of Identity and Access Management (IAM). It includes the policies and the tools that make the goal of IAM a reality. Gartner notes, “IGA differs from IAM in that it allows organizations to not only define and enforce IAM policy, but also connect IAM functions to meet audit and compliance requirements.”
Why does your organization need IGA?
Each person and each technology in your IT environment, including apps, databases, code, and devices, must have its own digital identity. Identity governance and administration can be extremely manual and time-consuming, especially as many organizations have several times the number of identities as they do employees.
IGA addresses the challenge of fragmented, unmanaged identities. For example, a single user may have one identity set up by their Active Directory, another for at-home work which they sometimes use to log into work-related applications, possibly another one provided by a cloud platform, etc.
Without an IGA solution, it’s nearly impossible to discover, manage, and audit all identities. IGA solutions ensure policies are followed consistently, even as your organization grows. IGA makes it easier to manage the entire identity lifecycle, from initial provisioning of an identity, to changes in roles, departments, and access, all the way to deprovisioning when someone leaves the organization.
What does cybersecurity like this cost? Not as much as you think
Key features of IGA solutions
IGA solutions have core features and capabilities, including:
- Provisioning – IGA solutions streamline the process of automated provisioning and de-provisioning access permissions throughout the identity lifecycle.
- Access request management and approvals – IGA solutions streamline the process to review and verify user access to applications and other IT systems. For example, manager or executive approval may be required to provide an elevated level of access.
- Entitlement management – IGA solutions specify and verify what users are allowed to do within systems once they have access.
- Attestation and certification – IGA solutions enable ongoing and/or periodic review processes to evaluate the risk associated with granting users access and confirm that access is appropriate. They surface information needed for reviewers to make informed, risk-based decisions about access, to avoid fatigue and rubber-stamping.
- Auditing, analytics, and reporting – IGA solutions provide visibility of user activities, identity unexpected behavior, and raise alarms for security teams. They generate audit logs and compile data for reports to demonstrate compliance.
Some things that separate the leading IGA solutions is their ability to integrate with many different types of IT environments, authentication methods, and technologies in your workflow. As your organization moves to the cloud, includes more third-party contractors, and adopts diverse applications, you’ll need an IGA solution that can easily scale.
Industry-leading IGA solutions include SailPoint and Okta. These modern IGA solutions are designed to bring together all types of identities, connecting to multiple, fragmented identity trees, so that they’re easier to manage in a central location. They support standards such as OAuth 2.0, OpenID Connect, SAML, SCIM, and REST.
The combination of IGA and Administration and Privileged Access Management
While IGA (and IAM for that matter) encompass all types of identities throughout your organization, PAM solutions focus on privileged identities – those identities that have elevated access to systems and sensitive data, such as domain administrators, root accounts, and other superusers.
To be most effective, IGA and PAM solutions work together. Delinea doesn’t offer IGA, but we’re tightly integrated with IGA partners such as Okta and SailPoint that provide this crucial solution. This integration allows IGA solutions to focus on identity governance and administration while Delina PAM uses role-based and context-driven policies to determine access for privileged users.

FREE WHITEPAPER
Take your Privileged Access Management to the Next Level
More Resources:
Meet Delinea’s IGA partners and explore IGA + PAM integrations.
You can learn more about how PAM and IGA work together by reading the Expert’s Guide to PAM.