Protect Active Directory from cyberattacks with Server PAM
A cyberattacker just breached your Active Directory. Is it game over? Not if you have the right privileged access controls in place.
Active Directory (AD) is a high-value target for cybercriminals to attain their nefarious goals. Many organizations still rely on on-premise AD, even though the adoption of Microsoft's cloud-based Azure AD is rapidly growing.
Delinea's Server PAM—Server Suite and Cloud Suite—impedes cyberattacker progress both on-prem and in the cloud, giving you a powerful defense against today's diverse array of cyberattacks.
How do attackers gain access to Active Directory?
An Active Directory attack typically starts with privileged credentials. Attackers favor legitimate credentials to fly under the radar. Posing as a trusted employee or third party, they can maximize dwell time - the time cybercriminals spend in your environment before being detected. The longer the dwell time, the more likely cybercriminals are to succeed in their effort to compromise your AD.
A standard route to obtaining user credentials is phishing. Sooner or later, a user will click on a link in an email, automatically installing malware on their workstation. If the user is logged in as a local administrator—a common practice, unfortunately—the malware runs with local administrator privileges, and the cybercriminal owns the workstation. Using familiar tools such as Mimikatz, elevating to full domain privileges can take as few as two steps for a cybercriminal.
After securing a workstation foothold, the attacker can move vertically from the workstation to a server. The attacker then jumps laterally from server to server to gain domain administrator or enterprise administrator access to AD. At this point, the cyberattacker has total control of AD.

Why is an Active Directory attack so dangerous?
If a cyberattacker breaches your AD deployment, they have compromised the trust fabric of your IT infrastructure. The attacker has complete control with these newly gained privileged domain entitlements.
The fallout is two-fold:
- The technical fallout: The cyberattacker can access and change any privileged AD user and computer account, security group, group policy, security policy, and trust relationship … the list goes on.
- The financial fallout: This affects your company's bottom line. The attacker can log in as anyone, even the CEO, and access ANY data on ANY domain-joined server, exfiltrate it, or destroy it all, including online backups. A smart cybercriminal plants back-doors to regain control after a restore.
Trying to recover from backups can be time-consuming and costly. It's only a matter of time (as dictated by the cyberattacker) before they execute their plan. The 2022 Verizon Data Breach Investigation Report tells us that financial gain remains the top motivator. You can count the minutes before your data appears for sale on the Dark Web or a ransomware note hits your desk.
Breaking the AD attack chain with PAM
In security, we refer to the cybercriminals' playbook as an attack chain. Privileged Access Management (PAM) solutions break that chain in several places, including workstations at the edge of our networks and AD domain controller servers inside.
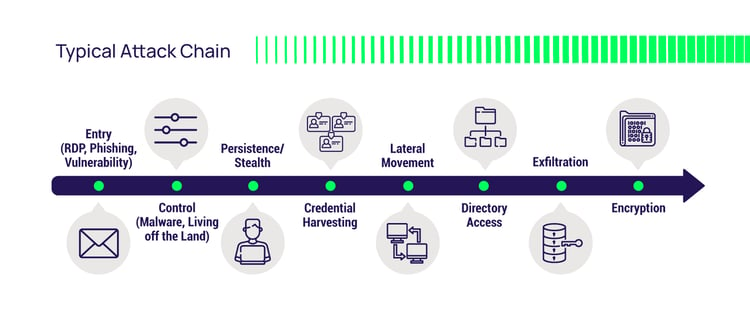
The native security on server operating systems doesn't go far enough to prevent AD compromise. Local and domain-shared privileged accounts and groups hamper best practices such as zero standing privileges and zero trust, resulting in over-privileged users and a bigger attack surface. Access control rules and policies are complicated and not sufficiently granular to align access and privilege to users' job functions.
Server PAM creates obstacles to an attacker's progress
Server PAM raises the bar on user validation, authentication, authorization, and auditing. It throws extra hurdles in the cybercriminals' path, forcing them to change course. Doing so wastes their time and generates more noise, reducing dwell time and triggering alarms.
 An ideal outcome is when they give up and move on to the next victim, and you learn from their tactics and what PAM controls were successful.
An ideal outcome is when they give up and move on to the next victim, and you learn from their tactics and what PAM controls were successful.
Here’s how Server PAM works:
Validating login
Just because an actor presents a legitimate ID and password doesn't mean the actor is the credential's legitimate owner, is allowed to log in to this specific server, or if there even is a human at the keyboard. Server PAM validates credentials against several on-prem and cloud identity providers such as AD, OpenLDAP, Ping, Azure AD, and Okta. PAM policies dictate permission to log in, and MFA policies help assure identity.
Denying unauthorized access on login and privilege elevation
With Server PAM, the user must prove legitimate ownership of the presented credential with a second factor. Multi-Factor Authentication (MFA) stops bots and malware and forces human adversaries to change tactics. Phishing-resistant MFA, such as a FIDO2 authenticator, is another layer of protection for sensitive assets.
Preventing lateral movement by enforcing least privilege for all admins
Combined with a vault, Server PAM removes shared privileged accounts from general circulation to prevent them from falling into the wrong hands. This combination reduces your attack surface, lessens the fallout from compromised accounts, and forces the attacker to work harder. Admins use an individual account to log in and elevate privileges, just in time. To further mitigate risk, consider implementing "alternate admin accounts" or "dash-a" accounts for administrative access.
Requesting elevated rights
Server PAM requires an explicit access request accompanied by context, such as a help desk ticket number, for sensitive systems. The approver can grant the request or deny it and alert the security team to investigate a potential attack in progress.
Just-in-Time access and Zero Standing Privileges (ZSP)
Server PAM eliminates as many shared privileged accounts as possible, vaulting the rest and using ephemeral accounts and tokens to reduce standing privilege. Enforcing least privilege with Just-in-Time access request workflows ensures rights are temporarily granted to legitimate users only when needed.
Augmenting static access control rules with behavioral analytics to spot an attack in progress. Static rules rely on human care and feeding. They are often stale and result in gaps. Machine learning and analytics can spot behavioral differences between an attacker and the legitimate owner of the credential.
Auditing and session recording
When investigating an incident, time is of the essence. Forensic-level auditing and session recording speed root cause analysis. Coupled with the behavioral analytics described above, it gives you the time necessary to prevent an incident from becoming a breach.
Take a look at this short demo of Server PAM in action:
See how Delinea PAM Can Help You Protect AD
Delinea Cloud Suite and Server Suite block cybercriminal efforts to escalate privilege, move laterally, and compromise your Active Directory. They help you gain deeper visibility into privileged activity and enforce least privilege and risk-based MFA to react quickly to abnormal behavior in real time and break the attack chain.
To learn more about how Delinea Server PAM can help you keep bad actors away from Active Directory, request a Server Suite trial or Cloud Suite trial today.
Privileged Access Management Software for Servers
Also, for additional insights, please check out the following:
Gartner whitepaper: Reduce Risk Through a Just-in-Time Approach to Privileged Access Management
Privileged User Activity Auditing: The missing link for enterprise compliance and security
Privileged Access Management Maturity Model: Step-by-step roadmap for your PAM journey