Secret Server Feature: SESSION Control
Record & Monitor Privileged Session Access, and Log Keystrokes
Maintain a full audit trail for your critical systems by recording remote sessions with Secret Server.
What’s the challenge?
Knowing who logged into your system with an administrator credential is simply not good enough. You need a complete record of the user’s activity as well, either as a backstop to change control to ensure no unauthorized changes were made, or to meet compliance requirements.
Why it’s important
If someone adds a backdoor account or makes an unauthorized configuration change, you must be able to identify who accessed the system, quickly review what they did and react accordingly.
How Secret Server's features solve it
Secret Server’s Session Monitoring and Recording add-on pack comes with three great features: Session Monitoring, Session Recording, and Keystroke Logging.
TRY IT FREE FOR 30 DAYS. It’s fast to install and easy to use!
Start your free trial of Secret Server using the trial form.
Or, check out our Chart of Secret Server’s user-friendly features.
Session Monitoring
Administrators have a real-time view of all privileged user sessions launched from Secret Server and can watch the live feed of an active session. You can quickly terminate risky or unauthorized sessions, or send a message directly to the user. Secret Server’s Session Monitoring feature works with Remote Desktop, PuTTY, and custom launchers.
This feature provides a powerful tool for monitoring privileged sessions. For example, an administrator is alerted of a new active session initiated on a critical SQL database server, they view the active SQL Management Studio privileged session, send a message to the user asking why they are accessing the database, and terminate the session if deemed necessary.
Session Recording
Recording privileged sessions results in an end-to-end record of a user’s privileged access. Secret Server provides an audit trail from when the user checked out a secret, to what they did on the system, to when they logged off.
By locking down privileged credentials with per-use password changes and access approval as well as controlling access to the endpoint through Secret Server’s proxy, you ensure that Secret Server brokers all privileged sessions. Users are then required to go through Secret Server to access sensitive systems, such as Domain Controllers, or highly regulated environments such as PCI or SOC-2 scoped networks.
Keystroke Logging
All keystrokes during sessions can also be recorded and available for quickly searching during the playback sessions. This keystroke logging provides the ability to rapidly search for administrative commands, such as sudo on SSH sessions, which may be important for your auditors to review.
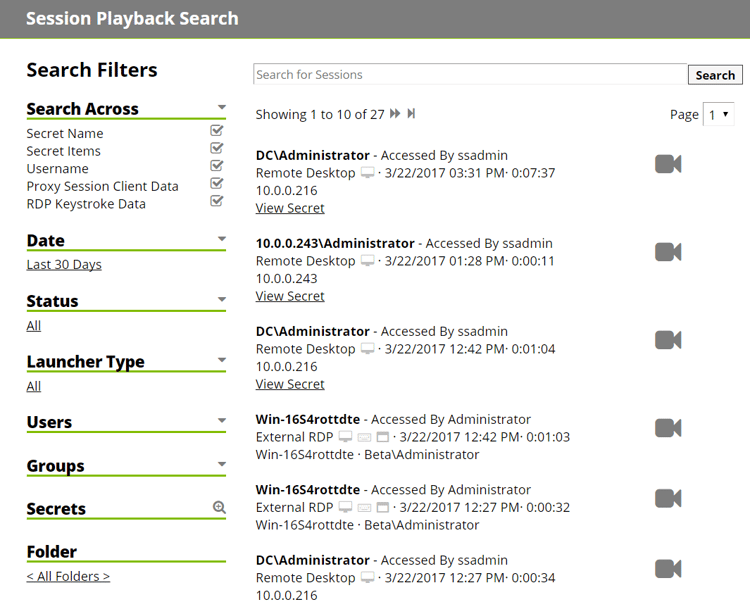
Quickly Find Recorded Sessions
Enhanced Session Playback
With Secret Server, administrators can quickly search for the exact session they want to review using a number of different filters as well as a cross-session search bar to quickly find the session they need, such as all sessions that had PowerShell running.
Once the session they would like to review has been found, they can open the recording in our enhanced web player. This player provides a lot of additional information and context to the administrator such as: an activity heat map, list of processes that ran, keystrokes, and meta data on the session itself.
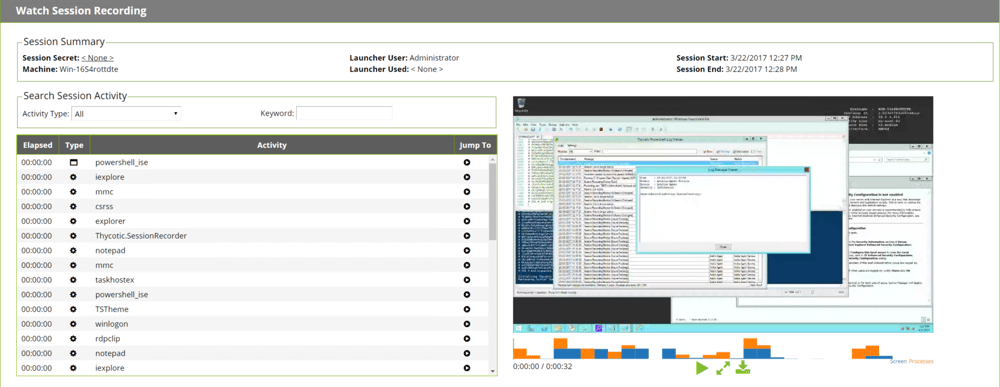
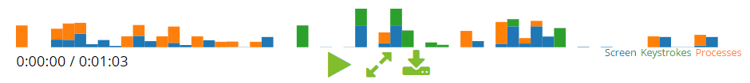
The Activity Heatmap on each session provides the process, screen, and keystroke activity across the entire session. Reviewers can use this quickly to pinpoint moments of activity that they would like to review during the entire session.
2 Minute Demo: Session Monitoring
Additional Information
Session Recording provides video playback of RDP, SSH, and custom applications. SSH sessions also log all traffic for text-based searching and analysis when combined with the SSH Proxy. Once a session is recorded it can be stored on disk and archived based on your company’s retention policy.
Session recording is built into Secret Server, so when you’re ready to turn it on be sure you have a video codec installed for performing the video processing. It’s also part of the session launcher that admins are already using to automatically open remote connections. As it doesn’t require complex configuration or additional deployments it’s fast and simple to roll out to meet audit controls or internal security mandates.
Many organizations choose to use Session Recording in conjunction with SIEM correlation or analytics to alert the SOC team on potential abuse or breaches. Secret Server can be configured to export events via syslog to enrich network logon information with the actual user. So when an alert is generated you know which recorded sessions are relevant.