Security as a Service (SaaS / SECaaS)
What is Security as a Service?
Security as a service is the business model in which organizations work with external partners—either cybersecurity vendors or IT outsourcers—to manage or automate their security operations. The products offered by SECaaS vendors are usually cloud-based and sold on a subscription basis. In the SECaaS model, vendors take responsibility for managing and maintaining cloud products. This is one of the major advantages for businesses adopting the model.
Examples of security as a service
Cloud Security Alliance (CSA), which promotes the use of best practices for providing security within cloud computing, defines the following categories, or examples, of SECaaS:
- Business Continuity and Disaster Recovery
- Continuous Monitoring
- Data Loss Prevention
- Email Security
- Encryption
- Identity and Access Management (IAM)
- Intrusion Management
- Network Security
- Security Assessments
- Security Information and Event Management
- Vulnerability Scanning
- Web Security
The pros and cons of SECaaS
 Pros of SECaaS
Pros of SECaaS
Why should companies adopt SECaaS?
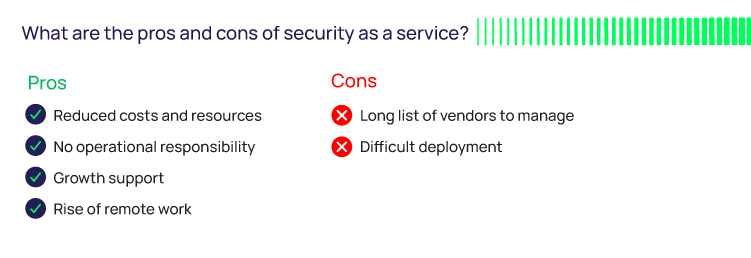
Reduced costs and resources
In order to run security operations via an internal team, companies need to hire people with certain skills who will be able to do the job. IT leaders might find themselves involved in a lengthy recruitment process. Filling the positions and then paying salaries might constitute a significant cost. Furthermore, the departure of IT professionals might affect the ease of running operations.
It's much more cost-effective to use your IT budget on cloud-based solutions that will handle routine tasks like reporting or monitoring, leaving IT leaders more time for strategic tasks.
No operational responsibility
In a scenario when companies prefer to handle security operations in-house, IT teams take responsibility for maintaining the infrastructure, running the updates, having a disaster recovery in place, and organizing day-to-day operations.
However, when IT teams don’t have sufficient resources or budget and want to outsource operational responsibility, these tasks can be offered as SECaaS by cybersecurity vendors. Then, the vendors are the ones who are responsible for maintaining the systems and making sure services are running smoothly 24/7.
Growth support
When a company experiences rapid growth, expands to other markets, or is involved in M&A, IT systems will be required to add new users and servers, and expand the system. This is challenging for teams that are lacking resources to meet the demand.
With cloud-based solutions, companies can scale up rapidly.
Rise of remote work
In a study published by Delinea last year, half of IT decision-makers' companies had to accelerate their cloud migration plans (48%) and IT modernization overall (49%) during the COVID-19 pandemic. The top two modernization priorities for the next 12 months are maintaining flexibility/security for remote work (38%) and digitizing more processes using cloud-native services (36%).
View the survey results in an interactive chart: https://charts.censuswide.com/CW6934/CW6934_VIbox.html
With the rapid shift to remote work, IT teams are required to enable remote workers to safely access the systems and secure the endpoints. With cloud-based solutions, admins can easily track, monitor, and manage access of their remote workers.
Cons of SECaaS
Long list of vendors to manage
As per the CSA category list, in order to secure various different elements of the system, companies need to work with many vendors. There is significant time required to properly evaluate and enter the integration process which, on occasion, can be lengthy. Once selected and integrated, it is usually difficult to switch to a different SECaaS provider. Therefore, IT leaders need to perform extensive due diligence on the products and vendors and select those that offer quick deployment and are clear about the pricing.
Difficult deployment
Even though a SECaaS vendor may have promised easy deployment and a full, cloud-based solution, later in the process they might require organizations to hire people who will be running and maintaining the solution. Again, the buyers must carry out the necessary research to avoid being trapped in a long deployment process.
Can PAM be delivered as security as a service?
As per the categorization of CSA, PAM solutions can cover the Identity and Access Management (IAM) category of SECaaS. Organizations can give over the responsibility to maintain, update and support privilege access management to the PAM vendor.
The majority of PAM products are hosted on cloud and offered as a subscription which enables vendors to deploy updates regularly and helps companies to scale up faster.
A growing number of vendors are migrating their PAM products into platforms so organizations can tailor solutions even closer to their needs.
PAM in the Cloud. Powerful. Secure.
How does Delinea deliver security as a service?
When selecting Delinea as your company’s SECaaS provider, you can choose to store basic data and secrets in one of our global data centers located in either the US, UK, Germany or Singapore. Data is fully encrypted at rest and in transit.
Delinea can automate the security needs of your organization by securing access and establishing privileges through the entire security environment from workstations, applications, servers, and virtual servers, to service accounts.
Solutions like Privilege Manager or Connection Manager ensure that your remote connections are safe, and you have full control and monitoring of them.
Migrating from on-prem to cloud doesn’t mean losing product functionality. When it comes to Delinea Secret Server, our cloud version gives 100% feature parity.
Delinea’s CMO, Chris Smith, discusses this in detail here:
Privileged Access Management: The Great Cloud Migration
Server PAM, which is a platform for managing privileged access in a multi-cloud infrastructure, is one of the solutions that enforce further migration into the cloud trend. Server PAM allows organizations to manage privileged access globally through centrally managed policies enforced on the server across Windows and Linux workloads.
Related Resources
Blog Posts:
5 Reasons why you need a modern PAM Solution built for the Cloud
Protect Active Directory from Cyberattacks with Server PAM

FREE EBOOK
Increased cloud adoption poses greater security risks to your IT and business users