Intelligently automate access provisioning
Identity Lifecycle Management
Securely manage joiner-mover-leaver processes based on identity attributes and risk context.
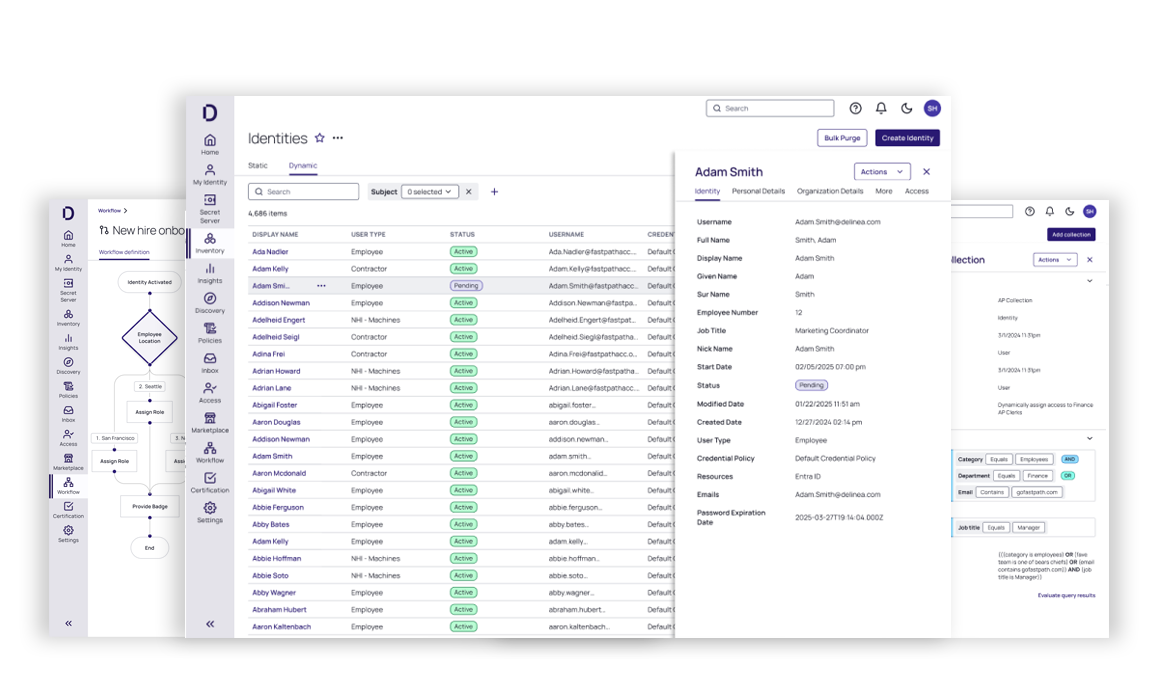
Streamline identity lifecycle management for human and non-human identities across your organization
Automate joiner-mover-leaver events
Efficiently build digital identities and provision access during onboarding. Adjust or remove access when users change roles or leave the organization.
Enhance security and compliance
Delivered on the cloud-native Delinea Platform, you can leverage real-time identity and access context to proactively identify risk, intelligently apply policies, and automatically provision or revoke access.
Easily configure workflows
Design and automate identity lifecycle events using an intuitive, no-code, drag-and-drop interface, eliminating the need for custom coding.
Provision access
When a new user joins the organization, efficiently build digital identities and automatically provision access during onboarding.
Proactively detect risk
Perform in-depth analysis of user access rights for self-service access requests to assess risk before access is provisioned.
Enforce least privilege access
When a user’s role changes, provision access for new systems and remove unnecessary access.
Automate access removal
When a user leaves the organization, automatically revoke access and validate with documented reporting.
Unify administration
Deliver fast time-to-value and lower total cost of ownership with comprehensive governance of identities and access in the cloud-native Delinea Platform.
Securely manage joiner-mover-leaver processes
Identity Lifecycle Management more easily and intelligently automates access management, reducing risk from overprovisioned and orphaned accounts. Integrate with your technology investment and leverage access policies for centralized, unified control and oversight across all identities.

Request Information

Making Identity Work: Ensure a Successful Identity Project for Risk Management
Learn how a fast, easy to set up solution can help build a strong Identity and Access Risk Management Strategy in your organization

Managing the identity lifecycle of Joiners, Movers, and Leavers (JML) is the backbone to strong identity security
Learn the importance of managing identity lifecycle events using best practices and Identity Governance and Administration (IGA) solutions to ensure secure and efficient access management.