Break glass privileged accounts for disaster recovery
There’s been a system outage and systems have slowed to a crawl. It’s the Friday night before a long weekend and your domain administrator is on vacation. Now what do you do?
It’s time to break the glass.
In this post, you’ll learn about the break glass process, including what it is, how to set it up, and how it impacts your cyber resilience. You’ll also see how you can reduce the risk of downtime or disruption in privileged access, even in emergency situations.
What does break glass mean?
"Break glass" accounts, or emergency access accounts, are reserved for urgent situations where standard access is compromised, such as during a system outage, cyberattack, or system failure.
These accounts grant immediate privileged access to IT systems for troubleshooting and are a key part of incident response plans, ensuring swift recovery and business continuity. They are not for regular use but are critical for emergency scenarios.
When would you use a break glass account?
The break glass example above is one scenario in which this special emergency account would be useful. In addition, you could face scenarios in which your password vault or Privileged Access Management (PAM) solution is compromised, or Multi-Factor Authentication (MFA) may not be working properly, or unavailable.
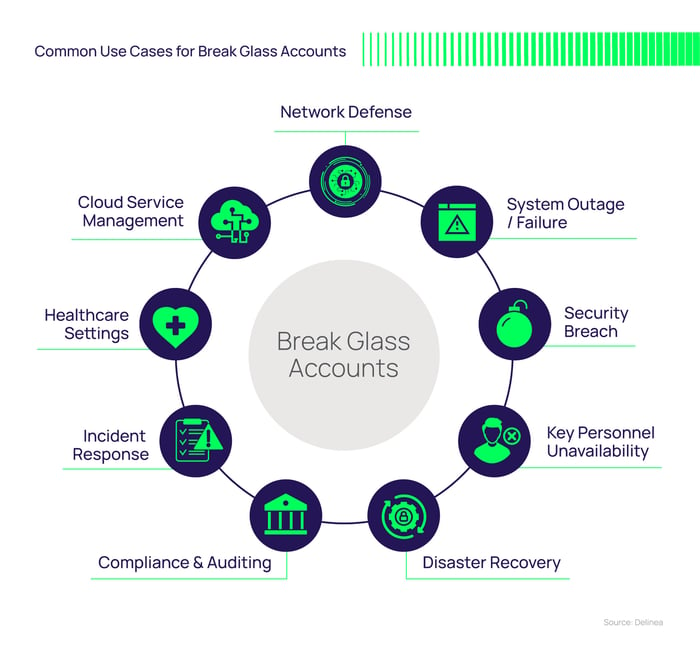 Common use cases for break glass accounts:
Common use cases for break glass accounts:
1. System Outage / Failure:
In the event of a system outage or failure where regular access mechanisms such as login credentials or authentication systems are not functioning, break glass accounts can be used to gain access to critical systems for troubleshooting and recovery purposes.
2. Security Breach:
If there is a security breach or suspected unauthorized access to systems, break glass accounts may be utilized to investigate the incident, assess the damage, and implement necessary security measures.
3. Key Personnel Unavailability:
During situations where key personnel with administrative privileges are unavailable due to unforeseen circumstances such as illness, injury, or incapacitation, break glass accounts can be accessed by designated individuals to ensure business continuity and system maintenance.
4. Disaster Recovery:
In the aftermath of a natural disaster, cyber-attack, or other catastrophic events that disrupt normal operations, break glass accounts may be employed to restore critical services and data, enabling organizations to recover from the disaster more quickly.
5. Compliance and Auditing:
Break glass accounts are sometimes used for compliance purposes to meet regulatory requirements or audit standards. These accounts are typically monitored and audited closely to ensure they are only accessed in authorized emergency situations.
6. Incident Response:
During incident response activities such as investigating security incidents, containing threats, and mitigating vulnerabilities, break glass accounts may be activated to facilitate rapid response and resolution of the incident.
Here's the framework for structured incident response: Incident response lifecycle for identity-related attacks
7. Healthcare Settings:
In healthcare environments, break glass accounts are often used to access electronic health records (EHRs) in emergency medical situations where immediate access to patient information is crucial for providing timely and effective care.
8. Cloud Service Management:
During a DDoS attack targeting cloud services, normal access to cloud management consoles may be disrupted or degraded. Break glass accounts can be used to access cloud management platforms provided by vendors such as Amazon Web Services (AWS), Microsoft Azure, or Google Cloud Platform (GCP). With access to these consoles, authorized personnel can scale up resources, adjust network configurations, and activate DDoS protection services offered by the cloud provider.
9. Network Defense:
During a DDoS attack, normal access to network infrastructure and security systems may become unavailable or severely degraded due to the overwhelming volume of malicious traffic. Break glass accounts can provide authorized personnel with alternative access to network devices, firewalls, and intrusion detection/prevention systems to implement defensive measures and mitigate the impact of the attack.
It's important to note that break glass accounts should be implemented with strict controls and safeguards to prevent misuse and unauthorized access. Access to these accounts should be limited to authorized personnel only, and proper logging and auditing mechanisms should be in place to track usage and ensure accountability.
In industries like healthcare, transportation, critical infrastructure, or defense, getting locked out of privileged accounts could put lives at risk.
Managing break glass accounts
Break glass accounts are extremely powerful. They provide access rights well beyond the typical privilege elevation scenario. For that reason, it’s essential that you use them sparingly, maintain control of their use, and can explain exactly how they were used during an emergency situation.
Make sure you implement best practices for oversight and accountability of break glass accounts.
For example:
- Restrict the use of break glass accounts to a small set of highly trusted users.
- Limit break glass access for a limited period.
- Closely monitor the use of break glass accounts, including recording privileged user behavior, for follow-up forensics and auditing.
- Document the requirements of break glass accounts as part of your cybersecurity policy.
- Test the use of break glass accounts as part of your incident response plan.
- After a break glass account is used, disable or delete it so it can’t be discovered or repurposed.
How do you set up a break glass account with Delinea PAM?
Privileged Access Management solutions like Delinea Secret Server are designed to support break glass scenarios.
When Delinea customers need emergency access to a Secret, they can run Secret Server in Unlimited Administrator mode. In this mode, an administrator can access all secrets and folders without explicit permission.
By using Role-Based Access Control (RBAC), this mode can be set up so that two people must agree before the feature can be used. Unlimited Administrator mode is audited within Secret Server, and an automatic email alert can be sent whenever it is accessed.
Avoid a single point of failure
In addition to break glass processes, there are numerous ways to build resilience into your Privileged Access Management strategy.
Modern, flexible PAM solutions are built for high availability. For example, Delinea Secret Server uses multiple servers in a clustered environment, providing automatic failover to a separate web server with no downtime. You can also configure database mirroring for a real-time backup of all stored data. Secret Server supports SQL replication through the Georeplication module.
Secret Server allows you to replicate secret data to another instance, either on-prem or cloud, with automated syncing across instances. You’ll have continuous access to secrets, even during an emergency incident.