The all-encompassing guide to cyber resilience
What is cyber resilience?
Cyber resilience refers to a company’s ability to endure and recover from cyberattacks. By improving resiliency, businesses have a better chance of withstanding sophisticated attacks—including ransomware, distributed denial of service (DDoS), and social engineering attacks—and avoiding extensive downtime and data loss.
With cybercrime accelerating at an alarming rate, it’s impossible to overstate the importance of cyber resilience. In a recent survey, 91% of businesses said that they experienced at least one cyber incident over the last year. What’s more, 51% of respondents said they suffered moderate or significant consequences like financial loss, business disruptions, reputational harm, and regulatory penalties from those incidents.

This increase in attacks is due to two main factors:
- Companies today have growing attack surfaces due to the rising number of devices, cloud services, and networks they use; the attack surface only gets bigger when teams are distributed.
- Cybercriminals are also becoming increasingly savvy and using advanced tools, including artificial intelligence, to build campaigns and penetrate defenses. Rather than thinking they can keep bad actors at bay forever, businesses are shifting their focus to containment and recovery.
Keep reading to learn more about the importance of cyber resilience, practical strategies you can use to improve your overall security readiness and increase business alignment, and how comprehensive cyber insurance can transfer your cyber risk.
The goal of cyber resilience is to maintain the delivery of intended outcomes despite challenges or crises
A cyber resilience strategy includes measures for detecting and responding to cyberattacks to minimize damage and data loss. At a high level, cyber resilience involves optimizing security tools and processes, ensuring business continuity, and implementing risk management policies. The goal is to maintain the delivery of intended outcomes despite challenges or crises.
For example, a business with strong cyber resilience may create and maintain data backups, train employees on cybersecurity best practices, and use real-time monitoring to detect incidents as they occur. The business may also diversify its data center infrastructure and run incoming network traffic through third-party services to prevent DDoS attacks. Simply put, combining security technologies and methodologies leads to better planning and responsiveness.
Cyber resilience vs. cybersecurity: What’s the difference?
Cyber resilience and cybersecurity have the same objective: to protect the organization from threat actors. But while cyber resilience focuses on preparing for and responding to cyber incidents, cybersecurity mainly focuses on awareness and prevention.
Cyber resilience
Cyber resilience concerns an organization’s ability to continue operating effectively during and after a cyber incident. It involves cybersecurity measures, incident response planning, and business continuity planning.
- Combines threat protection resilience practices
- Streamlines incident management and response
- Prioritizes adaptability, recoverability, and durability
Cybersecurity
Cybersecurity focuses on protecting systems, networks, and devices from unauthorized access, theft, damage, and disruption. It requires integrating multiple security systems to build an active, layered defense environment.
- Reduces exposure to internal and external cyber threats
- Combines technologies and frameworks like threat intelligence, vulnerability scanning, Endpoint Detection and Management (EDM), and Privileged Access Management (PAM)
- Involves quarterly risk assessments and planning
As you can see, cyber resilience and cybersecurity are related but distinct concepts. In other words, cyber resilience is NOT a replacement for cybersecurity and vice versa. Instead, the two concepts work hand-in-hand. By prioritizing cybersecurity, you can ultimately become more resilient and more effective in your remediation efforts.
Cyber resilience and disaster recovery
Cyber resilience and disaster recovery both reflect an organization’s ability to endure disruptions and maintain business continuity. The main difference is disaster recovery encompasses a much broader range of threats—including natural disasters like hurricanes, power outages, connectivity loss, and IT failure.
In today’s digital age, cyber resilience is now a fundamental component of disaster recovery with businesses becoming increasingly connected and data-driven. Achieving cyber resilience is critical for avoiding downtime and data loss—and being able to continue operating and serving customers. Disaster recovery planning must therefore include conducting data assessments, implementing cloud recovery tools, and encrypting backup data.
Benefits of cyber resilience
Organizations that avoid or delay cyber reliance planning risk suffering catastrophic security incidents. The threat is especially apparent in operational technology (OT) environments where hardware and software interact with the physical world and support public services and infrastructure. In fact, Gartner predicts that by 2025, threat actors will weaponize OT environments and successfully harm humans.
With cybercrime worsening, cyber reliance is now a fundamental business need—something that companies can’t afford to ignore. By building a comprehensive cyber reliance strategy, you can enjoy a number of significant benefits, which we’ll examine in this next section.
1. Minimize financial loss
According to IBM, the average data breach cost for businesses with fewer than 500 employees is up to $2.98 million. However, the cost of a cyberattack can be much higher when factoring in productivity loss, legal complications, and remediation expenses; IBM’s 2022 Cost of a Data Breach Report says that the average breach sets U.S. businesses back $9.44 million.
By having a robust cyber resilience plan in place, the financial impact of cyber incidents is minimized since sensitive files, systems, user accounts, and applications are protected, and the organization is able to recover quickly and get back to business as usual.
2. Increase uptime and availability
Cybersecurity incidents can disrupt internal business operations, productivity, and communications. They often lead to lengthy outages that last several hours or days. With a solid cyber resilience strategy in place, organizations can ensure a business continues humming along during and after a cyber incident—minimizing downtime and avoiding service delays.
3. Avoid regulatory penalties
Companies face an ever-growing list of cybersecurity regulations and frameworks. In some cases, penalties and fines can be substantial. For example, the European Union’s General Data Protection Regulation carries maximum fines of about $22 million or 4% of a company’s annual turnover, whichever is greater.
Prioritizing cyber resiliency streamlines compliance with various security policies. This leads to better decision-making and helps team members move with greater speed and accuracy when responding to incidents.
4. Gain customer trust
In an age of high-profile data breaches, cybersecurity is now a key part of the customer experience. Customers increasingly want to work with organizations that protect their personal information and avoid service outages. As such, businesses have a great opportunity to use cybersecurity as a differentiating factor—gaining customer trust and building loyalty.
How does cyber resilience enable enterprise resilience?
Enterprise resilience refers to an organization’s capacity to account for and react to change. As PwC explains, enterprise resilience is necessary for surviving and evolving.
Cyber resilience enables enterprise resilience by allowing an organization to continue operating and transforming during times of crisis. In other words, when leaders are confident in security, the company is free to continue focusing on growth goals—like digital transformation and automation—without having to shift priorities and budgets.
Cyber resilience is especially important due to the current IT talent shortage. IT executives presently see the talent shortage as the most significant adoption barrier to 64% of emerging technologies. Gartner also predicts that a lack of talent will contribute to more than half of all significant cyber incidents by 2025.
By focusing on cyber resilience, IT leaders can build safe and efficient operating environments that talented, hard-to-find employees want to work in. As a result, employee stress and burnout decreases, and employee retention and engagement improves.

Take your Privileged Access Management to the Next Level
How does cyber resilience support digital transformation?
Most organizations today are integrating digital technologies to improve culture, processes, and employee experiences. But digital transformation also exposes businesses to greater risk. According to PwC’s Global Economic Crime and Fraud Survey 2022, four in 10 organizations link internal fraud incidents to the digital platforms they rely on.
Cyber resilience supports digital transformation by allowing organizations to innovate with greater speed, confidence, and security. This is because cyber resilience entails identifying potential threats, assessing their impact, and forming concrete actions to address them.
Challenges to achieving cyber resilience
Despite the growing need for comprehensive threat protection, many businesses are struggling to achieve cyber resilience for many reasons, which we’ll cover in the next section.
1. Limited visibility
To become cyber resilient, businesses need real-time visibility across all IT assets and critical infrastructure. However, silos often exist between teams, data storage systems, and applications. This leads to visibility gaps, which make it hard to identify emerging threats and vulnerabilities.
2. Poor understanding of security controls
The threat landscape is constantly evolving with cybercriminals adjusting their tactics and procedures to evade defenses. This often leaves cybersecurity teams questioning the effectiveness of their existing controls and struggling to keep pace with attacker methods. As a result, many security leaders lack confidence in their ability to protect their organizations from cyberattacks.
3. Lack of automation
Most businesses are still in the early stages of using cybersecurity automation to detect incoming attacks. Companies that still rely on manual risk identification and mitigation processes tend to respond to information slower and less effectively than teams using automated platforms.
They also are more likely to make mistakes, such as misconfigurations, and forget important security processes, such as removing privileged access or changing passwords after an employee or contractor leaves.
4. Legacy systems and applications
Not all businesses are up to speed with the latest and greatest systems and applications; many organizations still rely on a slew of legacy systems and applications. Unfortunately, older systems and applications can pose security risks as they may no longer receive security updates and patches.
While updating systems and applying updates and patches are best practices, those types of operational maintenance activities often require advance scheduling or force a shutdown, which often means they are delayed—not great for cyber resilience.
5. Insider risks
Security teams often focus on protecting their assets from external threats. However, insider threats—like rogue employees—pose a major problem, too. In fact, according to one expert, 66% of all cyberattacks involve an insider. To achieve cyber resilience, security teams must require authentication, continuous validation, and session monitoring when granting people privileged access to applications and data.
Best practices for improving cyber resilience
Every organization is different, with unique operating environments, users, data, and devices. As a result, there isn’t any single solution for ensuring cyber resilience. That said, there are multiple cyber resilience frameworks that provide high-level guidance.
What is a cyber resilience framework?
A cyber resilience framework is a strategy that helps organizations prepare for incoming cyberattacks and protect infrastructure, data, and information systems. There is more than one model for a framework—it is recommended that organizations explore frameworks that best suit their cybersecurity needs. For example, the National Institute of Standards and Technology (NIST) offers a helpful cyber resiliency engineering framework for building secure IT systems. Additionally, there’s a cyber resilience model that the UK’s IT Governance recommends.
Here is Delinea's suggested framework:
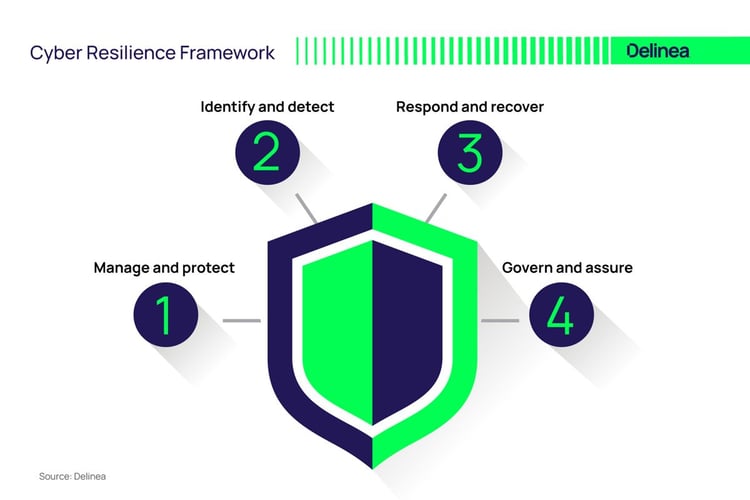
These frameworks include recommendations covering high-level aspects of cyber resilience throughout the cybersecurity lifecycle:
1. Manage and protect
The first step to creating a cyber resilience framework is to identify high-value assets and their associated risks. The main goal here is to target areas for improvement through audits and testing.
2. Identify and detect
Next, close the gap on cyber risk by developing controls based on unique requirements, risk profiles, and business environments.
3. Respond and recover
The third step is to perform under pressure and demonstrate agility during incident response. This way, you can successfully recover and restore operations following an incident.
4. Govern and assure
Finally, you need to engage and align executives and stakeholders with your cyber resilience strategy. This helps to collect feedback, discuss best practices, and eliminate confusion.
What are the steps to cyber resilience?
Becoming cyber resilient isn’t an overnight process. It requires a companywide shift in strategy and an ongoing commitment from all internal stakeholders. With that in mind, here’s a step-by-step process you can use to achieve cyber resilience.
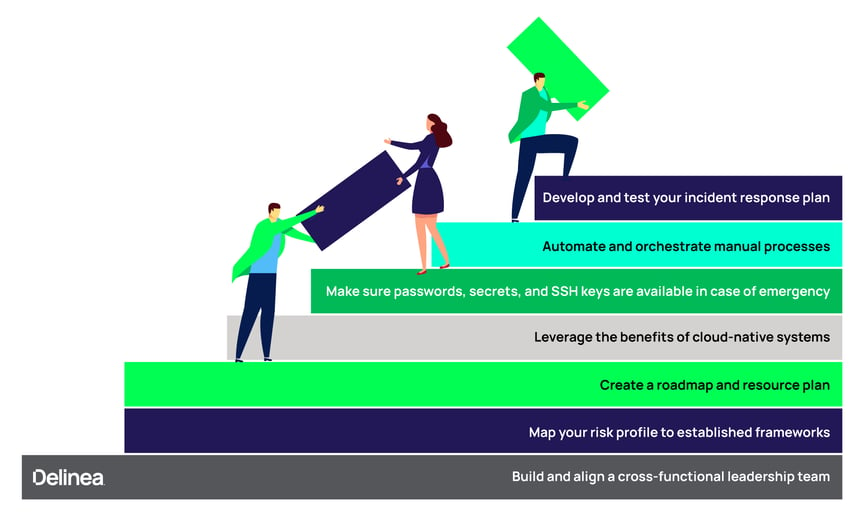
1. Build and align a cross-functional leadership team
Companies need to abandon the idea that the security team alone can keep them safe from cyber threats. Being cyber resilient means engaging your entire organization in the importance of security and data protection. The key is building a strong cybersecurity culture—one where all users are aware of how their actions impact the organization.
To kick off the process, create a cross-functional leadership team to oversee cybersecurity planning and response. This may include security leaders, C-level executives, engineers, developers, data management, security operations, IT operations, and incident response teams.
2. Map your risk profile to established frameworks
When building a cyber resilience strategy, it’s necessary to align best-in-class cybersecurity frameworks like NIST, CISA and other regulatory and compliance requirements, while still developing a plan that meets your organization’s unique requirements.
3. Create a roadmap and resource plan
Once your team is in place, you can then craft your cyber resilience strategy using the above cyber resilience framework as a guide. For the best results, cyber resilience should align closely with your organization's overall business objectives. Set a realistic goal for your future state and regular milestones to reach that goal.
Maximize value. Cybersecurity analysts and operations teams spend most of their time responding to trouble tickets instead of performing high-value work. This wastes valuable insights and prevents organizations from leveraging their talent to the best of their abilities.
If resources are scarce, security leaders must direct them where they will provide the most value—like forensics and incident response. Not only does this help organizations leverage their assets most effectively, but it can also potentially improve engagement and reduce turnover. Companies that lack internal support can also consider outsourcing security operations to a third-party managed security services provider (MSSP).
4. Leverage the benefits of cloud-native systems
Cloud-native systems allow for the rapid scaling up and down of resources, including security resources. This means that organizations can quickly respond to changes in demand, and allocate resources where they are needed most. This also helps to reduce the attack surface, as resources can be easily scaled down when they are not needed.
Cloud-native systems are designed to be resilient to failures, including security failures. They often include features such as automatic failover, backup and recovery, and data replication, which help to ensure that data and applications remain available and secure even in the event of a security incident.
While the cloud can improve cyber resilience exponentially, it also requires careful access management and monitoring. During cyber resilience planning, you should pay special attention to any sensitive data sitting in cloud systems. Vulnerability scanning and penetration testing can help to identify cloud vulnerabilities and potential misconfigurations that can lead to data breaches. It’s also necessary to review cloud access control policies and ensure only authorized users can access cloud resources, detect vulnerabilities in cloud applications, and safeguard data.
5. Make sure passwords, secrets, and SSH keys are available in case of emergency
Imagine a data center or cloud platform housing your enterprise password vault is inaccessible due to a cyberattack. Your team wouldn’t be able to gain privileged access to any resources that require secrets to be checked out of the vault, incapacitating your organization. That’s why advanced PAM tools like Delinea Secret Server include features for disaster recovery and break-glass scenarios so that you can continue to access systems securely, even while under attack. This multi-layered approach helps to ensure that if one layer of security is breached, there are additional layers in place to protect data and applications.
6. Automate and orchestrate manual processes
Security automation technologies help teams move faster and more effectively during attacks. To improve cyber resilience, companies may consider using automation services like seamless privilege access, endpoint detection and response (EDR), identity access management (IAM), security information and event management (SIEM), and security orchestration, automation, and response (SOAR).
It’s also important to automate notifications and alerting. By doing so, security teams can easily work together more efficiently throughout the day. Alerts can ensure teams stay in the loop about emerging security events and are positioned to respond immediately.
7. Develop and test your incident response plan
Security profiles change by the day. Because of this, it’s critical to regularly test and optimize your cyber resilience strategy. When testing, it’s a good idea to assess and measure incident response performance and look for potential gaps and inconsistencies. This way, you can ensure your incident response plan is fully functional when it’s time to put it to use.
Delinea’s customizable incident response template will help you get started building a response plan to increase your cyber resilience.
Cyber insurance for cyber resilience
No matter how strong your cyber resilience strategy is, it’s simply not possible to fully prevent attacks from impacting your business. Eventually, threat actors will slip by and put your security defenses to the test. That’s just the way it is.
One of the best ways to bolster your cyber resilience is to invest in cyber insurance—a type of insurance policy that helps organizations recover from cyberattacks by covering the costs of damages, legal fees, and lost revenue.
When implementing cyber insurance into your organization, keep the following tips in mind to increase your chances of success:
Assess your resources and risk level
Before purchasing cyber insurance, you’ll want to go through the steps to cyber resilience above—assessing your business’s available resources and risk level to determine an appropriate level of coverage. This assessment should consider your business’s size, industry, data sensitivity, and potential threats you’re likely to be impacted by (e.g., ransomware).
Choose your cyber insurance policy carefully
You need to pick a policy that supports your business’s specific needs. Policies vary widely in terms of coverage and limits, so you’ll want to review your policies thoroughly before purchasing one. During this process, it helps to round up your legal and security teams—and potentially a cyber insurance broker – and ask them to review your options and provide feedback.
Review and update your policy regularly
Cyber risks and business needs can change rapidly. That being the case, reviewing and updating your cyber insurance policy regularly is essential to ensure that it remains appropriate for your organization's current needs.
Check out Delinea’s Cyber Insurance Readiness Checklist
Buying cyber insurance is a big step in becoming a resilient organization. But purchasing insurance can be a tricky process and one that requires preparation.
To make the process easier, Delinea created a Cyber Insurance Readiness Checklist—a useful guide that will help you answer the questions that cyber insurance providers are going to ask. When you’re ready to take the next step in your cyber resilience strategy, have a look.
Related reading:
Cyber resilience: The name of the game for 2026
Top 8 ways to improve cybersecurity for your organization.


