Delinea Platform
IT and security leaders face increasing challenges in protecting every identity across complex environments. The cloud native Delinea Platform reduces risk across human and machine identities with intelligent, centralized authorization, delivering compliant, usable identity security without slowing growth.
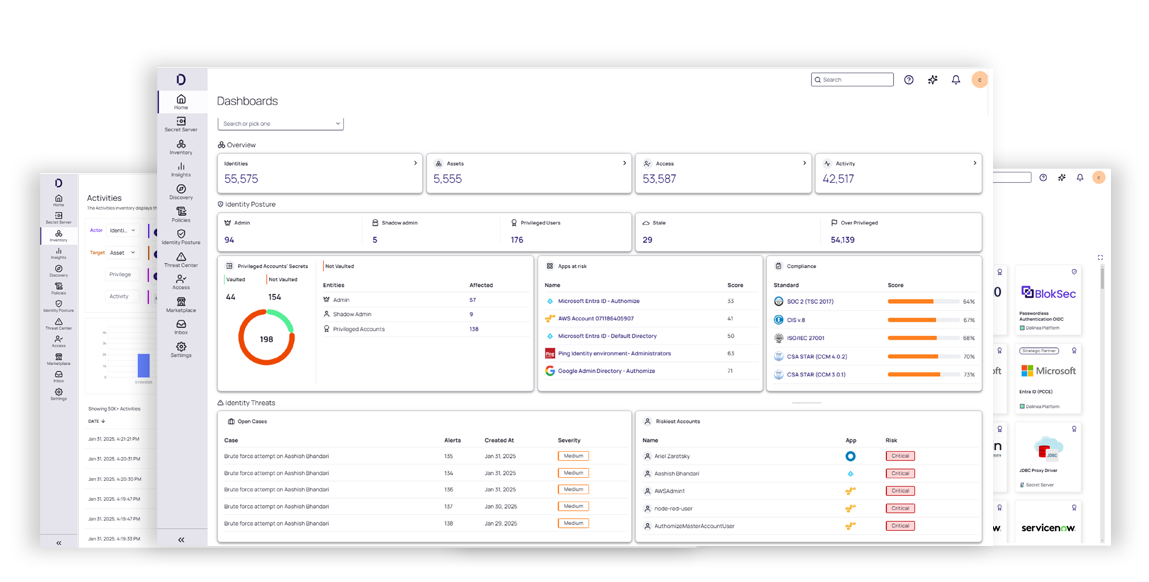
Delinea protects all types of identities throughout your IT environment
Protect IT admins, reduce risk, increase efficiency
Delinea provides a flexible, easy-to-deploy, intelligent, centralized authorization solution for securing IT admins against identity compromise.
- Reduce the cost of compliance with your privileged IT identities across hybrid and cloud environments.
- Monitor and audit privileged sessions and ensure appropriate access.
- Detect anomalous behavior and respond to threats in real-time.
Secure access for every employee, everywhere
The Delinea Platform provides seamless, centralized authorization to secure and govern credentials and access to systems and data.
Delinea protects the entire workforce through:
- Ensuring a centralized, policy-based approach.
- Eliminating inconsistent, siloed, manual processes.
- Removing gaps in workforce protection and reducing risk from identity-related threats.
Control machine identities, remove complexity
Reduce risk with continuous protection across the breadth of machine and AI identities and their access with centralized, intelligent authorization.
Secure your machine identities by discovering and managing:
- Service accounts
- Cloud service provider accounts
- Software-as-a-Service local accounts
- Artificial intelligence agents
- Static secrets
Manage AI identities with intelligent controls
AI agents act autonomously, requesting access, moving data, and invoking APIs. Delinea discovers and governs AI agents, vaults secrets, and enforces just-in-time privileged access so AI activity stays secure and auditable.
Manage and control AI identities by:
- Discovering AI agents and services automatically .
- Vault secrets and enforce time-bound, least privilege access.
- Automate lifecycle oversight to reduce risk and maintain compliance.
- Gain visibility into shadow AI, external models, and API usage.
Reduce risk without impacting developer productivity
Balance innovation and security by marrying a dynamic, intelligent approach to assigning zero standing privilege (ZSP) with a frictionless experience for developers, reducing risk, without impacting productivity.
With ZSP, you can ensure developers maintain only the access they need for the shortest time.

Protect your organization from identity-related threats
Reduce breach risk and blast radius by eliminating standing privilege, continuously controlling access across identities—human, machines, and AI. You gain clear visibility, detect risky behaviors early, and contain threats before they spread.

Remove friction from access governance, so users get the access they need, the moment they need it, without sacrificing security or control. Automation and AI reduce manual work and errors to keep your business moving and controls in place.

Consolidate tool sprawl into a unified identity security platform. Fewer tools, less manual effort, and reduced operational overhead lower your total cost of ownership without sacrificing security and control.

Make identity security flexible, resilient, and built for change. The cloud-native, microservices platform connects identities across hybrid cloud, SaaS, DevOps, and AI. Teams move faster, adopt new technologies confidently, and innovate without compromising security.

Centralized identity security reduces risk
Remove siloes to improve your security posture with a single source of truth to discover, monitor, protect, and secure access for every identity and every interaction.Visibility: Illuminate your identities
Hidden identities and unknown access paths create risk you can’t govern. Delinea continually discovers identities—human, machine, third-party, and AI—the moment they exist, along with every privileged asset across on-premises, cloud, and DevOps environments. You gain a clear, always current view of who has access to what, where exposure exists, and where policy is breaking down.
Posture: Quantify your risk
When everything looks critical, nothing is. Delinea continuously analyzes identities and access activity to surface and prioritize real risk that matters, unmanaged privileges, shadow admins, over-permissioned users, stale accounts, and high-risk human, machine, and AI identities. By correlating identity context with real-time behavior, Delinea delivers defensible, risk-based insight that enable leaders to focus resources, justify decisions and reduce exposure with confidence.
Control: Accelerate your business
Security only works if it keeps the business moving. Delinea turns identity insight into action with explainable risk signals and adaptive, real-time continuous authorization. Risk is contained faster, alert fatigue drops, and teams remediate what matters most, strengthening identity security posture while enabling the business to operate at speed.
Take the next step to secure all identities
Under the hood of the Delinea Platform

The Delinea Platform powered by Delinea Iris AI
Delinea Iris AI empowers you to stay ahead of identity threats with real-time, intelligent access decisions and granular, evidence-based insights.

Built-in capabilities
The Delinea Platform’s shared capabilities built into the platform deliver a secure foundation that reduces complexity, lowers cost, and extends consistent control and insight across every identity and system.
Download the report


