Does your IT security budget include PAM? If not, you should be worried

View the source report: 2022 Trends in Securing Digital Identities
Businesses of all sizes and spanning all industry verticals have witnessed growing cyberattacks and security breaches in the last few years. Looking at the stats above, it’s highly likely that compromised credentials and privileged access abuse were the cause of these breaches. Password misuse, mismanagement, and sharing have a ripple effect making passwords easy targets for attackers.
Beyond financial risk, the stakes are higher than ever before. The impact is especially significant for critical utilities, emergency services, medical facilities, and other essential government services, where cyberattacks can put lives at risk.
 The case for robust Identity and Access Management (IAM) solutions for your IT security budget is a no-brainer considering increasing threats, rising data breach costs, non-compliance penalties, and cyber insurance costs. In any economy, preventing data breaches and attacks is a business imperative. Proactive risk mitigation is not just an IT problem—it must be baked into company culture and budget planning.
The case for robust Identity and Access Management (IAM) solutions for your IT security budget is a no-brainer considering increasing threats, rising data breach costs, non-compliance penalties, and cyber insurance costs. In any economy, preventing data breaches and attacks is a business imperative. Proactive risk mitigation is not just an IT problem—it must be baked into company culture and budget planning.
Clearly, IT has a limited budget and must make wise security investment decisions. However, since most breaches involve compromised credentials, it’s important to prioritize investing in identity-centric security solutions designed for modern hybrid and multi-cloud IT infrastructure.
Why IT security budgets are better spent on privileged access management instead of more firewalls
The top-ranking identity-related breaches in the past year include inadequately managed privileges, stolen credentials, and compromised privileged identities.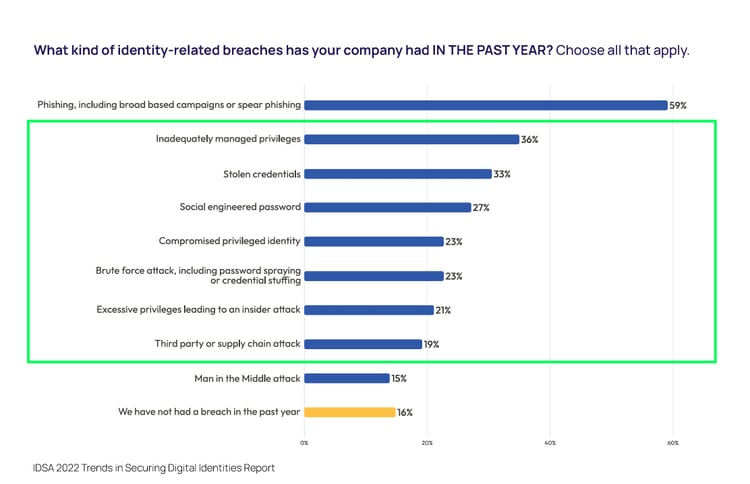
These are common tactics for cybercriminals who compromise accounts and elevate privilege to move laterally between servers. Privileged Access Management (PAM) is critical to protect these servers and prevent, contain, and detect security incidents before they turn into a breach.
Let's not forget that cyber insurance carriers are demanding stronger PAM-related security controls such as Multi-Factor Authentication (MFA) as an insurance condition.

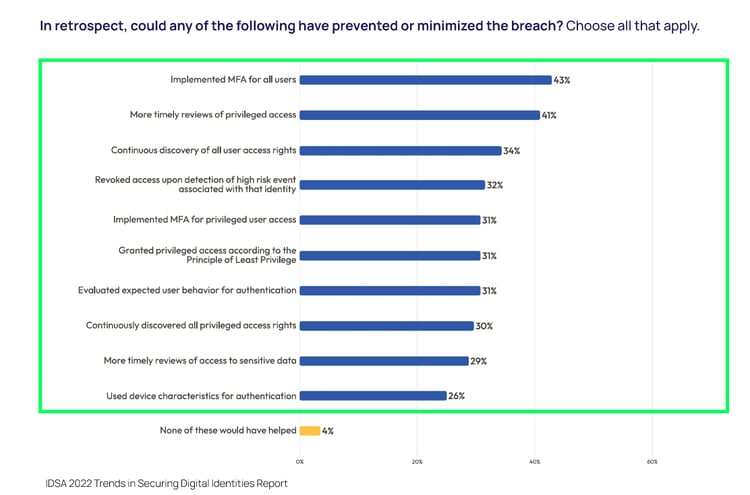
Preventing identity-based breaches is a priority in any organization's security program. Are you boosting your cyber resilience by first fortifying your front gates? Let’s take a look at where how cybersecurity budget allocations are projected to shape up in the coming years.
How are organizations budgeting their IT security spend?
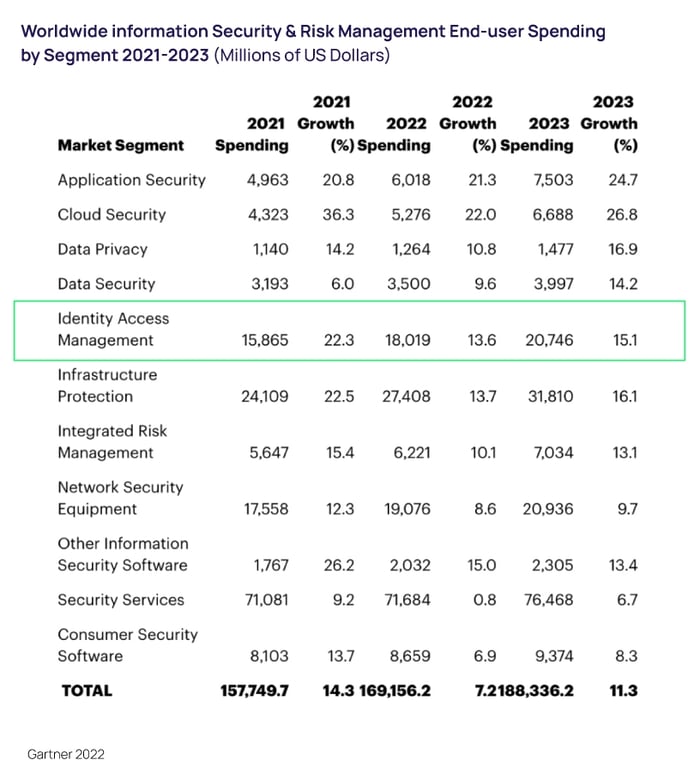
According to Gartner, worldwide spending on security and risk management is forecast to grow 11.3% in 2023, with IAM solutions predicted to increase by 15.1%. The growing worldwide emphasis on cybersecurity is a move in the right direction.
With PAM cited as the top priority project for CISOs by Gartner, your executive team needs to understand PAM’s business impact in terms of:
- security risks and threats
- compliance and audit issues
- operational challenges
The risk of regulatory fines and ever-increasing costs associated with a data breach should not be the only reasons for IT security budget planning. Investing in a proactive security solution will help you put up your strongest defenses and decrease your IT operating costs.
Now you have enough evidence to present a strong proposal to your board for allocating your IT security budget on identity-centric security solutions. The costs of internal security incidents, failing audits, and the threat of compliance violations are significant motivators for board approval of cybersecurity investments. Investing in a modern PAM solution can have a measurable impact on the bottom line.
So how does PAM help prevent data breaches and ransomware attacks?
A PAM solution centralizes and orchestrates fragmented identities, secures privileged access, improves audit and compliance visibility. PAM reduces risk, complexity, and costs.
View our webinar: Two Sides of the PAM Coin
Modern PAM identity assurance capabilities—like MFA and granular access control—monitoring, and anomalous activity auditing make it harder for attackers and can stop the cyberattack chain. PAM allows only the right people to access the correct application with Just-in-Time (JIT) and just enough access.
Related reading: How Just-in-Time privilege elevation prevents data breaches and lateral movement
Want to see where your organization stands in implementing PAM controls? Read our PAM Maturity Model whitepaper to better understand your current and future security state and what PAM controls exist to help close the gap.
Here’s a top tip when considering your cybersecurity budget allocation: focus on investing in a low-complexity and scalable PAM solution to help reduce friction and seamlessly secure access to your critical resources.
A scalable solution can address the various challenges of privileged accounts, including vaulting shared passwords, host-based session auditing, and video capture that serves both audit and security needs. We believe cybersecurity solutions must be easy to use, or they won't be successfully implemented and leave networks and systems dangerously unprotected.
Looking for more info on PAM pricing and budget questions?
Check out our blog: The Real Cost of PAM Software.
Until both the CISO and board speak the same language, cybersecurity will be limited to a reactive role. Switching to proactive security drastically reduces your business risk and saves more money by preventing incidents. Attackers are increasingly using privileged user credentials to access and exfiltrate data. By effectively managing access rights for all human and machine identities first, you can proactively secure the keys to your kingdom. A modern PAM solution must be a high priority for your IT security budget. If it’s not, you should be really worried.

FREE WHITEPAPER
Take your Privileged Access Management to the Next Level