Secure remote access part 2: The best approach
This post is part of a series on Secure Remote Access
Read: Part I | Part II
Welcome back! This is the second part of a blog about Secure Remote Access for IT Administrators, which highlights Good/Better/Best methods.
Let’s recap what we learned in the first blog:
- GOOD: A VPN is better than nothing, but it’s not great at securing remote access for IT administrators, which increasingly includes outsourced IT, managed service providers, and other third parties and the risk that could come with them being able to access other systems on the broader network.
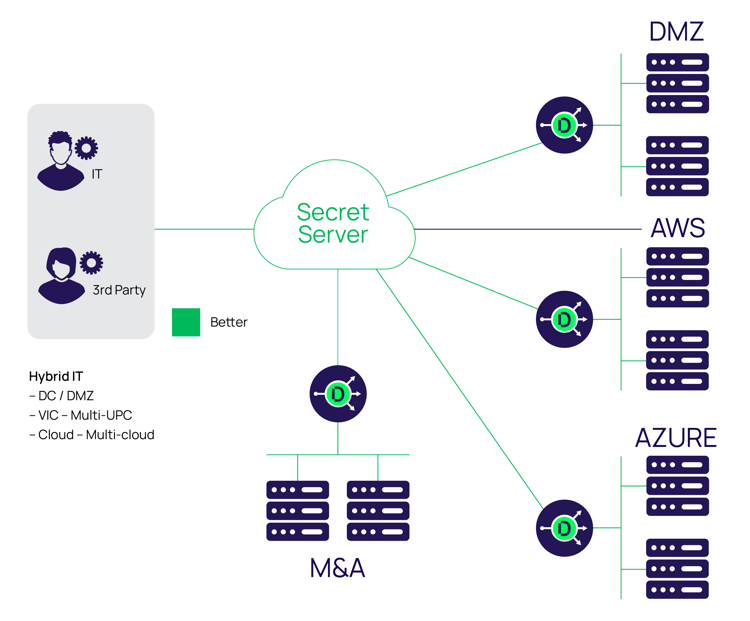
- BETTER: Adding Delinea Privileged Access Service on top of a VPN is a better option because it provides better control, security, and operational efficiencies. In this hub and spoke model, the Delinea Gateway Connector spoke acts as a bridge – the ONLY bridge – to the servers and network devices.
With the “Better” option, the user is still network-attached so there’s inherent risk there, but with the additional Delinea security, many risks of the “Good” approach are mitigated.
The Best Option: Ditch the VPN Completely
When you look at business continuity challenges related to a 100% remote workforce, the business needs to:
- Allow access to the resources required, NOT the entire network.
- Provide granular privilege, not just administrator or root. Not everyone with access
- truly needs complete administrative access.
- Ensure a higher level of certainty that it is truly the admin taking actions on the resources.
- Manage resources anywhere without requiring knowledge of the network configuration to access the resources.
- Allow an admin to access the resources they have a business need to manage without dependencies of VPN or client software.
- Allow any admin to access the resources they have a business need to manage without requiring corporate-owned machines and provide access from a clean source.
©2020 Centrify Corporation. All Rights Reserved.
With this approach, you get all the Delinea benefits of the “Better” solution, plus all the benefits of avoiding the VPN-based downsides. If faced with scaling a VPN solution to support a huge uptick in remote users, this approach is much more cost-effective.
Arguably, the biggest benefit is keeping users off the network, and in the process, ensuring a “clean source”. IT doesn’t have to worry about the health of 3rd-party workstations or laptops, VPN software, and infrastructure, VPN-related help desk calls, elaborate tools such as Cisco NAC, etc.
Some might argue the biggest benefit is its ability to scale out to accommodate networks of IT infrastructure in different places, with ease. Its hub and spoke model allows you to deploy as many Delinea Gateway Connectors as you need with no additional license cost. As a lightweight service, the Delinea Gateway Connector has minimum system requirements, installing on a non-dedicated Windows server. Got a new VPC for a new service? Workloads in multiple VPCs or multiple clouds? A merger or acquisition? Simply drop in a new Delinea Gateway Connector, enroll it in your Delinea Privileged Access Service SaaS, and you’re on your way.

FREE EBOOK
Privileged Access Management For Dummies