Secure Remote Access Paradigms Pros and Cons
Remote users expect instant connectivity so they can access the same systems they use when in the office. However, increasingly complex hybrid cloud, multi-cloud, and on-premise infrastructures make remote privileged access more difficult for IT teams to manage and secure using traditional access management techniques. Therefore, enterprises need a flexible, easy-to-use method for secure remote access that strikes the right balance between productivity and central control, without compromising either one.
In this blog, we’ll explain how to address the changing requirements of secure remote access and overcome the obstacles traditional remote access methods present.
First, let’s lay the groundwork with some definitions.
What is remote access?
Remote access provides users who aren’t physically in the office the ability to access enterprise IT systems, computers, and files through a network connection. Many people within an organization rely on remote access to do their jobs, including IT administrators, developers, and business users. More broadly, the term “remote users” can apply to employees and third parties, as well as IT systems and service accounts that connect without human intervention.
The number of people and systems requiring remote access is growing. After years of remote work due to the COVID-19 pandemic, many organizations expect a hybrid workforce to become the norm. According to a recent Gallup poll, of the 60 million Americans who could potentially work from home: 30% would prefer to never come into the office during the week, and 60% want a blend of working one to four days per week at home.
Growing use of remote third parties is also driving the need for remote access. Enterprises increasingly rely on contractors, vendors, and partners that perform various activities and supplement internal teams.
What is privileged remote access?
Privileged accounts provide specified levels of access to users and IT systems. For example, privilege provides access to specific systems and data that have business-critical information, often governed by compliance requirements, such as:
- HR applications, which contain protected salary, health, and personal information
- Social media that impact a company’s brand and reputation
- Cloud infrastructure, such as applications and databases
- Legacy or custom IT systems that contain intellectual property, or proprietary information
Additionally, to support remote users, help desk teams leverage privileged accounts to log in and fix any remote device on any platform.
What is secure remote access?
Secure remote access reduces the risk of cyberattack. Ideally, access should be granted according to the Principle of Least Privilege, meaning all privileged users, including those working remotely, should be granted just enough privilege to access what they need to do their jobs—nothing more.
High-risk remote access situations occur for several reasons:
- Likelihood of privileged users mixing systems for personal and work.
- BYOD and multiple form factors, which increase the difficulty of keeping systems up to date.
- Risky remote access scenarios, such as users connecting via insecure public networks in hotels, airports, cafes, or even at home.
- Privileged users storing passwords for web-based applications in their browsers, which can easily be stolen.
Remote access risk increases for third parties. IT teams must spend a lot of time manually setting up accounts for a contractor and must keep tabs on when contractor access needs to expire. Compliance and risk assessment teams often struggle to collect data to demonstrate third-party compliance with secure remote access policies.

Traditional remote access methods expose security gaps
Privileged accounts must navigate SSH (Secure Shell) and RDP (Remote Desktop Protocols) protocols to gain remote access, which makes the management process complex and cumbersome. Traditional methods end up making more work for someone—often IT operations, as well as business users.
What’s more, traditional remote access methods lack granular access management controls. This is especially difficult when you want to provide only a certain level of access to third-party contractors.
Let’s look at the standard paradigms for remote access:
- Direct access. It’s not new news that direct access is bad practice, especially when it comes to RDP. Opening a port in your firewall that is insecure means open season on your servers.
- VPNs. Let’s face it: VPNs suck. They’re hard to navigate. How well they work depends on the user’s network, which can slow down and interrupt connections. Users are asked to verify their identity multiple times on difficult systems. In this case, “Multi-Factor Authentication” could mean “multiple flavors of annoyance.”
- Legacy desktop tools. Some people love legacy desktop tools, such as remote virtual desktop solutions, that provide secure remote access. The problem is that an agent or application must be installed on every single employee laptop to load up and broker that connection. It’s a beast. For IT, it’s yet another software to install and maintain, not to mention user training. There’s too much possibility that something could go wrong.

A new paradigm to secure remote access
Secure remote access and zero trust
Any secure remote access solution should be built upon the Principle of Least Privilege and Zero Trust practices. In a Zero Trust access model, assume any user or system that accesses the network, services, applications, data, or systems starts with zero trust. To gain authorized remote access, trust must be earned by the prospective user through verification.
Users should authenticate using modern multi-factor authentication (mfa) techniques including biometric, geo-proximity, and geo-location. Additional factors of authentication should be required before providing access to critical web applications and sensitive data.
Once a user is verified, their access is limited to only what’s necessary to accomplish the specific task or job. For example, secure remote access policies should limit precisely what workers, contractors, and third parties can access, perform, read, and interact with across web applications, servers, containers, and databases.
Centralized session authentication and management
Effective secure remote access solutions must allow IT teams to manage access easily, even automatically, according to central policies. Granting access through an intuitive, central portal helps you seamlessly integrate existing SSO and Multi-Factor Authentication solutions and navigate RDP and SSH connections.
Via a central portal, you should be able to activate continuous session monitoring, so you can record, review, and audit all access sessions to web applications, servers, and containers without installing any agents. The degree of session recording may vary depending on your compliance and business requirements. With some servers, you may require keystroke logging and video capture, whereas other servers may only require keystroke logging.
Privileged access pathways
A Privileged Access Management (PAM) solution provides privilege management capabilities, including the creation of privileged access pathways, for secure remote access.
For example, you can create Alternative Administrator accounts, dedicated to performing administrative work. These types of privileged accounts are used for privileged functions, while mitigating the need to use a broad Domain Administrator account (aka God account, superuser, superadmin) whenever possible.
An Alternative Admin account can be added to the local Administrator group when in use on a destination system. To log on directly to servers to perform privileged work, remote employees would need to leverage Alternative Administrative rights. These accounts should require MFA at system login when accessing an internal system remotely.
Instead of provisioning VPN accounts for remote workers and third parties and granting them access to your network directly, you could provision them similarly to Alternative Admin accounts that are distinguished uniquely compared to employees. As part of a secure remote access workflow, third parties would need to have approval and additional MFA requirements to elevate their privileges.
Web-based secure remote access
Remote access security must happen behind the scenes so users can work without being interrupted. Otherwise, frustrations bubble up and IT faces the backlash.
That’s why we recommend a new paradigm for secure remote access: Secure Web Browser-Based Sessions. The web browser is how users tap into the remote access capabilities provided by your privilege management system. This will give users isolated access to only the specific system(s) they are accessing at a given time to perform work.
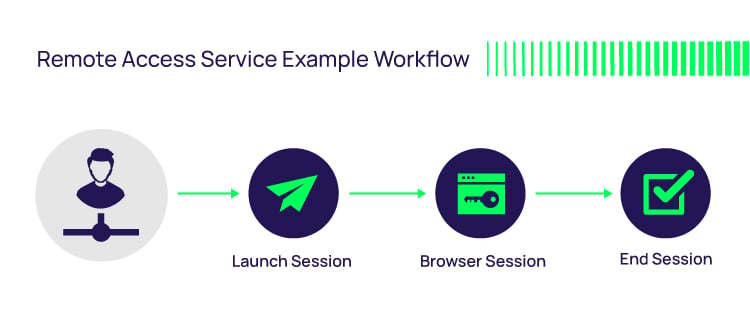
The benefits of web browser-based remote sessions include:
- No need to open up ports
- No need to install software on endpoints, including servers and user workstations
- Easy to provision new remote employees and remote third parties
- Keeping infrastructure secure, while allowing convenience for employees without the buildup of infrastructure and support
For users, it’s as simple as loading a web browser on whatever system you have and getting into a remote server.
For IT, you can use the secrets you already have vaulted in a PAM solution and use a private IP address for your servers to increase security.
Interested in learning more about secure remote access?
With Delinea, privileged users can log in remotely using a vaulted account or their individual Active Directory, LDAP, or cloud directory account, from anywhere without a VPN. MFA adds an essential layer of identity assurance to help stop data breaches.
Learn more about Delinea's Privileged Remote Access.
Secure privileged remote access for everyone
More Secure Remote Access Resources:
Free Tools:
Browser Stored Password Discovery Tool
Connection Manager Free Trial (Remote Connection Software)
Solutions: Secure Remote Access Solutions
Glossary - what is:
Cloud Computing Security
Least Privilege
Privileged Session Management
Remote Desktop Protocol (RDP)
Secure Shell (SSH)
Zero Trust

FREE EBOOK
Increased cloud adoption poses greater security risks to your IT and business users



