Privileged Access Management Best Practices
Privilege Access Management (PAM) is a top priority for many organizations around the world as cybercriminals continue to target privileged accounts to gain access, move around the network, and carry out malicious activity.
Due to the critical impact of privileged accounts, organizations continue to look at PAM best practices to protect and reduce the risks of privileged accounts in traditional environments and cloud infrastructure. Privileged accounts are found everywhere as they are required for managing IT environments and enable employees to carry out administrative tasks.
For two years, Gartner named privileged access management the top IT security priority and recently part of their Top 7 Trends in Cybersecurity for 2022 under Identity System Defense. Privileged account credentials for domain admins, service, application, and root accounts are valuable targets. When attackers gain these credentials, the attackers can then exploit your most sensitive information and critical systems. Privileged access gives them the power to alter data, change configurations, or even shut down your operations. Masquerading as privileged users, attackers can cover their tracks and go undetected for months or even longer. Despite this, many organizations fail to meet even basic PAM security hygiene.
Some of the top privileged accounts organizations must protect:- Domain Admins
- Local Administrators
- Root Accounts
- Service Accounts
- Network Accounts such as CISCO Enable
- Application Accounts
- Automation Accounts to run workloads
So, what should you do to protect your privileged accounts and your organization? Here are our best practices for privileged access management.
PAM Best Practices
1. Understand your internal PAM landscape
Without knowing where privileged accounts exist, organizations may leave in place backdoor accounts that allow users to bypass proper controls and auditing. External attackers may create user accounts for later access that can go undetected for months.
Identifying what a privileged account is for your organization is usually the best starting point for organizations and PAM best practices. It can be different for each company, so it’s crucial for you to map out important business functions that rely on privileged accounts, such as the data, systems, and access. Gain a working understanding of who has privileged account access and when those accounts are used, because you can’t manage unknown privileged accounts. With many organizations adopting more and more cloud services, it’s important to map your PAM best practices for your cloud environments.
The PAM Lifecycle steps are detailed in this blog post:
The Privileged Access Management Lifecycle and Path to Maturity
Want to own your PAM journey? Observing the PAM best practices described in this post will get you going in the right direction. However, we recommend you also view one of these—select one based on your comfort level:
Get better acquainted with PAM basics in our PAM for Dummies e-book
Take your existing program to the next level with our Expert’s Guide to Privileged Access Management
2. Write a formal privileged account password policy
It’s critical to have privileged account password protection policies in place to prevent unauthorized access and demonstrate security compliance. You can use this Privileged Access Management Policy Template, which was developed according to best practice standards from SANS, NIST, GLBA, ISO17799, and ISO9000.
As you start or update your PAM best practices, ensure that your organization has a solid definition of what privileged access management means for your business.
Your policy should include requirements for both human and non-human accounts (aka machine identities). For human accounts, you should use passphrases, which are a type of password that is easier to remember while still complex. Just this year the National Institute of Standards and Technology (NIST) removed its recommendations around complexity requirements for human accounts.
Forcing password complexity along with frequent password rotation results in cyber fatigue and user friction. This inconvenience results in users reusing similar passwords across multiple accounts, which increases the risks of successful brute-force attacks that occur when a credential is compromised or stolen. Stolen or compromised accounts increase the risks of additional accounts suffering a similar fate later.
As an important part of the PAM best practices, you should prioritize moving passwords into the background which will improve employees’ authentication and authorization experience, such as combining a password-less authentication experience with a strong privileged access management solution. If you are considering going down a passwordless authentication as part of your PAM strategy, then check out my blog: Passwordless authentication: making the vision a reality.

Privileged access management best practices include choosing the timing by which all privileged passwords are changed. Generally, non-human or system-based account passwords should be changed frequently; human accounts secured with Multi-Factor Authentication (MFA) may not need to be changed as frequently or could be changed only when a known risk or breach is uncovered. It’s critical that all privileged account passwords be updated automatically and simultaneously, both on a regular basis to meet compliance mandates, and on an ad-hoc basis, such as when an admin leaves or if a security incident or data breach occurs.
3. Change default usernames and passwords
This may seem obvious, but using default usernames and passwords creates significant risk as they are an exceptionally easy target for cybercriminals to compromise. Default software configurations for systems, devices, and applications often include simple, publicly documented passwords. These systems usually don’t have a user interface to manage these passwords, and the default passwords are typically identical within all systems from a specific vendor or a product line. These default passwords are intended for initial installation, configuration, and testing operations, and must be changed before deploying the system in a production environment.
Check your password habits against our 20 password management best practices.

Privileged Access Management For Dummies
4. Manage shared accounts
Shared accounts are another easy target for cybercriminals and provide little to no accountability. Shared accounts lack access control and cannot be properly attributed to incidents because one user can’t be directly linked to specific account activity due to the shared nature of the account. This adds to the security risk. PAM security solutions are critical here to manage these accounts with full auditing of access and usage.
5. Monitor activity on privileged accounts
Privileged accounts should be protected through session monitoring, recording, and auditing. This helps enforce proper behavior, adherence to security protocols, and help avoid mistakes by employees and other IT users as they know their activities are being monitored. Security teams must be able to see at a glance which policies are implemented, as well as exceptions that require closer attention or additional user education. If a breach does occur, monitoring privileged account usage helps digital forensics identify the root cause and critical controls that can be improved to reduce your risk of future cybersecurity threats. Managing and securing Privileged Accounts and Session Management (PASM) is a critical component of PAM solutions and a top best practice for PAM strategies.
Auditing privileged accounts also give you cybersecurity metrics that provide executives, such as the Chief Information Security Officer (CISO), with vital information to make more informed business decisions. Auditors also use this information to see who had access to what information and why.

6. Implement least privilege
Least privilege is a security model whereby once a user is verified, the user’s access is limited to only what’s necessary to accomplish their specific task or job. If any user action requires more access than granted via policy rules, permissions to elevate privileges are strictly controlled and monitored. This means no more full local administrator access to endpoints and helps minimize the risk associated with compromised endpoints, the most common entry point for attack.
Removing local administrative privileges on endpoints blocks that common attack vector and reduces your attack surface. Utilizing application control behind the scenes to enable needed applications for users to do their jobs allows least privilege to be successful, with no downtime or loss of productivity. Privileged Elevation and Delegation Management (PEDM) is a critical component of privileged access solutions to ensure that users can elevate privileges on demand when they need to perform administrative tasks.
7. Establish privileged access governance
Governance ensures that privileged account access is properly controlled and monitored throughout the entire lifecycle. It defines the roles, policies, and mechanisms for access requests, as well as the workflow for privileged access approvals and delivery. It also ensures that account permissions remain appropriate over time. PAM governance can also intersect with other IT security systems, such as IT ticketing systems, identity governance tools, and identity and access management solutions.
8. Ensure buy-in across your organization
Cybersecurity and Privileged Access Management must be visible and a positive experience for all employees across departments, including your executive team. Proper security awareness training is a good way to share your organization’s security policies and build an understanding of the associated risks when those policies are not followed. Training also helps your staff become better employees by empowering them to do their jobs better.
We know that PAM is not a simple fix and the PAM best practices and strategy is not the same for every organization. The PAM Best Practices and PAM Lifecycle approach provides a framework to help PAM experts manage privileged access as a continuous process.
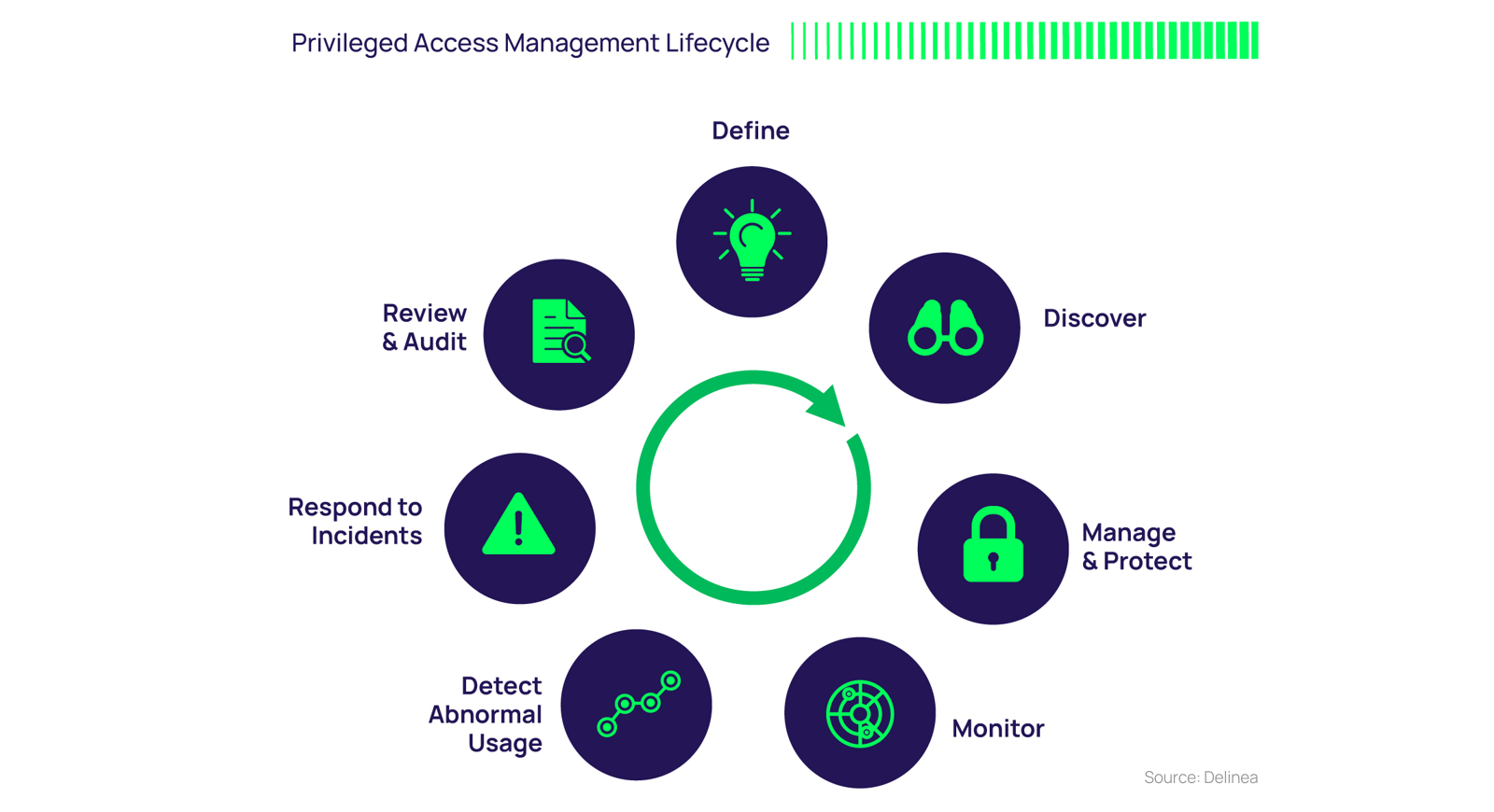
The key stages of the PAM Lifecycle include:
- Define: define what ‘privileged access’ means and identify what a privileged account is for your organization
- Discover: identify your privileged accounts and implement continuous discovery to curb privileged account sprawl, identify potential insider abuse, and reveal external threats
- Manage and protect: proactively manage and control privileged account access, schedule password rotation, audit, analyze, and manage individual privileged session activity
- Monitor: Monitor and record privileged account activity
- Detect usage: ensure visibility into the access and activity of your privileged accounts in real-time to spot suspected account compromise and potential user abuse
- Respond: take action to protect compromised accounts and systems based on defined policy and breach intelligence
- Review and Audit: help identify unusual behaviors that may indicate a breach or misuse through continuous observation of how privileged accounts are being used
Why is Privilege Access a Top Security Priority?
PAM is MORE THAN SECURITY: It saves money
PAM is a POSITIVE SECURITY experience and empowers employees
PAM is a WIN for the CISO
PAM is a FAST TRACK to compliance/cyber insurance
PAM helps you RECOVER QUICKLY from cyber-attacks
PAM is a powerful security solution and makes a cybercriminal's job more difficult.
We want to make you a self-sufficient security champion so you can own your PAM journey, and observing these PAM best practices will get you going in the right direction. Then, depending on your level of PAM maturity, you can either get better acquainted with PAM basics in the aforementioned PAM for Dummies ebook, or take your existing program to the next level with our PAM Expert’s Guide.
IT security should be easy. We'll show you how


