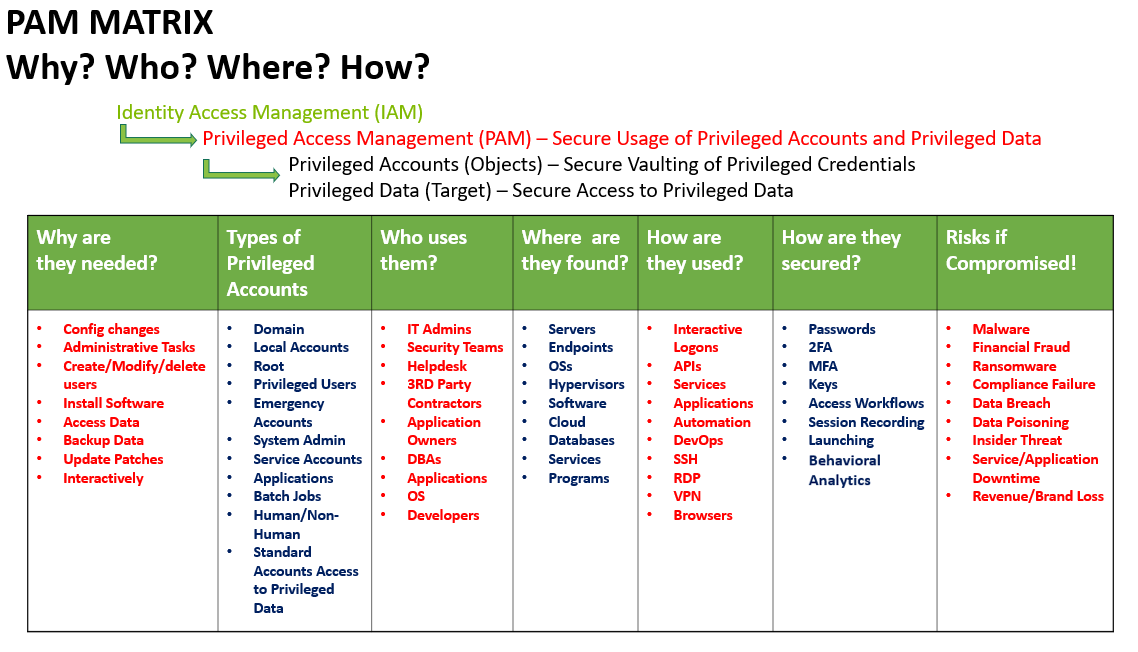
Privileged ACCESS Management and Privileged ACCOUNT Management are used interchangeably, or simply called “PAM”, but it’s important to understand the difference
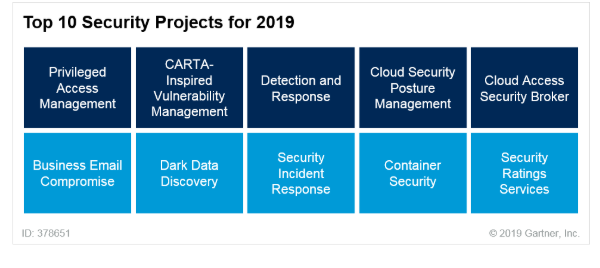
Privileged Access Management was at the top of Gartner’s Top 10 Security Projects for 2019. But in 2018 it was called “Privileged Account Management”.
So, what is the difference between Privileged ACCESS Management and Privileged ACCOUNT Management? And how do they relate to Password Management?
Although the terms are commonly used interchangeably, or simply bundled as “PAM”, I think it’s important to understand the difference.
A quick recap on Password Management / Managers
To fully understand PAM, it helps to view it in context with password management—the place where PAM has its roots. So, let’s have a quick recap.
Password management, or password managers, have been used for decades to store passwords within a central secure vault. Most password managers store credentials used to access multiple accounts like email, bank accounts, and system logins, along with a username, website URL, or IP address of system.
Password managers can be installed locally or accessed in the cloud. Most organizations that use password managers are inclined to leave employees to manage their own accounts, meaning the employees are responsible for creating and rotating the passwords for each account individually.
Password managers are great at generating long complex passwords and can auto-populate the password into the correct field so the employee does not have to type it in. This surely helps reduce cyber fatigue for employees. But here’s the problem: they are NOT good at managing privileged access which requires additional security controls, auditing, compliance reporting, and integration into multiple systems—especially important given the higher level of permissions they have.

Here are some common features usually found in a password manager:
- Encrypted Vault (cloud or Local)
- Browser Plugins/Extensions
- Two-factor authentication
- Auto Fill Web Forms
- Password Strength Check, Auto Generate, and Password Age
- Limited Sharing Capabilities
Brush up on your knowledge of enterprise password management.
Privileged Account Management, aka the old PAM
The next generation of password managers was introduced as Privileged Account Management. This PAM included the ability to integrate into multiple systems, share or delegate passwords to employees, rotate passwords, audit usage, check-in, and checkout processes. Privileged credentials are those accounts within an organization that have a much higher level of access, making it critical to protect and secure them.
I tend to look at a privileged account as the object that is being protected, such as a domain admin account, root account, or local admin account. This means it is about the account and password combination.
When Privileged Account Management was evolving it focused on password disclosure, checkout procedures for gaining access to the password, and the ability to share the password with colleagues for a limited time. Once the password was no longer required it was rotated so employees or 3rd party contractors would not know the password indefinitely.
But while Privileged Account Management includes many password management features, it is way more than just a password vault.
Privileged Account Management evolved to be a more robust security solution that still managed and secured the most critical credentials, but also offered enterprise features, such as:
- High Availability
- Enterprise Scalability
- Compliance and regulatory security controls
- Automated Discovery
- Integrations with Enterprise Solutions, like SIEM and Systems Management
- Control and Manage Sessions
- Role-Based Access
- Active Directory Integrations
- Automatic Backups
- Advanced Reports and Automation
- Approval Workflows
Privileged Account Management became a priority, helping organizations meet ever-growing compliance and security requirements—access control is where many organizations often fail in an audit. Not only was it a must for compliance, but it also became an important business enabler aiding organizations in solving complex interoperability projects, reducing overprivileged users, and reducing help desk costs brought on by constant failed logins or password resets. PAM became a positive business experience and helped reduce cyber fatigue.