Passwordless authentication: The easy button towards a password-free world?
Passwordless authentication is a holy-grail objective that always seems to be just out of reach. Why passwordless? Well, the human element is the root cause of most data breaches, with 82% stemming from stolen passwords, phishing, misuse, and errors. Let's not forget that users outright hate passwords. They slow us down, especially on small devices where it is easy to mistype passwords. Get rid of passwords and voilà, breach numbers are significantly reduced and users are happier!
So, what’s the holdup? Well, several communities had varying measures of success, but to be effective, passwordless authentication needs to be ubiquitous. Fully end-to-end.
Keep reading to learn more about how passwordless authentication works, user experience, digital security benefits, and important considerations for enterprises to create a secure passwordless future.
What is passwordless authentication?
Passwordless authentication, sometimes known simply as “passwordless,” is user identity authentication without a password—presenting a user identity without requiring a typed credential. One touch, you’re in.
Instead of a password, we use possession factors such as one-time passwords, mobile devices, and hardware tokens combined with unique biometric factors to validate a person's authenticity. Once validated, the user can then unlock and enable use of the possession factors, protecting the privacy of the biometric. With standards and protocols like passkey and FIDO2 (we'll meet them later), I'm bullish that this state of nirvana is within our grasp.
Passwordless can be presented as a veneer, masking the continued use of passwords under the covers
The devil is in the details, as they say. Passwordless can be presented as a veneer, masking the continued use of passwords under the covers.
For example, if I were a software developer and my application is not set up for passwordless, I wouldn’t want to incur the cost of re-coding the app. Instead, I could layer a passwordless mechanism in front that prompts a user for their ID and a second factor such as a fingerprint. The password is then injected behind the scenes. With the password still in play, the user is fooled into thinking the process is passwordless.
Compare this to the traditional log-in process where a user is required to present an identifier (typically a username) and a verifier (such as a password, passphrase, pin, credential, key, certificate, or another type of secret). The identifier confirms the identity of the user and determines what verifier is needed to authenticate and provide the level of access permissions.
With passwordless authentication, secrets are still exchanged to verify the user’s permissions and access level–they’re just exchanged behind the scenes. Secrets can be permanent or temporary, depending on your level of risk and security goals.
You can create passwordless experiences for users logging into:
- Servers
- Workstations
- Cloud applications
- On-premise applications
- Hybrid applications
- Legacy applications
- Databases
- Multiple other types of enterprise systems
Are passwords a relic of the past?
Everyone hates passwords. While a relic of the past, passwords still flourish as a protective barrier in front of websites, applications, workstations, and servers. But let's face it—it's a low-security barrier. Passwords are easy to crack, phish, and buy from Initial Access Brokers for pennies.
For end users, they're a bitter pill that sours our experience. For IT and the help desk, passwords require administration, decreasing operational efficiency. They expose us to risk and can negatively impact compliance. For incident response teams, they're a constant issue. Even for those who author laws, regulations, and guidelines, passwords require more substantial security and privacy treatment.
But there's more. We put the onus on users to manage passwords. We trust users will create and remember complex passwords, not share them, store them securely, routinely change them, and ensure they're unique. It's not surprising that in its latest Data Breach Investigations Report, Verizon tells us that the human element accounts for most data breaches, with 82% stemming from stolen passwords, phishing, misuse, and errors.
A password vault such as Delinea Secret Server mitigates all this. It can auto-generate long and complex passwords and auto-rotate them on a schedule. They can be automatically replayed when needed behind one MFA-protected lock, stored securely in the vault. This has the advantage of making the credential stronger, however, doesn’t solve the fact that the credential is known by the user and the website. If the website is compromised, then the credential is known by the adversary.
The more obstacles we place in front of users in the name of security, the less likely they are to comply
Historically, solutions to this puzzle have resulted in extra security at the expense of user experience. Infosec leaders know that the more obstacles we place in front of users in the name of security, the less likely they are to comply. So, the more seamless we can make a user's login and authentication experience, the less likely they'll explore ways to skirt it.
We've seen standards like HSPD-12 drive the use of smart cards for secure single sign-on in U.S. government agencies, federal contractors, and non-U.S. contexts using a variety of CAC, PIV and CIV credential variants. Challenges include a complex issuance process and the need to remember a PIN, which the FIDO Alliance solved with their U2F and UAF standards.
These standards triggered the use of USB form factor security keys and simpler use cases for mobile devices.
Meanwhile, innovations in mobile devices and modern laptops have driven down the cost of fingerprint and facial biometrics. It's now built-in along with trusted platform module (TPM) style technologies to secure private keys used for strong authentication once the biometric has been validated.
Widespread adoption of SAML has also simplified login to commercial web apps.
The Payment Service Directive (PSD2) in the European Union has driven the use of Strong Customer Authentication (SCA) and Multi-Factor Authentication (MFA) in FinTech.
Types of passwordless authentication
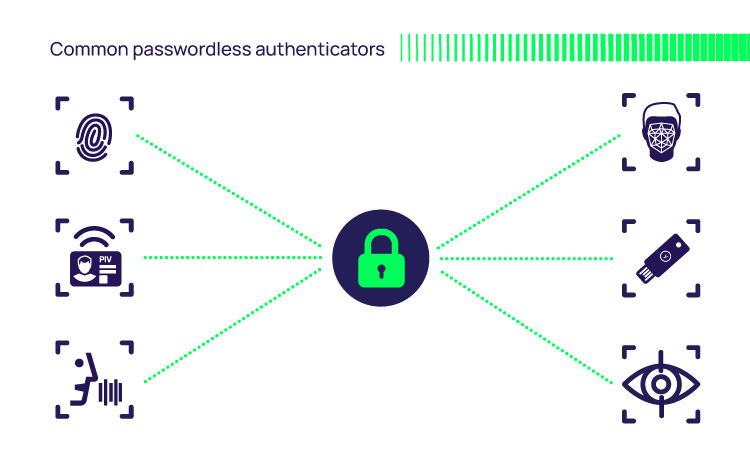
There are numerous ways to enable a passwordless log-in to make identification and verification easier. For example, rather than require a password to be typed, you could use one of these alternative types of credential:
- Facial biometric, such as Windows Hello or Apple Face ID
- Fingerprint biometric, such as Apple Touch ID
- Iris biometric. Used, for example, by border management and defense access controls
- FIDO authenticators from vendors such as Yubico and Duo
- SMS message supported by many applications such as Facebook, Google, and Amazon
- SAML for federated single sign-on, commonly used in web-based applications
- X.509 digital certificates used in many applications such as Wi-Fi, VPNs, and S/MIME secure email
- Email. User verification via a one-time passcode or a magic link (one-time use URL sent via email or text message)
It’s important to keep in mind that biometrics in this case do not replace passwords as they are not secrets. Rather, they replace or enhance the username or identity portion of authentication unlocking use of the possession factors.
Enter passkeys
As noted above, credentials exist that improve the user experience and provide higher assurance for high-risk users and critical services.
FIDO credentials are the most notable example. They can be used in software (for example, a Trusted Platform Module in a laptop) or with a roaming hardware token (for example, a YubiKey). They improve security by representing another factor – something you have – and being phishing-resistant.
Initially, FIDO tokens augmented the use of a password with additional factors. More recently, the FIDO alliance partnered with Big Tech (Apple, Google, and Microsoft) around a new passkey standard. As the passkeys.io website describes, a passkey is a new way to sign in that works completely without passwords. Instead of augmenting a password, it fully replaces the password. Passkeys build off existing FIDO standards, adding user experience and digital security benefits.
By taking passwords out of the equation, life is simplified for both vendors and users
Users can access their passkey from all their devices using a method they use every day—verification of their fingerprint, face, or device PIN. There's no need to enroll a new FIDO credential on each new device. Service providers can support passkey-based authentication without needing passwords, as an alternative sign-in or account recovery method. Management of the private key may be specific to the ecosystem; for example, Apple using its iCloud and Keychain to replicate.
Additionally, passkeys have been combined with auto-fill technologies to simplify the login process for users so that the user identity is auto-populated when accessing a web application which has been previously registered for passkey-based login. This results in a “no typing” experience for the user once they have performed the biometric verification.
Companies like eBay, PayPal, BestBuy, and Kayak have promised to offer a passkey alternative for logging in, and the Big Tech founding members have all updated their systems and apps to support it. This level of support will move us closer to a true end-to-end passwordless world.
Passwordless Authentication for the Enterprise
Will passkeys or something similar become de facto?
Making passkeys the norm will require every service provider to update their existing password-based authentication. We can anticipate passwordless adoption to flow from the cloud down to legacy apps and systems. Many SaaS apps already support modern standards and protocols like OpenID Connect, SAML, and OAuth2 for federated authentication from a trusted Identity Provider, as well as multi-factor authentication (MFA), so the lift should be easier.
Any web application that currently supports FIDO2 should be able to take advantage of passkey technology given the interoperability. For example, the identity services within the Delinea Platform supports FIDO2 and passkey-based passwordless user authentication. However, websites that have not yet added FIDO2 support will need to be modified to support passkeys.
We have the technology for passwordless . . . but are businesses making the switch?
So we clearly have the technology for passwordless authentication and passkeys, but are businesses making the switch?
According to Forrester Research, more enterprises are adopting passwordless authentication. A recent poll found that roughly half are experimenting with passwordless login. Most are piloting, running proof of concept programs, and small deployments with specific user groups. Surveys from vendors such as Ping Identity and Yubico report an overwhelming IT desire to adopt passwordless authentication. So, the dominos are falling.
Passkeys are great for passwordless login to laptops and web applications, but organizations must consider how to extend passwordless to servers and business applications. Enterprises have advanced security needs and require a more stringent level of authentication management.
Organizations will also require a higher level of assurance that the user authenticating with the passkey is the one for whom it was created. A modern privileged access management (PAM) solution for server protection, such as Delinea Cloud Suite, supports passwordless login and MFA.
Passwordless combined with strong credentials can satisfy nearly any scenario, making life easier for the user (biometric touch or facial recognition to gain access) and improving digital security for enterprises.
Several uses for biometric unlock:
- Biometric unlock for strong crypto-based mutual authentication to resources for more ubiquity and ease of use (for example, FIDO2 or passkeys plus federated login protocols like SAML, OAuth, and OpenID Connect.)
- Biometric unlock for crypto-based authentication to resources where strong mutual authentication is impossible (for example, SSH certificates.)
- Biometric unlock to access a shared secret as a fallback. I.e., a password or SSH Key under the covers where an underlying secret vault or password wallet auto-injects the password, enforces strong quality of service, and auto-rotates the password.
Enterprises must determine what is doable and feasible based on their current mix of modern cloud-based services and legacy applications, along with user experience versus resilience to attack pressures. For many, a fragmented infrastructure with a mix of passwordless and password-based services may persist for some time. Some may replace legacy apps with a SaaS equivalent to leverage modern passwordless and MFA services.
Some may take the veneer approach in lieu of an update from the vendor. While the user experience appears to be passwordless, the service is still reliant on using secrets behind the scenes. Without effective security controls, your enterprise is still at risk from adversaries capitalizing on the same password-based attack surface.
This can be facilitated by PAM solutions that include vaulting, privilege elevation, centralized identity, credential management, MFA services, and behavioral analytics.
Is passwordless authentication safe?
The answer to this question depends on our definition of secure. If we mean harder to crack and being more resistant to common methods of attack compared to passwords, then yes. But if we mean impervious to hacking, then no. But, as security practitioners, we are very aware that nothing is 100% secure.
When considering passwordless security, we must weigh the benefits across two main fronts. One is user experience, and the other is digital security. The march towards passwordless authentication has primarily been driven by the desire to make life simpler for users accessing commercial apps. Passwords, password management, and hygiene are well-recognized pains for end users.
However, for enterprises with higher-risk users, regulations to juggle, and the constant threat of ransomware attacks, passwordless security will often win out over user experience. But to reach that nirvana state of passwordless, we need a good balance plus coverage across all environments and use cases.
My example earlier leans more towards user experience, with the user not having to remember and type a password. Good enough for non-enterprise access scenarios, perhaps, but a sizeable password-centric attack surface remains under the covers.
Security benefits of passwordless authentication
Passwordless authentication protects your critical enterprise systems in the following ways:

Passwordless authentication mitigates risky user behavior
In the enterprise, passwordless practices avoid the need for people to use consumer-grade digital wallets, Excel spreadsheets, or sticky notes to store their passwords. While consumer password vaults are helpful for personal use, they don’t meet the consistency, monitoring, and reporting requirements of the enterprise. They also put the onus of responsibility for password maintenance on the shoulders of users rather than IT security experts .

Passwordless authentication offers greater protection from password theft
People often take the path of least resistance with passwords and create ones that are easy to remember and type, which also makes them easy to crack. You’ll find many passwords readily available for purchase on the dark web.
Cybercriminals have an abundance of tools for brute force, pass-the-hash (PtH), and other attacks that center around stealing and leveraging passwords. For these reasons, relying on passwords alone isn’t sufficient for protecting sensitive accounts.
Passwordless authentication makes it harder for bad actors to penetrate your cyber defenses. Passwordless authentication reduces the attack vectors and the risk that cybercriminals will leverage stolen credentials to escalate privilege and move laterally.
Passwordless authentication is much stronger than passwords, providing a superior assurance level-based risk profile, always at Authenticator Assurance Level 2 and typically rated Authenticator Assurance Level 3 (per NIST SP 800-63).
Passwordless authentication makes it harder for bad actors to penetrate your cyber defenses. Simply put, they reduce the risk that cybercriminals will steal and apply passwords and other privileged credentials.

Passwordless authentication eliminates password sharing
Password sharing is a way for users to avoid paying more for services—making it a major source of revenue loss for subscription service providers. It’s also an easy way for IT teams with a shared responsibility to maintain access to systems when someone is out of the office or on vacation.
However, password sharing is a big security risk because it allows multiple users access to critical systems and makes it impossible to know which user conducted which activity. Compliance reporting, auditing, and post-event forensics are virtually impossible.
Passwordless authentication eliminates the opportunity for password sharing. If users never even see their passwords, they can’t share them with others.
Productivity benefits of passwordless authentication
Besides improving security, passwordless authentication offers enticing productivity benefits.
Benefits for regular end-users
Logging in is arguably a mundane process that nobody relishes. The faster, the better. Having to remember passwords for every application (I have over 1,100 accounts!), change them routinely, and reset them result in delays that are eliminated with passwordless authentication.
Logging in to apps using familiar, everyday actions like a finger swipe, face scan, or PIN entry improves the user experience. Productivity plus happier users.
Benefits for IT and the Help Desk
Fewer passwords mean fewer help desk calls to reset passwords and unlock accounts.
In response to a security incident, IT can be overwhelmed with response and containment tasks, severely impacting productivity. Reducing the attack surface by replacing passwords with passwordless security reduces incidents and hence, reduces operational overhead.
To learn more about boosting user productivity while maintaining security, read our Cybersecurity Team’s Guide: Balancing Risk, Security and Productivity
Is passwordless right for my organization?
Before rushing in, it’s important to remember that passwordless authentication still comes with a few risks and challenges. Here are a few things to keep in mind before starting on your journey to becoming a passwordless organization.
Vulnerable systems need oversight and layers of defense
Even with passwordless authentication in place, critical enterprise systems are still at risk from unauthorized users and cyberattack. Cybercriminals can potentially intercept links, PINs, and email notifications and use them to gain access.
It’s a good idea to integrate passwordless authentication with a comprehensive privilege management strategy for enhanced visibility, security, and control. This way, you can centralize access management and limit data drift and exposure.
Provision and migrate to new devices
One of the major challenges with a passwordless experience is when users get new devices, and those devices need to be enrolled or migrated from an old device. This causes several risks in getting the new devices ready for a passwordless strategy. This process typically requires a backup key or recovery key in the case that the old device is no longer functioning or is lost.
Continue to educate users on security best practices
Not all users may immediately understand the need for passwordless experiences, and some may fear or question the change at first.
Consider holding a lunch-and-learn session or workshop to go over the shift to passwordless experiences and explain why the system is changing. This way, you can answer questions and guide users through the process.
Ensure careful orchestration and execution
Businesses that fail to implement passwordless architectures properly risk security vulnerabilities and access and performance issues.
The easiest way to avoid implementation issues is to work with expert third-party passwordless experience enablers who can help you get up and running properly.
Manage secrets through enterprise PAM
It’s necessary to rotate secrets periodically to reduce risk. However, manually rotating secrets takes time and creates extra work for IT operations teams and users.
Using PAM solutions, you can rotate secrets regularly and randomly without interrupting the user experience. This approach is much more efficient and eliminates time waste for users and IT teams.
How Delinea enables passwordless authentication experiences
Delinea is on the front lines of passwordless authentication with invisible Privileged Access Management. Invisible PAM enables you to manage multiple types of secrets seamlessly and securely. Operating entirely in the background, invisible PAM is designed so passwords are hidden and users stay productive. By deploying invisible PAM, your company can stop asking employees to remember and manage passwords and use modern, alternative options to grant and manage access.
We achieve invisible PAM with the Delinea PAM platform, which makes passwordless MFA available during authentication and step-up authentication for powerful identity assurance. Use it during Secret Server vault login, secret checkout, and remote session initiation. Use it during server login and privilege elevation using Server Suite and Cloud Suite. With Delinea Platform, all PAM bases are covered.
For the full scoop, learn more about invisible PAM, a core requirement for achieving a true passwordless state.
Conclusion
While passkeys are in their infancy, the backing of Big Tech and major service providers bodes well for a future where passwords retire gracefully. We expect to see further adoption as companies perfect their strategies and embed passwordless experiences into more use cases across the enterprise.
Find out how much you know about enterprise password management.
IT security should be easy. We'll show you how