Over the past weeks, we’ve learned more about one of the biggest cyberattack on the software industry supply chain. This attack is a wake-up call for the software industry.
It’s a true “mass indiscriminate global assault” as quoted by Brad Smith whom I regard as one of the most respected software leaders. His words during the CES technology trade show keynote should not be taken casually. It’s an assault against many public and private companies, affecting approximately 18,000 victims globally, many of which were Stage One victims. The attackers then targeted high-profile targets with Stage Two, such as Microsoft, FireEye, and government agencies.
Even if you do not use SolarWinds software, this breach could still impact you
I cannot emphasize enough the far-reaching implications of this security incident. We will likely be talking about it for years to come. Even if you do not use SolarWinds software, this breach could still impact you. What I mean by that is if you are a customer of one of the victims or have a partnership, or they are a supplier to your business, it could even be possible that the attackers moved deeper into their victims’ networks or accessed their customer data.
This is a reminder that we must do more to curtail cyberattacks, and we must do it together, as an industry. We cannot sit back and let this one pass by. It requires a full industry collaborative effort.
As we analyzed the details and timeline of this attack, we realize it was truly sophisticated. It attempted to stay covert; tracks were hidden. There was unlimited time, expert resources, financial backing, and creativity behind this attack. The preparation will have likely taken several years of testing, planning, staging, and executing. I’ve been involved in analyzing many major cyberattacks over the past 15 years, and this is close to the top of my list of the most serious.
What is the possible impact and motive for attacking supply chains?
As an Incident Response professional, I always look for the motive of the attack. This helps me put myself into the mind of the cyberattacker. Given the techniques used within this sophisticated attack, it’s highly likely that there were several motives, and that dedicated teams were behind this massive attack. This points to a nation-state or nation-state-backed operation.
Different attacker teams would have tackled different tasks, such as Infrastructure operations, payload, targeting, and exfiltration. These would have been separated based on campaign motives, such as espionage, intelligence gathering, IP theft, and potentially even staging for future preemptive strikes. Based on my previous experience, it may even be that some of the attackers did not know fully what they were looking for. This reduces the possibility of attribution and sometimes even forces misdirection. They are just one small piece of a much bigger puzzle.
It is possible that this is just one of many compromised supply chains. Now we must work vigorously to identify others that leverage similar tactics.
The scary thought is that now other nation-state actors and criminal organizations can reuse this technique and weaponize the tactics for further malicious attacks, ones that could be even more devastating. This attack is only the beginning, and it’s why we must act now. We must learn from this and act, as a global industry. We must combine our efforts to identify what we can do to reduce the risk of supply chain cyberattacks becoming the new threat that keeps CISOs, CEOs, and government leaders up at night.
“The victim here is not just SolarWinds; it’s the entire Software Industry Supply Chain”
~Joseph Carson
Uncovering the cyberattack piece by piece
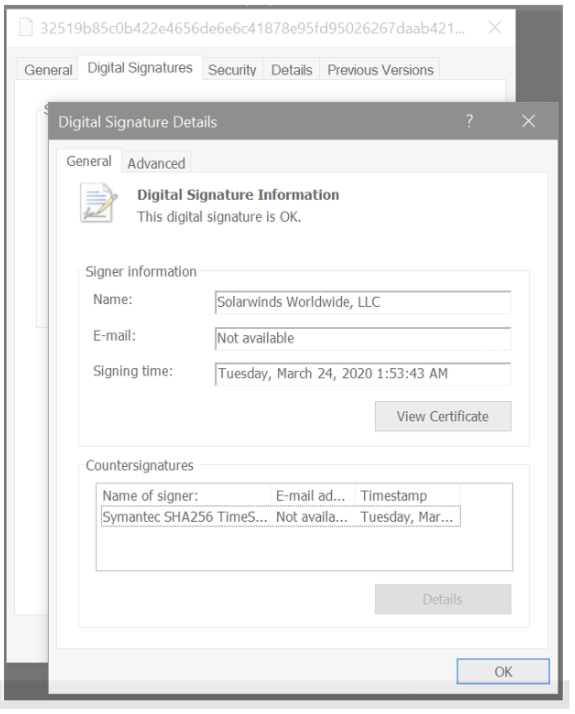
It all started on December 9th, 2020 when FireEye disclosed details about a security incident involving the theft of some of their Red Team penetration tools. After an investigation, FireEye (who has some of the best incident response and malware analysts globally) quickly analyzed the malware and started to uncover details about what happened. On December 12th they notified SolarWinds about a Trojan Backdoor hidden within the SolarWinds Orion product. The details of this are terrifying as it targets one of our most important security controls and trust mechanisms for fixing security issues—the digitally signed software/security update process.
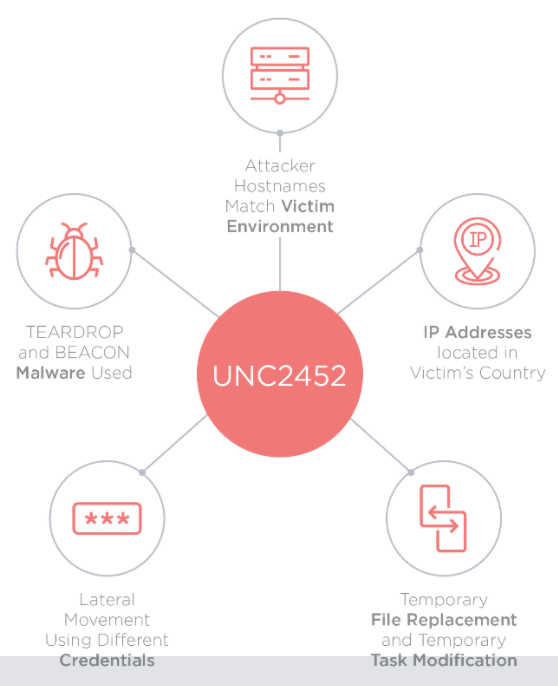
FireEye referred to the attackers as UNC2452 (aka Dark Halo, SolarStorm, and Solarigate.) Due to the threat actor not yet fully confirmed, it will likely get its APT Group alias later. It’s a globally distributed campaign that has far-reaching implications. Many vendors have identified the trojan backdoor and you can check out VirusTotals’ engine detection results here. UNC2452 has a possible association with Kazuar, according to Kaspersky.
“Is our digitally signed software update process severely compromised, and can we trust it moving forward?”
Joseph Carson
So, let’s take a step back and look at the timeline of what we know so far.
Initial foothold: Targeting the SolarWinds build repo and development tools
As we learn more, the complexity of the incident is revealed. It has the potential to cause havoc for years to come.
Crowdstrike disclosed how the cyberattackers secretly gained access to and abused the SolarWinds Build Process, and they named it SUNSPOT. SUNSPOT malware was used to monitor and learn about the SolarWinds Orion build process, including the running processes, so the malware could be used to insert malicious code during software compilation.
See how the attackers exploited Microsoft Visual Studio development tools and added a backdoor into the build process: SolarWinds Describes Attackers’ “Malicious Code Injection.”
The infrastructure used in the attack shows domain registrations used for the Command and Control (C2) going back as far as July 2018, and the initial threat actor accessed SolarWinds and ran tests between September and November 2019.
Once the attackers had gathered enough intelligence about the SolarWinds build process it’s likely they leveraged this to further test and plan the next phase: embedding the Sunburst malware into the Orion Software build. This occurred from February 2020, later removing and cleaning itself up in June 2020.
Disguised within legitimate network connectivity, the malware learned how SolarWinds’ software build process worked so that it could sneak a malicious DLL component into the build process. It masqueraded as SolarWinds code so that developers working on the code would not notice anything suspicious. Then it got compiled, ensuring that no errors occurred. It was ultimately digitally signed as a legitimate software update, waiting for the next campaign phase and the trojan to be delivered to the unsuspecting victims.
The multiple techniques used just to get the trojan into the software build process unnoticed are, on their own, very sophisticated and complex.
You have a new software update: The payload delivery
As IT teams, we expect that when a software update is available and digitally signed we can automatically trust it as it comes from the software vendor. This has been a common routine across the world; in the cybersecurity industry, we have put our trust in Digital Certificates.
In Spring 2020 a software update became available for SolarWinds Orion that was digitally signed and made available to 18,000 customers. So it was IT teams who, unsuspectingly, downloaded and deployed the trusted software update and the hidden trojan backdoor contained within.
SunBurst sleeping and lying in wait: The next move
Once the software update had been delivered, the trojan backdoor had many ways to evade detection and maintain persistence. One was to stay dormant for 12 to 14 days. Enough time had elapsed that even if something was detected, the relationship to this software update would be a little distant. The trojan made numerous checks to identify that it was running in a legitimate environment and not a sandbox.
Once the time had passed and the trojan activated, it commenced Stage One which was to profile the system to identify where it was and who the victim was. Once enumeration had been completed it would then communicate back to the C2 (Command and Control) using a subdomain technique to ensure it was unique, and inform the attackers of which victim they had access to and now controlled.
The malicious trojan would pretend to be a SolarWinds Orion Improvement Program (OIP) protocol, using fake variable names and camouflaged in normal data, storing reconnaissance results within legitimate plugin configuration files communicated back to the C2 server, and sending the system profile information it had gathered.
After initial access, the attackers used various techniques to disguise their actions while moving laterally around the network and systems. They remained stealthy, maintaining a light malware trail and reusing legitimate credentials to access the victim’s environment.
With so many victims reporting back to the C2, the attackers now had a trove of second-stage targets, many of which were very high-profile tech companies and included government agencies. Now they would determine who they wanted to access and lurk deeper into the victim’s networks. The initial Sunburst Backdoor allowed the attackers to execute commands remotely and enable access, leading to hands-on-the-keyboard attacks—the ability for the attacker to get interactive with the victims’ systems.
Some of the commands that the backdoor enabled the attacker to initiate were:
- CollectSystemDescription
- UploadSystemDescription
- RunTask
- GetProcessByDescription
- KillTask
- GetFileSystemEntries
- WriteFile
- FileExists
- DeleteFile
- GetFileHash
- ReadRegistryValue
- SetRegistryValue
- DeleteRegistryValue
The CollectSystemDescription command gathered the following system information:
- Local Computer Domain name
- Administrator Account SID
- HostName
- Username
- OS Version
- System Directory
- Device uptime
- Information about the network interfaces
The malware also leveraged Steganography to disguise its communications. Details can be found in the FireEye and Microsoft research.
Mapping this to the Mitre Att&ck framework is always helpful. Click on the image below to view an interactive navigator on the techniques used by UNC2452.
The lateral moves and privilege escalation: Stage 2 straight from the Hacker Playbook
Most past cyberattacks focused on abusing humans. However, this attack appeared to avoid that method—at least for now. Once the attackers had an open door to the victim’s environment via the Sunburst Trojan, they could simply access the environment remotely and make the needed changes to avoid further detection.
For most attacks, this means theft of sensitive data and privilege escalation, and that’s exactly what the attackers did in Stage Two. They targeted privilege escalation, stole credentials, and moved laterally in search of sensitive accounts and assets.
If you want to learn about privilege escalation techniques commonly used by attackers, read my blog post “Hardening Windows Endpoints Against Cyberattack“. It explains why and how attackers escalate privileges.
My biggest concern about the attack is that it targeted and abused forging SAML tokens. This not only allows the attackers privileged elevations but also enables them to expand into cloud environments such as Azure AD or abuse SSO (Single Sign-On) processes.
Were you a victim? You must activate your incident response now
If you were a victim of this unforgiving incident, then you must act urgently and hastily. I’ve learned from my incident response experience that attackers will have stolen credentials (including local administrator and domain administrator) which could allow them to return via another exposed door. Or, what normally occurs, they sell your credentials on the darknet where they’ll be found, purchased, and used to deliver ransomware or other malicious activities.
Please don’t wait until it’s too late. If you’ve discovered that you’re a victim, here are some actions you must take right away:
- Disable existing Domain Administrator accounts and move to new accounts
- Rotate all local and domain credentials
- Lockdown your SolarWinds Orion Environment and carefully update it with the patch from SolarWinds – SolarWinds Security Advisory
- Discover newly created accounts post-March 2020 and audit activity
- Audit and monitor your privileged accounts for suspicious activity
To get your incident response plan in place fast, download Delinea's Cybersecurity Incident Response Plan Template:
Delinea also has FREE TOOLS that will help you automate your privileged account password rotation.
Summary and Latest Updates
Just to be clear, there’s no silver bullet product that would have prevented such a sophisticated attack. Some solutions might have made it more difficult, however, these were dedicated resourceful attackers and they’ve exposed major flaws in our software supply chain. We must learn from this attack and work together as an industry to continue making access difficult for attackers.
Since writing this blog the news and updates continue to be released regarding this incident.
MalwareBytes has since announced that they were also targeted by the same group exploiting a dormant email protection product and ultimately gaining access to a subset of internal emails.
Symantec has revealed further malware discovered within their customers, which they have named Raindrop and Teardrop. It’s disguised as a 7zip file that includes a copy of Cobalt Strike to establish another command-and-control node.
A website has popped up called SolarLeaks, which claims to be selling source code from several of the SolarWinds Sunburst victims. This latest announcement introduced new motives such as financial gain. However, it is yet to be confirmed whether the same group who targeted SolarWinds is behind this, or whether it is indeed a scam, as most industry experts assume.
Realize that this is going deeper and deeper, and we must work as an industry to find ways to reduce the risks to our critical software supply chain industry.
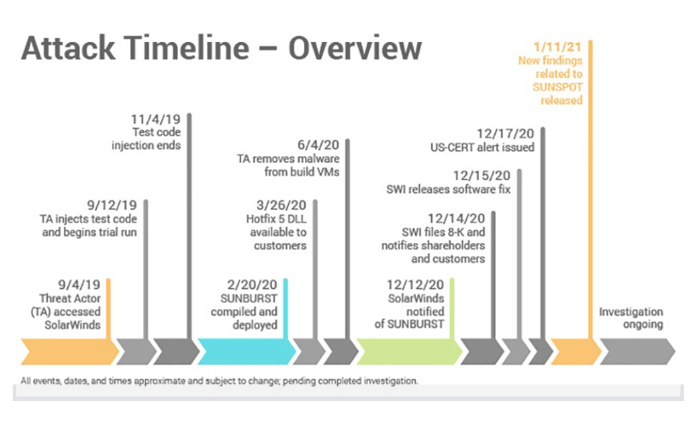 Source: SolarWinds
Source: SolarWinds