Unlocking Cybersecurity Insights: Exploring the MITRE ATT&CK Framework
In this blog post, we'll look broadly at the MITRE ATT&CK Framework and discuss how you can leverage it for research, education, and recovery. You'll understand what it is, the data it holds, and the hierarchical structure it presents.
By the time you've finished reading, you'll better understand how to assess attacker tactics and how they relate to your situation. You'll also appreciate how the Framework can help you proactively build resilience and assist with forensic investigations in the event of an incident.
What is the MITRE ATT&CK Framework?
The MITRE Corporation, a non-profit company managing federally supported research and development institutes, created the MITRE ATT&CK Framework (referred to as ATT&CK) in 2013. In the words of MITRE, it "is an open framework for implementing cybersecurity detection and response programs."
The ampersand in the name may have you baffled. The acronym ATT&CK stands for "Adversarial Tactics, Techniques, & Common Knowledge."
This knowledge is called Cyber Threat Intelligence (CTI). Consider ATT&CK as a knowledge base of well-known tactics, techniques, and procedures (TTPs) that you can use to enhance readiness for and response to cyber threats. ATT&CK provides guidance on detection and mitigation for a given technique where possible.
Instead of speculating how adversaries attack businesses like yours, MITRE's operationalized asset provides focus and quantifiable data
As you may imagine, there's a massive amount of security intel from dozens of sources. It's easy to get lost in that sea of noise. Instead of speculating (educated or not, especially with today's security skills shortages) how adversaries attack businesses like yours, MITRE's operationalized asset provides focus and quantifiable data—concrete factors—that help you make better-informed decisions. It's an essential tool for studying antagonistic behaviors and trends that would be challenging to quantify otherwise.
The primary data source for ATT&CK is publicly available threat intelligence and incident reporting. It also employs publicly available information that closely mimics opponents' actions because new tactics, techniques, and procedures (TTPs) swiftly appear in the wild.
ATT&ACK offers a thorough picture of how adversaries behave once they're inside your network, following a successful access attack. By integrating CTI into your security practices, you are better positioned to anticipate and defend against cyberattacks.
The TTPs describe adversarial behavior. They help us get inside the mind of the actors who attack us:
- Tactics describe tactical goals–the "why." For example, the credential access tactic to obtain privileged credentials to help the adversary move laterally from server to server while searching for sensitive data.
- Techniques and sub-techniques are the "how," describing specific tools or methods to execute tactics. For example, obtain credentials by scraping process memory on a Windows server.
- Procedures are more detailed steps to execute the techniques. For example, using Sysinternals ProcDump to dump an LSASS process from memory, then using Mimikatz to extract credentials.
There are a lot of TTPs! To help, MITRE has partitioned them into tables called matrices – Enterprise, Mobile, and industrial control systems (ICS.) The ATT&CK Matrix for Enterprise is the most well-known, documenting adversarial attack approaches against enterprise networks.
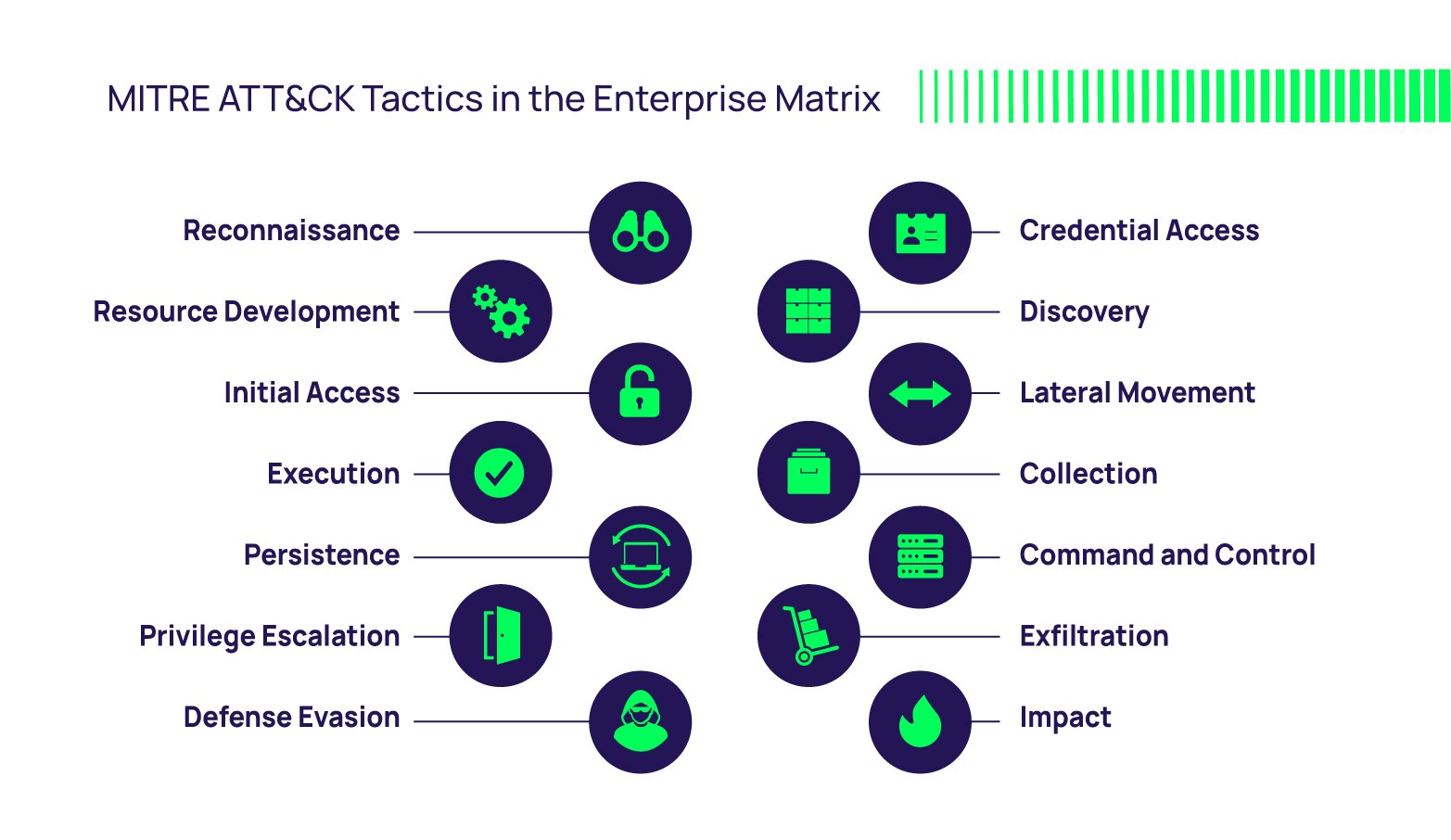 Above: Figure 1
Above: Figure 1
Since the ATT&CK Matrix for Enterprise is so big, MITRE has subdivided it into:
- PRE Matrix: covering preparatory techniques used by adversaries at the front end of the attack chain (reconnaissance and resource development: gathering victim network intel, phishing, searching open databases and websites, etc.)
- Windows Matrix: techniques commonly used to attack Windows systems.
- MacOS: techniques commonly used to attack MacOS systems.
- Linux: techniques commonly used to attack Linux systems.
- Cloud: further divided into matrices that cover techniques used to attack Office 365, Azure AD, Google Workspace, SaaS, and IaaS.
- Network: techniques commonly used to attack network infrastructure devices.
- Containers: techniques commonly used to attack container technologies.
Each matrix groups adversarial approaches according to the phases of a typical attack, such as initial access, persistence, lateral movement, and exfiltration, as shown in Figure 1. In this blog, we'll focus on the Enterprise matrix.
MITRE updated the Enterprise Matrix to version 12 in October 2022. It comprises 14 tactics and 193 techniques with 401 sub-techniques.

Download our Conversational Geek eBook and get up to speed quickly on the MITRE ATT&CK Framework
How to use ATT&CK
ATT&CK helps everyone by providing a language and a standardized way to describe and exchange cyberattack tactics used by threat actors. Techniques, mitigations, detections, etc., are assigned a unique identifier. This will enable your security personnel, red and blue teams, and forensic investigators to develop better strategies and consistent communication for thwarting, recognizing, and responding to the dangers they face.
Understanding the ATT&CK knowledge base is crucial if you're a security professional or ethical hacker. By comprehending the TTPs employed by attackers and locating potential holes in your security defenses, ATT&CK is an essential resource for organizations who want to strengthen their cybersecurity posture.
You can use ATT&CK in various methods, including blue and red team adversary emulation, threat intelligence, and detection and analytics. For example, MITRE's Caldera and Red Canary's Atomic Red Team. The latter is an open-source library of tests you can download from GitHub. You can use it to simulate malicious activity in your environment.
Many organizations have mapped their controls to the ATT&CK, such as the Center for Internet Security's Critical Security Controls. They claim to be effective at defending against 86% of the ATT&CK (sub-)techniques found in the ATT&CK Framework.
Use ATT&CK to develop your playbooks, much like cybercriminals do, to understand how they operate and what tools they use
You can utilize ATT&CK to develop your playbooks, much like cybercriminals do, to understand how they operate and what tools they use. To educate, teach, and pinpoint areas for improvement, you can utilize ATT&CK in adversarial cyber threat modeling activities like wargaming, tabletop, breach and attack simulation (BAS), and red-team exercises. MITRE has documented several common use cases on its website, such as threat intelligence and adversary emulation.
Analyze prior attacks and, along with your own CTI, match what you know to techniques in MITRE. You will likely find additional techniques you failed to discover representing gaps that your red team can emulate to test resilience going forward.
Use ATT&CK proactively as an education tool to help you shore up your defenses in specific areas by better understanding the attack chain and the typical steps in attacker playbooks. ATT&CK contains detection and mitigation recommendations to help you assess your security and identify gaps. You should, however, determine the likelihood of specific techniques being used to attack your business. Then, prioritize which security measures to implement to close gaps related to your most critical assets.
Use it reactively if you discover or suspect an incident to help forensic analysts identify the cause and emphasize tactics and processes to help narrow the scope of the investigation.
If you determine a malicious actor has used several specific techniques, you can highlight these in the model and isolate attack chains that leverage them. This can give you additional insights into other techniques used in the attack chain. A popular tool to help you in this regard is the GitHub project ATT&CK Navigator.
It's a fantastic visualization resource that provides a replica of the ATT&CK matrices found on the MITRE site but with the ability to annotate them. You can color code cells, add comments, and assign numerical values. ATT&CK Navigator allows you to visualize areas of concentration, red/blue team planning, techniques discovered and their frequency. You can also find a live instance hosted on GitHub.
Click on Create a new empty layer > Enterprise to see the familiar collection of Enterprise techniques and controls to make it your own.
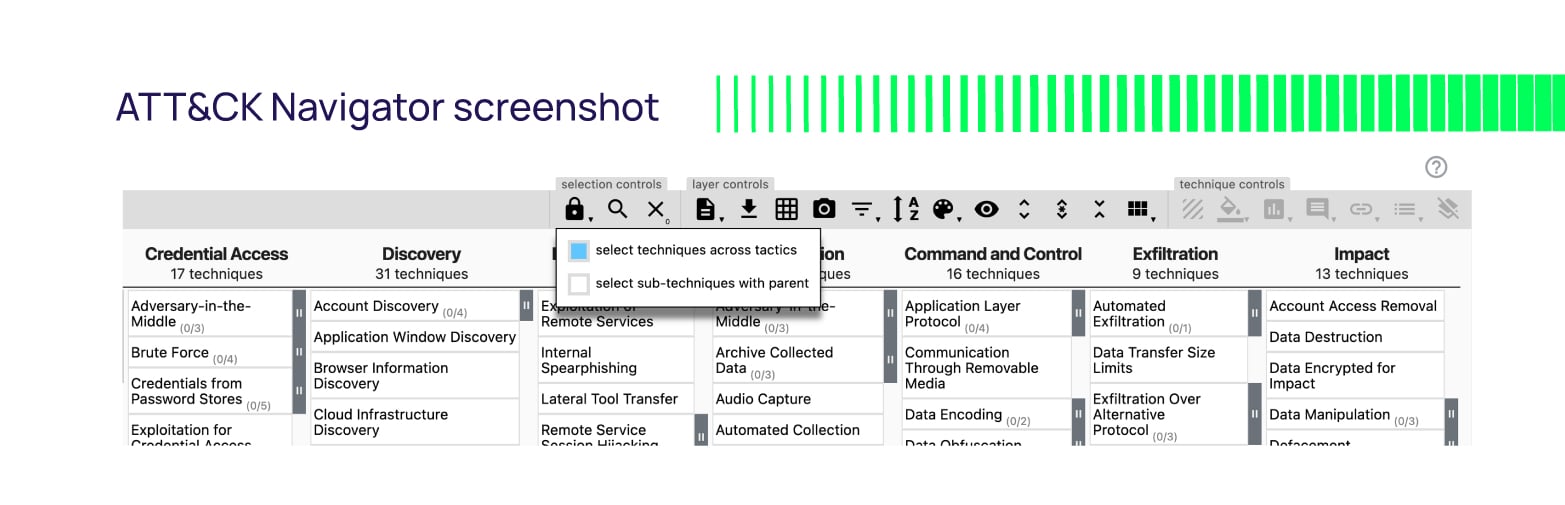 Third-party tools leverage ATT&CK data to enrich their value
Third-party tools leverage ATT&CK data to enrich their value
- MITRE-Engenuity
Want more information? You can go to the source for services and training around the ATT&CK framework. MITRE-Engenuity is a MITRE company that provides ATT&CK Defender training taught by ATT&CK subject matter experts and ATT&CK evaluations—objective analyses of cyber products and features.
They also publish a mapping between ATT&CK and NIST SP 800-53 controls. This can help you understand how the NIST controls you use in your environment relate to adversary TTPs. As mentioned earlier, MITRE Caldera and Red Canary Atomic Red Team can help you emulate adversaries with techniques from ATT&CK. - Sprinklr
At the recent RSA Conference, I attended a presentation by Sprinklr where they discussed an upcoming tool that models security controls to ATT&CK. By mapping controls to TTPs, they can semi-quantitatively understand the likelihood of TTP success during an incident. This helps in risk calculations, APT readiness assessments, and investment planning (knowing what areas are problematic to guide investment decisions). - Cybersecurity and Infrastructure Security Agency (CISA)
Government organizations such as the Cybersecurity and Infrastructure Security Agency (CISA) in the U.S. also contribute tools. CISA recently released Decider to help defenders and security analysts quickly generate MITRE ATT&CK mapping reports. - Mandiant
Several threat intelligence companies also leverage ATT&CK, mapping their findings to the Framework. Mandiant (a Google subsidiary) has mapped over 2,300 techniques to the ATT&CK framework. Its annual M-Trends report remains a good source of intel to help you understand which ATT&CK techniques and sub-techniques are most prevalent. - Scythe
Scythe is a tool on the bleeding edge for attack emulation. It helps defenders build, develop, and operate adversary emulation. It "behaves just like attackers do in the real world" and can help you anticipate which TTPs adversaries are more likely to use in your industry against your company.
Third-Party Technologies
A wide variety of third-party security technologies directly integrate with ATT&CK. Tools that draw on ATT&CK's expertise before and during incident investigations can add tremendous situational intel when needed. Here are some examples of how they use ATT&CK TTP data:
- Security Information and Event Management (SIEM) tools like Splunk, Elastic, and LogRhythm provide your teams with real-time threat detection and response capabilities.
- Endpoint Detection and Response (EDR) tools such as Carbon Black Endpoint, CrowdStrike, and SentinelOne can give you visibility into endpoint activities and help detect and respond to attacks.
- Threat Intelligence Platforms (TIP) like ThreatConnect, Anomali, and Recorded Future provide context and insights into threat actors, motives, and methods, correlating their threat data with the Framework's TTPs.
- Network Security tools like Palo Alto Networks, Trellix (FireEye), and Fortinet provide network visibility and detection capabilities.
- Vulnerability Management tools like Tenable, Rapid7, and Qualys help identify vulnerabilities and prioritize remediation.
ATT&CK is instrumental in the cybersecurity arms race
The MITRE ATT&CK framework is a precious resource developed in response to defenders' needs to understand adversaries' constantly evolving tactics, techniques, and procedures. In this war against cybercrime, you can use ATT&CK for offense as well as defense. Defender red, blue, and purple teams worldwide use this Framework to provide a more proactive approach to cyber defense.
It's a critical tool you should use directly or via third-party products that integrate with it to your benefit. In a world where defenders are too often on the back foot, this tool, along with the supporting tools mentioned earlier, helps close that gap.
Like all tools, ATT&CK is a double-edged sword that also helps adversaries. It can assist them in determining where to move next in an attack because, like us, they aren't familiar with every approach and technique. They can improve the playbooks they already have by using additional possibilities suggested by ATT&CK. Going forward, we can expect more automation around ATT&CK.
The MITRE ATT&CK framework provides us with real ways to implement offensive and defensive strategies.
Related reading: Defensive vs offensive cybersecurity



