What are the risks that come with ransomware attacks?
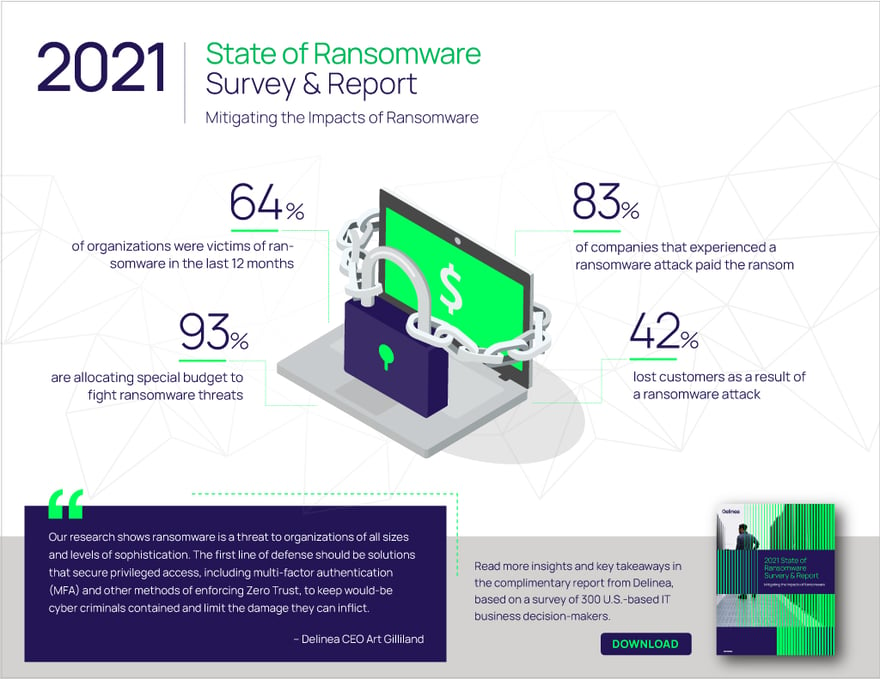
Initially, ransomware attacks focused on locking up or encrypting an organization's data and demanding money in exchange for providing a decryption key to unlock the victim’s information. As more companies than ever have been paying the ransom, usually with cryptocurrencies (which are difficult to trace), the amounts demanded have increased as well.
The message to attackers is clear. Restoring a victim’s information is good for business since many companies feel they have no choice but to pay up; they also expect to get their information back, and attackers are obliging. It’s a self-reinforcing vicious cycle that feeds on every successful attack. Recent major incidents highlighted that the success of the decryption process was poor, indicating that even if you do pay the ransom, it could take a long time before your business is back online. It is very likely that the ransomware gangs are going to improve this in future variants.
Exfiltration of critical data
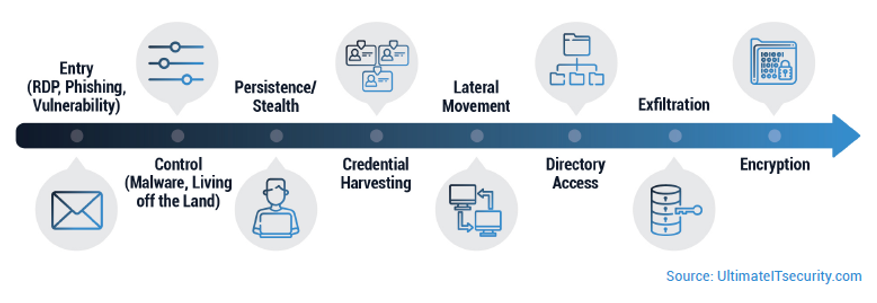
More recently, ransomware attackers use a breach to explore and traverse a network undetected to locate and exfiltrate or steal information before deploying the ransomware payload.
I have observed many ransomware cases that specifically target privileged access. Compromising a user account provides an initial foothold into the network, giving attackers a foot in the door to roam around and eventually gain privileged access. Overprivileged users, such as local administrators, are a favorite target, providing the attackers an easy way to elevate privileges to Domain Administrator accounts.
Once attained, privileged access through service accounts, local admin, or domain administrator accounts enables attackers to cause as much damage as possible. They can discover where your backups and most sensitive data are located. Taking over these types of accounts allows attackers to turn security off, create back-door access, and elevate their privileges to domain administrator status. This is especially dangerous as we are now getting to a point where many users should be considered privileged users because of the access they possess—which can be exploited by an attacker.
Compliance and regulatory concerns
Ransomware attacks can also impact regulations and compliance, triggering regulatory reporting requirements from the CCPA or GDPR. So, you must not only deal with unavailable data and systems but also personal information loss of employee or customer data, posing liability, or legal issues stemming from compliance violations.
Reputational damage
One thing I’ve seen more frequently is ransomware attackers announcing the encryption of your data on Twitter feeds. In some cases, attackers may actually be communicating with your customers directly by tagging your organization or by mentioning it in their own feeds. Thus, organizations must recognize the potential damage to their business reputation and plan for a response accordingly.