How Secure are your Linux Endpoints? An Ethical Hacker’s Guide to Securing and Hardening Linux and Unix Endpoints
Welcome to the next post in our series on hardening and protecting endpoints. In Part I, Hardening Endpoints Against Cyberattack, we covered these important steps to an ethical hack in the preparation and Open Source Intelligence gathering stages:
- Step 0: Pre-Engagement
- Step 1: Passive Recon and OSINT
- Step 2: Active Recon on Windows Endpoints
In this post, I’ll focus on Linux and Unix endpoints, and I’ll cover the Active Recon stage again as results will differ when creating your attack path.
These are the steps to an ethical hack of Linux and Unix endpoints:
Step 1 was covered in Part I of the series
Step 2: Active Recon on Unix and Linux Endpoints
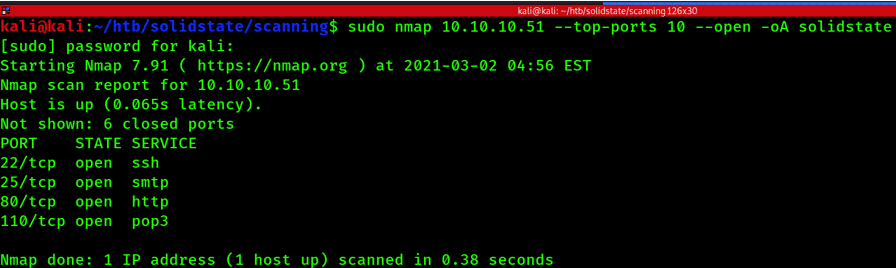
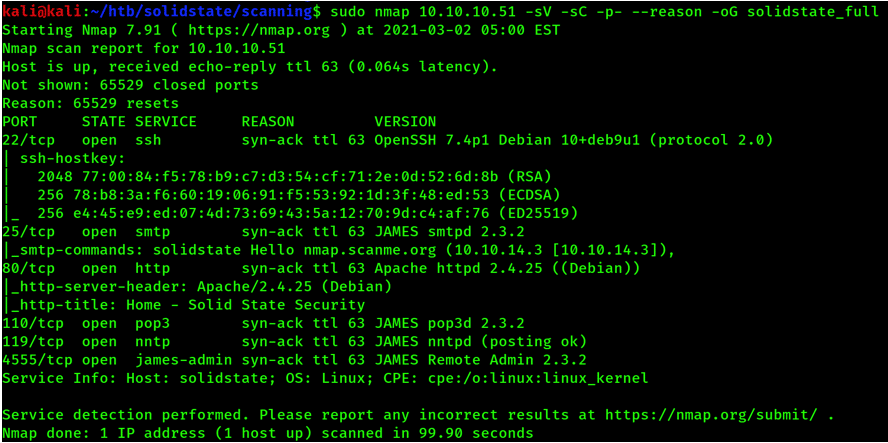
Step 3: Linux Service Enumeration
In our final post, we will cover the final step:
Step 4: Access Exploitation and the Initial Foothold
Again, if you’re interested in the planning, prep, and intelligence stages of an attack (both Windows and Linux), read: Hardening Endpoints Against Cyberattack: Part I
Or, find out how to secure and harden Windows endpoints here: Hardening Windows Endpoints Against Cyberattack: Part II
So, why would I cover Linux and Unix endpoints when most of the world’s desktop endpoints are running Windows? When I refer to endpoints, I mean all types of endpoints including laptops, desktops, and servers. Linux and Unix have a major role in the world’s computing systems and cloud. Attackers will attempt to gain access into your organization via the easiest path, and that could be either Windows or *nix (notation for both Linux and Unix) endpoints. Therefore, a strong security strategy is one that covers all the possibilities. I’m going to focus on the Linux flavor, however many of these techniques also apply to other *nix OSes.
Operating system (OS) options today are more diverse than they were 10 or 15 years ago. Since the explosion in mobile, tablets, Internet of Things (IoT), and cloud, most systems are based on the Linux and Unix family of operating systems, and of course Apple. Apple runs Mac OS which comes from the Unix family of OSs. You might not see Linux in the foreground, however, you’ll interact with Linux systems almost daily. If you drive a Tesla the in-car entertainment system is based on Linux, your smartphone might be running Android, in-flight entertainment systems most often run Linux, your home router likely enables you to connect to the internet using a Linux system, and when you shop online most of the websites you visit will be hosted on Linux Servers.