RDP Security: How to secure Remote Desktop Protocol
Many businesses use Remote Desktop Protocol (RDP) to connect remote workers with business resources including critical applications and sensitive data. RDP is free, flexible, and easy to set up, making it ideal for distributed enterprises. However, not all implementations of RDP are free, as certain features and use cases may cost money—such as personal versus commercial licenses incurred
While RDP is simple and convenient, it can also be a security risk without the proper supporting controls and configurations. Keep reading for an overview of RDP security and some tips on providing secure remote access.
What is RDP?
Remote Desktop Protocol is a proprietary communications protocol developed by Microsoft that enables remote access and management for virtual and remote desktops. It’s one of several popular remote desktop protocols on the market today that provides a graphical user interface.
The Remote Desktop Protocol creates a dedicated network channel that allows connected machines to transmit data to each other. This includes desktop displays, keystrokes, and mouse movements, among other things. With RDP, users can access company servers, log into desktop machines, and collaborate with employees from any location.
SSH vs. RDP: What’s the difference?
There are several protocols that connect remote machines and servers. But most network administrators use either Remote Desktop Protocol or Secure Shell Protocol (SSH).
List of Common Network Protocols
- FTP (File Transfer Protocol) – Port 21 – Used to transfer files
- SSH (Secure Shell) – Port 22 – Cryptographic network protocol
- Telnet – Port 23 – Application Protocol – Text-based
- RDP (Remote Desktop Protocol) – Port 3389 – Graphical Remote Desktop Interface
- VNC (Virtual Network Computing) – Port 5900 – Graphical Desktop Sharing
RDP is the most popular choice for connecting Windows systems while SSH is more closely associated with Unix and Linux environments. However, SSH integrates with just about any operating system.
The main difference between RDP and SSH is that SSH typically uses public and private key pairs instead of standard credentials for authentication. Unlike RDP, SSH lacks a graphical user interface (GUI) and instead uses text-based command-line interfacing. As a result, RDP is easier to use since you don’t need deep technical knowledge to deploy it.
Is RDP secure?
Remote Desktop Protocol is designed to enable authorized users to access data and remote systems. However, RDP security is not infallible. There are certain vulnerabilities inherent to using RDP that threat actors can potentially exploit to gain unauthorized access.
What are the vulnerabilities of RDP? Let’s take a look at several examples of RDP attack vectors:
Unrestricted port access: The majority of RDP connections use port 3389 by default. Cybercriminals often take advantage of an open port to launch sophisticated attacks and penetrate system defenses.
Brute-force credential attacks: Similarly, threat actors also look for weak or insecure user credentials that they can leverage to gain entry to systems, lift sensitive data, or deploy malware or ransomware. Typically, they’ll use brute-force attacks to gain credentials in an RDP-focused attack.
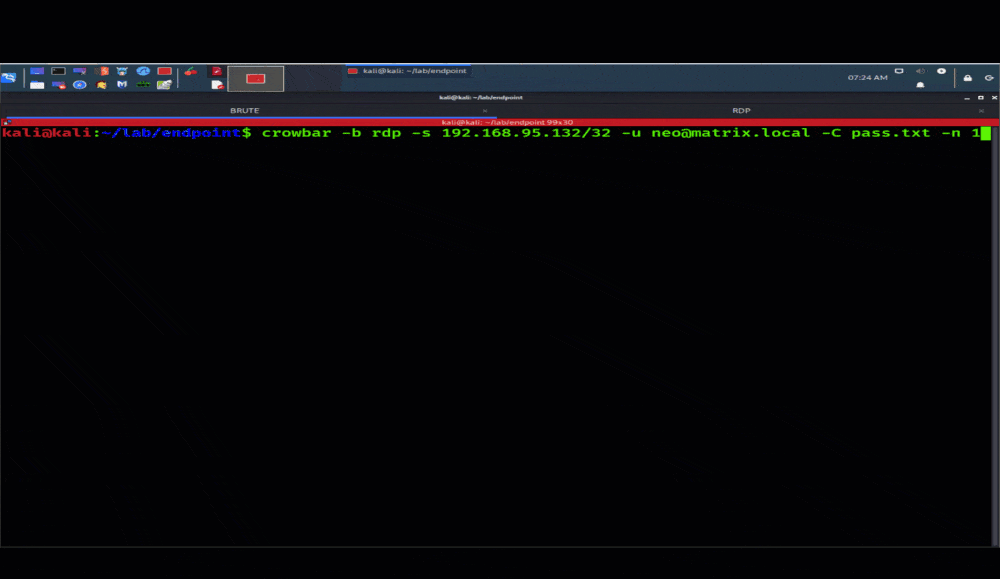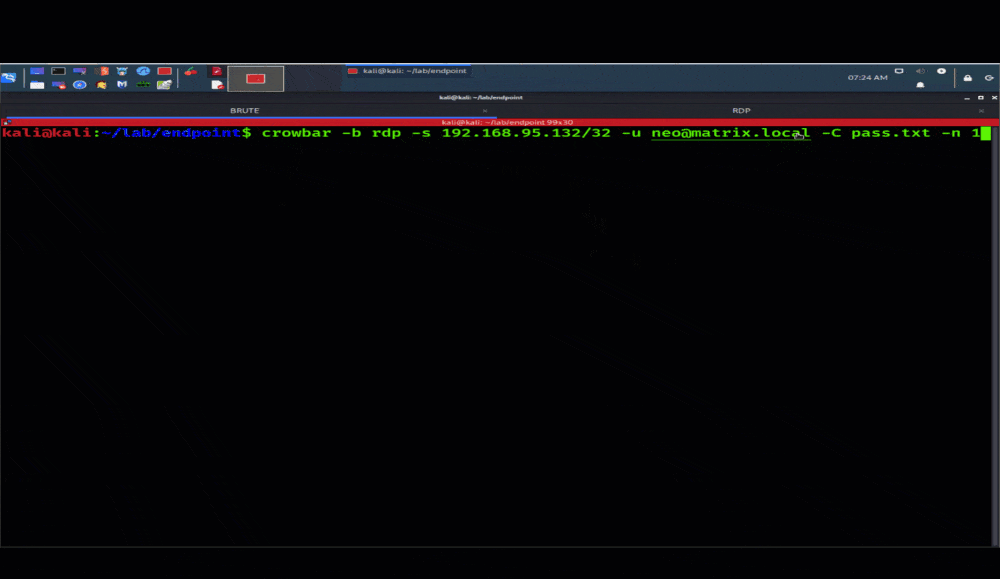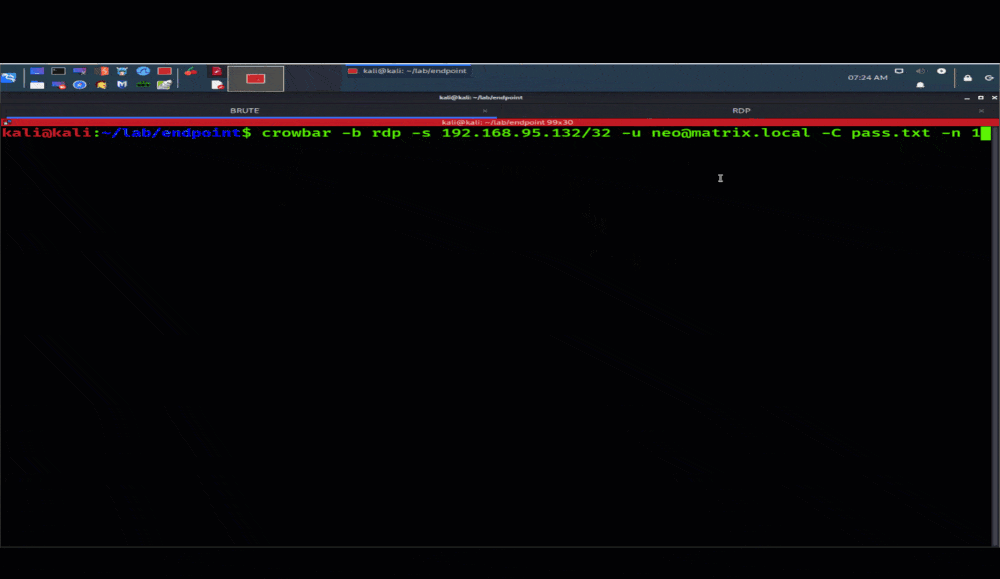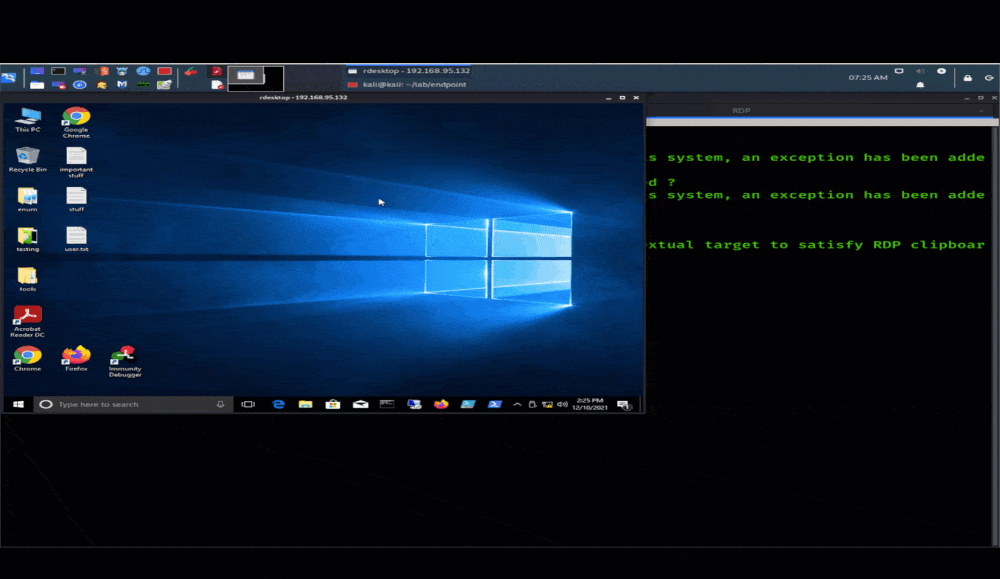
Example of RDP Brute Force Attack
Vulnerabilities for remote code execution: Attackers will also exploit RDP vulnerabilities. and RDP has several. The most recent being in 2019 which allowed attackers the possibility of remote code execution that exploited vulnerabilities such as BlueKeep (also known as CVE-2019-0708).
The bottom line is that RDP isn’t secure enough as a standalone technology. To ensure optimal protection, you need to supplement RDP with additional security measures.
How to secure RDP
As a whole, RDP security is very flexible. There are several best practices you can employ to enhance RDP security and protect your remote environment. With that in mind, let’s examine some of the top RDP security best practices.
 Secure RDP with a self-signed certificate
Secure RDP with a self-signed certificate
A self-signed certificate is a type of public key certificate that lacks a signature from a public certificate authority. You can use a self-signed certificate to set up access control policies and determine who can access systems via RDP, as well as from where they can gain access.
 Set up a jump host
Set up a jump host
A jump host is a security-hardened intermediate server that sits between a machine and the server that it’s trying to connect to. A jump host essentially acts as a barrier by restricting access to a destination server. Companies often use jump servers to verify user identities before granting access to private systems.
 Require a VPN
Require a VPN
A virtual private network (VPN) creates a private tunnel between a remote worker’s machine and the organization’s network. By extending a private network, a VPN allows users to send and receive data securely from any location as if the users are on-site. This reduces the need to make RDP public-facing on the public internet and searchable via internet discovery tools such as Shodan.
 Restrict which users can use RDP using a PAM solution
Restrict which users can use RDP using a PAM solution
Another way to secure RDP is to set up a Privileged Access Management (PAM) solution. This solution enables you to store privileged account credentials in an encrypted centralized vault and manage them through Group policies. You can configure RDP PAM policies and password lockout policies to limit access instead of granting broad-standing permissions to users. That way, if someone does get into your system through an open port, they’ll have limited ability to access additional systems, make changes, or exfiltrate data.
So, those are the basics of Remote Desktop Protocol (RDP) security.
Is it possible to manage and interact with multiple remote sessions for both RDP and SSH in a unified environment?
Yes! You can monitor, record, and control multiple remote sessions for both RDP and SHH in an all-in-one secure application. Check out Delinea’s Connection Manager to find out more, or try it for free here.
Screenshot: Connection Manager interface
Delinea Secret Server Privileged Remote Access
Modern Privileged Access Management has introduced secure and seamless methods of managing remote access beyond what RDP or SSH can offer. As companies progress in their PAM maturity, they can leverage these new remote access capabilities to remove access bottlenecks for remote workers and third parties.
Privileged Remote Access (PRA) extends the capabilities of Delinea's Secret Server, the industry’s leading PAM solution, to enable secure remote access conveniently through a web browser. For example, PRA is a powerful remote desktop alternative to RDP for securing remote access. This is especially beneficial for third-party contractors and partners who aren’t part of your Active Directory and don’t have company-issued laptops and VPNs.
So how does PRA work?
With PRA , a Remote Access Engine sits on a secure system inside your network instead of relying on a public-facing server. Users simply access PRA via a web browser, without having to wrestle with a VPN. All traffic connects to the PRA engine via HTTPS. A reverse proxy opens a port on your network exclusively for outgoing traffic—not for inbound traffic. A web launcher then connects to the target machine.
To further enhance security, Secret Server negotiates permissions and unlocks relevant secrets. Privileged access managed by Secret Server is time- and context-limited, aligning with zero trust least privilege best practices. For added security, you can integrate an authentication service such as Multi-Factor Authentication (MFA) to confirm users’ identities before granting access.
We’d love to show you how it works. As a next step, learn more about PRA for remote access that improves security, removes bottlenecks, and simplifies management for your IT team.
Related reading: SSH Proxies vs Jump Hosts | Secure RDP within a PAM Solution
What does cybersecurity like this cost? Not as much as you think


