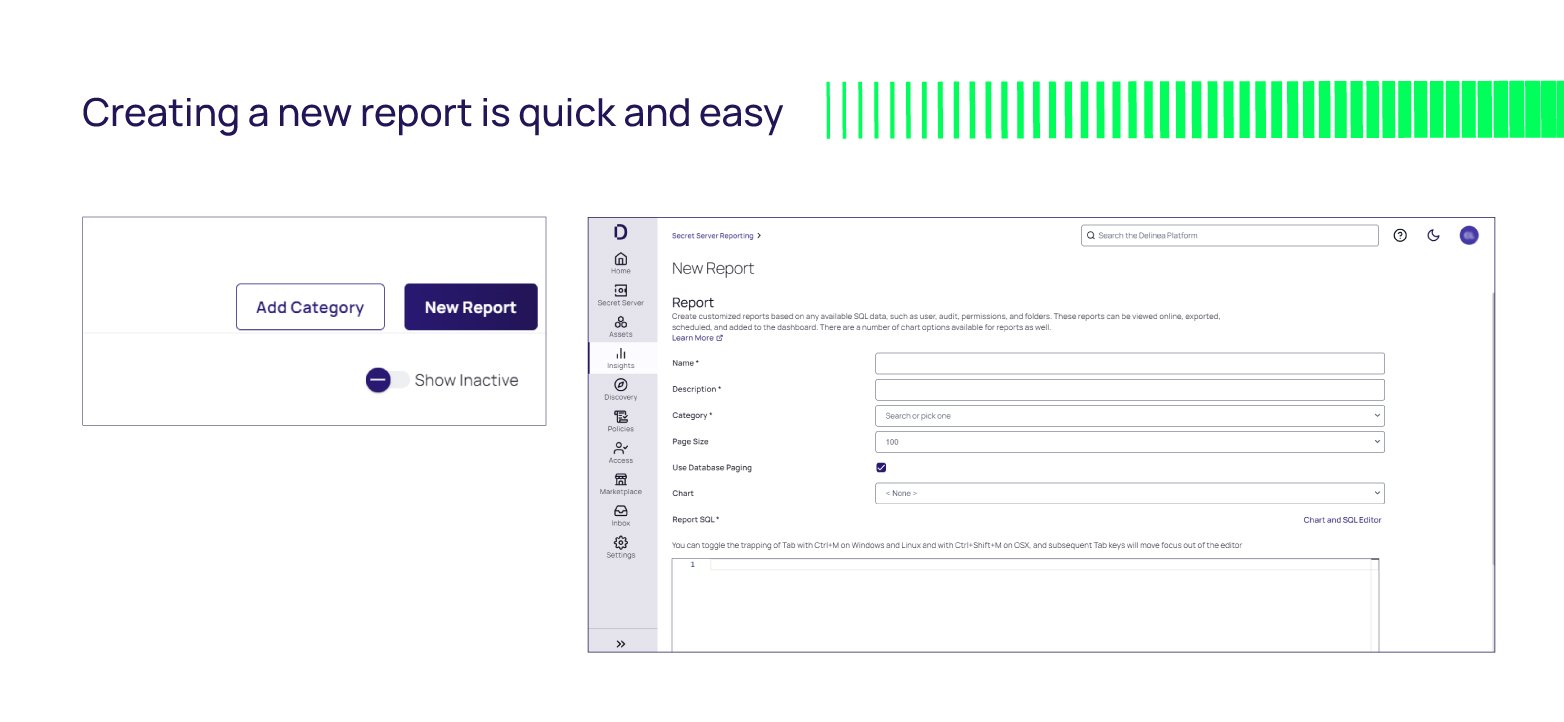
What’s privileged access reporting got to do with time, money, and security?
Privileged Credential theft is still one of the primary causes of successful cyberattacks. When a bad actor is at your digital door, it’s a race against time to get that door locked.
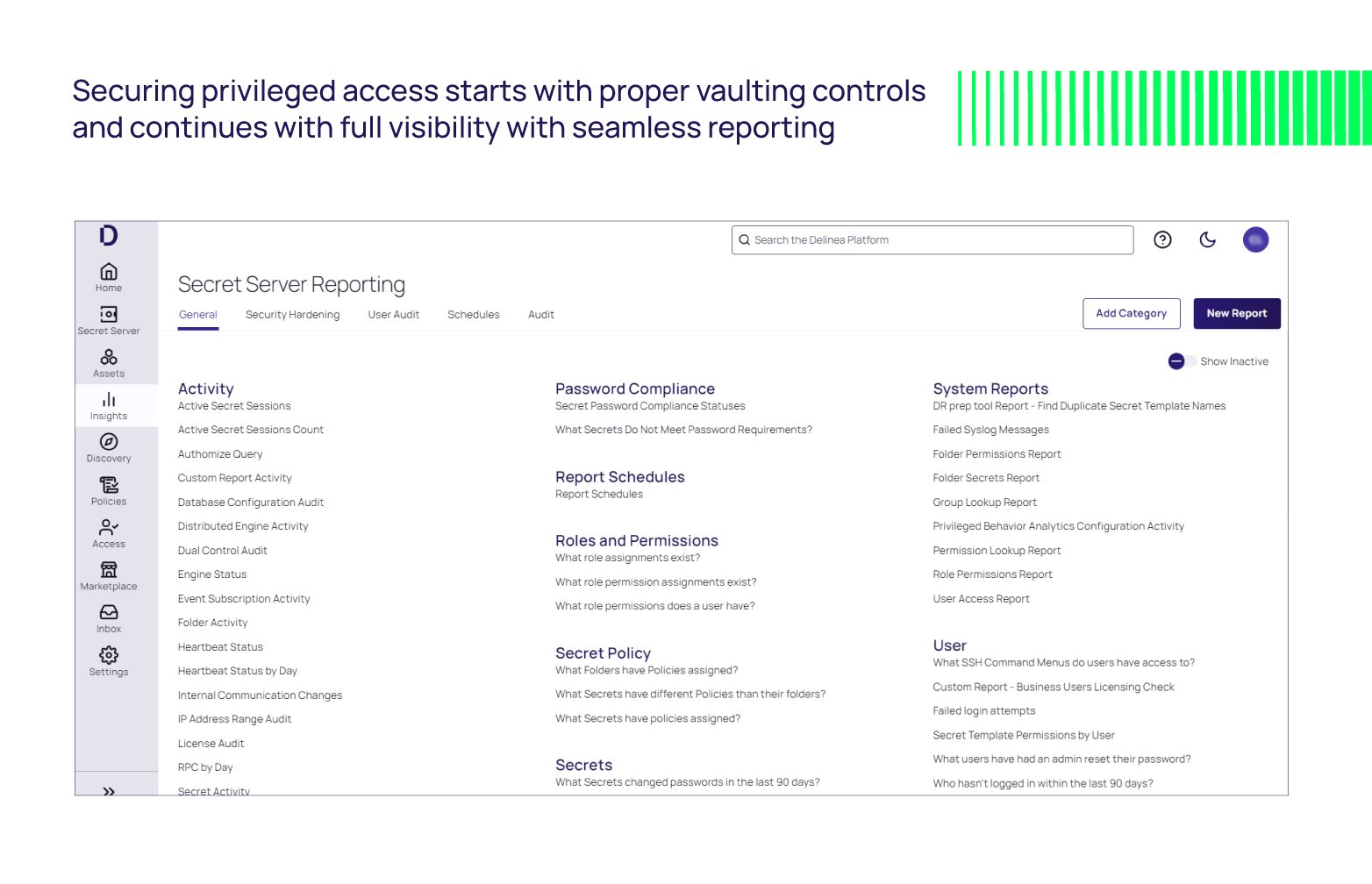
Securing privileged account credentials in a vault is your first priority. However, visibility to the right reports at the right time makes it easier for Privileged Access Management (PAM), Identity and Access Management (IAM), and Infosec teams to proactively monitor privileged accounts to mitigate risk while focusing on business-critical projects.
Unfortunately, reporting on privileged access activity has become cumbersome, expensive, and time-consuming. This makes it nearly impossible for teams to control internally, creating a gap in security posture for many organizations.
Modern PAM vaults secure privileged account credentials while proper reporting and access controls ensure all users adhere to proper PAM hygiene and policies, helping reduce gaps in secure access.
Save time with out-of-the-box audit reports
Do you know which of your users have elevated privileges? Have any shared Secrets been copied to a different folder? What secrets have changed or have not changed their passwords in the last 90 days? What Secrets have been accessed by an impersonated user?
Administrators are moving at a digital speed to keep organizations secure, and starting reports from scratch can create barriers to success and gaps in secure access. Out-of-the-box (OOB) templates and audit reports quickly provide insight into all actions on any privileged account.
Delinea’s Secret Server has over 90 Out-of-the-box reports that can easily be customized per your requirements for additional data, saving teams countless hours of time and frustrations.
These OOB reports are SQL-based, so creating new reports is just a simple SQL query. This makes it easy to secure access to credentials, keep teams productive, and maintain visibility for all privileged access activity.
Administrators can quickly prove PAM security to all stakeholders and auditors by running Risk assessment reports regularly, including:
- User Access Report
- Role Permissions Report
- Who hasn't logged in within the last 90 days?
- Group Membership Report
- Unlimited Administrator or Break Glass Account behavior
Two specific reports most administrators look at regularly to evaluate risk are the User and Secrets activity.
Audit reports on Users or Secrets activity:
This level of visibility into User and Secrets activity ensures passwords are used properly and makes it easier to reduce risk quickly. For example, when someone leaves your organization, the team can pull a report to gain full visibility into every Secret the user accessed. For those of you who are SEC-regulated, this easily accessible report helps to demonstrate SOX compliance.
Because every organization is unique and their reporting expectations differ, out-of-the-box (OOB) templates and flexible reporting functionality are critical to keeping privileged credentials secure, teams productive, and organizations ahead of bad actors.
Administrators should close any security gaps by paying close attention to users with elevated privileges.
For example:
- IT Administrators or Developers with system-level access—do they still need this access?
- Ephemeral Users or Contractors who should have had temporary access—do they still have access? Has their role changed?
Without proper monitoring and auditing, this unused access could be used as a gateway to your systems.
Save money with Automation and Event Subscription Reports
Efficient PAM administrators leverage as much automation as possible, including scheduled reports to be auto-generated and delivered regularly or based on an action.
Administrators who like to save time can streamline their review with reports delivered only when that report has content, thus avoiding unnecessary disruptions. This option keeps admins focused on business-critical projects while proactively monitoring privileged access with immediate alerts.
For example, these reports can be set up to target unusual events, such as when a user views more than 50 secrets in one day, failed heartbeats, configuration changes, and more.
OOB Event Subscription reports make it easy to get started with:
- Unlimited Administration Mode toggle
- Secret Edit/Add/View
- Role and Group Assignment changes
- Secret expiration
- Configuration changes
- Heartbeat failure when a password is invalid
It’s important to note that:
- Automatic Heartbeat reports, for example, must be included in this category to mitigate risk and close any gaps quickly.
- Secret Server reports sent on a schedule or targeted action based on your need demonstrate competence, security, and compliance without disrupting teams.
Modern Privileged Access Management solutions provide the necessary visibility and control capabilities to help PAM administrators secure privileged access without relying solely on expensive and time-consuming outside security services.
The PAM market has evolved, and the old, cumbersome, costly way to get reports is no longer feasible. PAM, IAM, and Infosec teams expect a modern reporting functionality that works the way they work to keep their teams efficient and productive while controlling costs.
Having access to auditing and reporting data has everything to do with time, money, and security. Do you have what you need, when you need it?
Experience Delinea Secret Server today! The easy-to-use, manage, and implement Enterprise Vault.


