Identity Security Maturity Model
Challenge
As identities and entitlements multiply across environments, enforcing least privilege access becomes increasingly complex.
Risk
Without authorization controls, over-provisioned identities and compliance gaps increase risk.
Solution
Implement a structured Identity Security Maturity Model to enforce least privilege, continuous discovery, and adaptive access governance.
The Identity Security Maturity Model
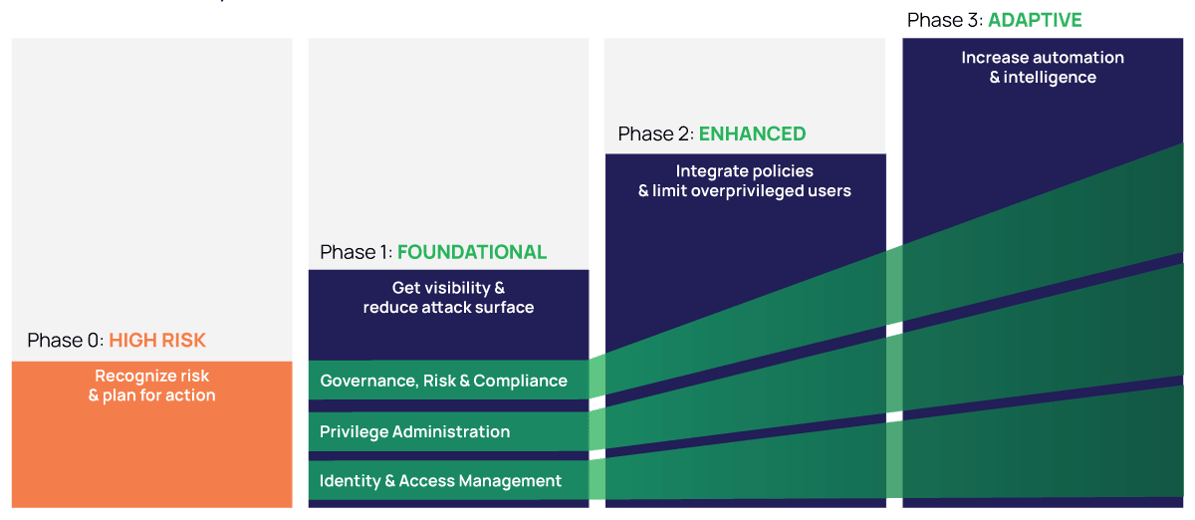
Step-by-step framework for reducing risk
Authorization is core to identity security.
The Identity Security Maturity Model helps you assess your current practices, prioritize next steps, and guide investment in key authorization controls.
Build a practical roadmap that aligns with your identity security goals andcompliance needs, while keeping your business agile.
Informed by 10,000+ companies
The maturity model draws on identity security best practices and Delinea’s work with organizations at every stage of maturity, from those just starting their identity security journey to the most advanced programs.
The scope expands to include more types of identities and privileged accounts.
Intelligence and automation advance, enabling you to continuously learn and adapt your strategy.
Controls become more granular and dynamic to govern, validate, and automate access with precision.
Integrations embed identity security directly into your workflows, making controls virtually invisible to most users.
Identity security maturity is multi-dimensional
Each phase of the Identity Security Maturity Model helps you evaluate your level of maturity according to three factors:
Governance, Risk, and Compliance (GRC) – How strong is the integrity of your system, and how much visibility and oversight do you have?
Privileged Administration – How do you create, define, and manage identities across your organization?
Identity and Access Management (IAM) – How strong are your authoentication controls and how granular are your authorization controls?

What's new in identity security
Learn to protect your most critical systems and data with these free, in-depth identity security resources.
Search our library of webinars, videos, whitepapers, case studies, and more to get started with your identity security or PAM strategy. Get the most from Delinea's solutions, and hear inspiring stories of cybersecurity success from companies just like yours.
Assess your maturity level and learn about the identity security controls recommended for each phase and dimension—all at a glance.
Download the matrix
Explore the Identity Security Maturity Model for detailed guidance and practical steps to expand your identity security program and reduce your risk.
Download the whitepaper