Guide to Network Security and Hardening
Network hardening is a security strategy at the top of every CISO’s list. It’s a topic that's become more complex and dynamic as the very definition of the network has changed.
The network infrastructure, a chain of connected highways for data to move at high-speed, is essential for business services to operate efficiently. When network infrastructure is breached, sensitive data can be exfiltrated, services can be interrupted, and your business can cease to operate.
Network security includes the underlying protections that safeguard your infrastructure from malicious access and misuse. Traditionally, network hardening techniques have focused on firewalls that block unauthorized outsiders from gaining access to networked corporate resources. Think of those traditional approaches to network security like building a moat around a castle.
Traditional approaches to network security are like a moat around a castle; today, the line between inside and outside the castle is no longer clear
Today, the line between “inside” and “outside” of the castle isn’t as clear as it once was. Organizations have resources on-premise, in private clouds, and in public clouds. Plus, third parties and employees are accessing corporate networks from remote locations.
With traditional networks, you could manage and secure all the network highways. You no longer own most of those highways, such as the cloud network infrastructure or employee home networks.
Due to this lack of direct network highway control, network security requires multiple layers of defense from the network edge to the core. That includes ensuring identities, devices, applications, data, and systems (such as servers and workstations) are protected from unauthorized access at every point. Network security strategies must stop the bad guys from entering the network and prevent them from traveling once they’re inside.
Network hardening techniques include ensuring your firewall is set up correctly, regularly checking its rules, prioritizing securing access points, and managing user permissions. They also utilize access lists to monitor and grant network privileges, close unused network ports and safeguard your network traffic by minimizing unessential protocols and services, and always encrypting the flow.
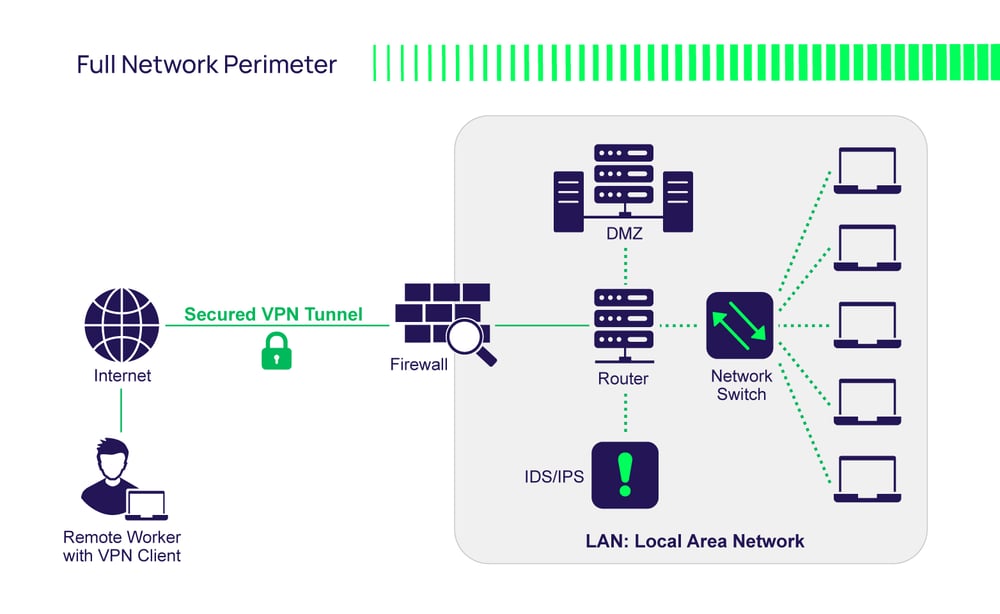
Network components to harden and secure
The network is typically made up of components that enable access and support the flow of data. All of these components must be considered in your network security strategy.
 Endpoints: Devices where users, data, and applications interact with the network, such as:
Endpoints: Devices where users, data, and applications interact with the network, such as:
- User workstations such as desktops and laptops
- Mobile devices such as smartphones and tablets
- Servers
- Smart devices that are part of the Internet of Things (IoT)
 Network switches: These are network devices that route traffic within the Local Network and enable endpoints to be connected to the network.
Network switches: These are network devices that route traffic within the Local Network and enable endpoints to be connected to the network.
 Routers: These are network devices that manage and route traffic across different networks including to and from the internet.
Routers: These are network devices that manage and route traffic across different networks including to and from the internet.
Top threats and risks of unprotected networks
There are many threats that organizations are exposed to when networks aren’t protected or hardened. Once attackers gain initial access, they can move around the network undetected, allowing them to carry out malicious activities such as:
- Deploy malware or ransomware
- Install viruses or spyware
- Phish to steal credentials or deploy malware
- Compromise business email
- Steal and exfiltrate sensitive data
- Execute DDoS (Distributed Denial of Service) attacks
- Perform financial fraud
Securing your network the old-fashioned way
In the past, organizations typically used several network security strategies to protect the network from authorized access via the public internet:
 Firewalls: The primary security role of the firewall is to filter inbound and outbound traffic with predefined rules/policies that allow or deny traffic.
Firewalls: The primary security role of the firewall is to filter inbound and outbound traffic with predefined rules/policies that allow or deny traffic.
DMZ (Demilitarized Zone): The DMZ is a buffer zone between the public internet and the local area network (LAN), which provides a layer of security between trusted and untrusted networks.
 Intrusion Prevention Systems (IPS): This network security tool monitors network traffic for malicious activity. Depending on the prevention rules, it can report, block, or drop traffic to protect the network.
Intrusion Prevention Systems (IPS): This network security tool monitors network traffic for malicious activity. Depending on the prevention rules, it can report, block, or drop traffic to protect the network.
 Intrusion Detection Systems (IDS): Like an IPS network security tool, IDS detects malicious activity and alerts when detected.
Intrusion Detection Systems (IDS): Like an IPS network security tool, IDS detects malicious activity and alerts when detected.
 Virtual Private Networks (VPNs): A VPN enables a private network connection between endpoints and networks, adding an additional level of encryption to ensure the traffic cannot be intercepted by unauthorized access. VPNs are good for encrypting traffic but not efficient for managing access for large groups of employees.
Virtual Private Networks (VPNs): A VPN enables a private network connection between endpoints and networks, adding an additional level of encryption to ensure the traffic cannot be intercepted by unauthorized access. VPNs are good for encrypting traffic but not efficient for managing access for large groups of employees.
Network security in 2022 and beyond
The issue with relying entirely on the traditional network security strategies listed above is that the network is no longer clearly defined. As a result of cloud, mobility, connectivity, and remote working, the modern corporate network is basically cloud workloads and services being delivered over the public network.
The world has accelerated quite a bit from the Bring Your Own Device (BYOD) model, in which employees brought their own devices onto corporate networks. In that model, to secure your networ,k you might have segmented those personal devices from the managed corporate network by enabling secure access to business services and applications with strict policies and security controls that limited what each device could access. (Unfortunately, some organizations didn’t even go that far, resulting in a mixture of corporate and personal devices being introduced into the network.)
Today, BYOD has evolved further into Bring Your Own Office (BYOO). Remote workers now access business services and applications directly from their home networks.
As a result of these shifts, the security of your workloads and services must change. To secure the modern network, you must move beyond traditional network hardening techniques and strategies.
15 network security best practices
The following 15 steps are essential best practices to harden your network against unauthorized access and abuse.
1. Asset inventory and software audit
It’s critical to have full visibility of what’s on your network—traditional on-premise or cloud. Continuous audit and discovery ensure you know when new devices or software are introduced on your network so you can monitor for suspicious activity.
2. Secure physical access
Always ensure that your network infrastructure isn’t easily accessed by unauthorized employees or visitors. Physical access continues to be an important security control to prevent malicious actors from adding malicious devices onto the network to enable reverse shells or remote access.
3. Scan for open ports
Audit and check your network for open ports to discover what network services are enabled. One of the most common techniques used by attackers is to scan for open ports to identify possible ways to gain network access. By knowing your open ports, you’ll also know how an attacker sees your network and systems.
Check out Hardening Your Systems and Endpoints Against Cyberattacks. This multi-part blog series covers some of the most common techniques attackers use to gain access and elevate privileges. It includes details on how attackers scan and enumerate open ports to determine what is running on systems and possible system vulnerabilities.

4. Manage and audit firewalls
A firewall’s job is never done. Periodically review firewall configuration, rules, and policies. Ensure that only authorized employees can access your firewall and protect administrative access with a Privileged Access Management (PAM) solution to ensure that access is controlled with the highest security requirements.
5. Network segmentation
I can’t emphasize enough how important segmentation is as a critical network hardening strategy. Network segmentation enforces policies and security controls so that only users and devices with authorized access can use certain parts of the network, whether on-premise or in the cloud. A flat network is easier to manage but also represents a very high risk of attackers bringing your business to a complete stop.
While segmentation is important, it’s only as good as the security controls that protect access to and within each segment. For example, you’ll want to keep your backup systems on a separate network and limit access between the production network and the backup network.
See how one of the largest hospitals in Canada implemented network segmentation as part of its security strategy. They used Microsoft’s credential tiering system, known as Privileged Access Workstation (PAW) to create an isolated virtual zone in which sensitive accounts can operate with low risk.
6. Remove unused devices
As part of your audit and inventory discovery process, always look for unused devices that are no longer required by moving them into a deprovisioning process. Unused devices on the network typically get forgotten and are often left with vulnerabilities such as weak credentials, becoming prime targets for attackers to gain access and elevate privileges.
7. Audit and monitor all network access
Know your network by monitoring network access requests and trying to detect unusual or suspicious activity. This can result in lengthy logs of activity so try to use smart filters and machine learning to detect abnormal activity. Not only is it important to audit and monitor the access but also to archive access so when a security incident occurs, you can investigate the logs later.
8. Patch and update security
Patching systems should be done based on the severity and risk of vulnerabilities. Not all patches are equal, so evaluate each based on your business risks. Automate as much as possible.
9. Remove unused software and services
Periodically review your service lifecycle and software catalog to determine which services and software can be removed. Unused services and software can be a high risk to the business, especially when left unpatched or not updated to later versions. This can leave weak configurations, default credentials, or vulnerabilities that can open doors for attackers to gain unauthorized access to sensitive systems and data.
10. Manage and restrict admin access
Attackers are always looking for admin access, especially credentials allowing full network access that enable an attack path to elevate privileges. Remove and revoke excessive admin privileges regularly. Practice the principle of least privilege and move to just-in-time (JIT) privilege elevation.
Download Delinea’s eBook on implementing least privilege cybersecurity:

Start your least privilege journey here
11. Multi-Factor Authentication (MFA) everywhere
Enforcing MFA at the network perimeter is no longer enough. If attackers gain access to the network and the only remaining security controls are passwords, it’s only a matter of time before that attacker owns the entire network. It’s important for critical systems and network infrastructure to implement MFA at depth. Don’t assume that just because the access request is coming from within your network, it should be trusted.
Check out Delinea's blog on MFA at depth.
12. Privileged Access Management
An essential part of network hardening is to secure and manage privileged access on your networks. This means deploying a Privileged Access Management solution that enables you to protect privileges with solid passwords, auditing, security controls, and policies.
Check out Delinea Secret Server and start a 30-day trial for free:
IT security should be easy. We'll show you how
13. Backup strategy
A strong backup plan is essential for network hardening and resiliency. Ensure your backup is protected from unauthorized network access and keep it segmented from production.
14. Secure remote access
All access to your network must be continuously verified, authorized, and secured. Ensure that passwords aren’t the only security controls protecting access to your networks. Combining Identity and Access Management (IAM) with Single Sign On, Multi-Factor Authentication, and strong Privileged Access Management will provide your network with strong access controls that will force an attacker to take more risks. The attacker will then be detected, or they’ll move on to other, easier targets.
Check out how secure remote access can integrate with your PAM solution to allow remote workers and third parties to access your network securely without the need for a VPN.
15. Zero trust network strategy
Don’t automatically trust devices or access on your network. Practice a zero trust network security strategy so that all devices must continuously verify authentication requests and authorization.
Learn more about zero trust privilege with Delinea's eBook:

FREE EBOOK
Decrease your risk of a breach with a modern PAM solution founded on zero trust principles