Mandatory MFA at depth: The Benefits of Stronger Authentication for Cloud Environments
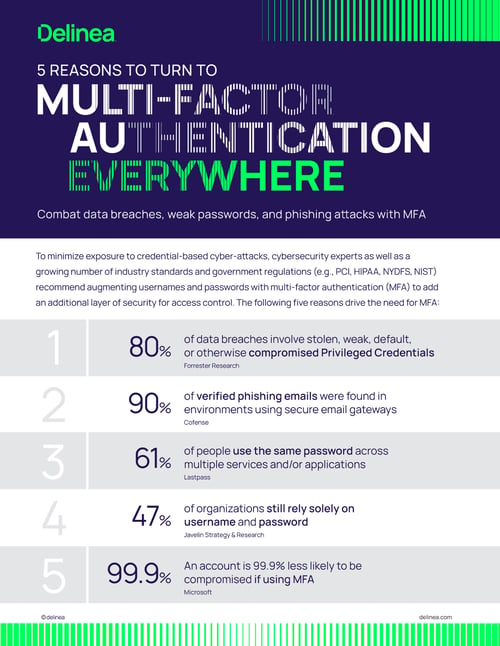
One of the biggest security threats today is the risk of compromised credentials and misuse of privileged accounts. Organizations of all sizes and verticals recognize the need to protect access to their applications, servers, and infrastructures. However, it is often hard to distinguish between a legitimate admin presenting a legitimate ID and password versus a threat actor using compromised credentials.
The threat is no longer only from humans but also bots and malware, making it more challenging to make proper identity decisions. Many organizations struggle with how to do this comprehensively across their distributed infrastructure.
As security professionals, our job is to put up barriers to reduce cyber risk exposure from external and internal threat actors. One of the most effective and easy-to-implement best practices is to enforce multi-factor authentication (MFA) everywhere, requiring additional validation steps for extra identity assurance when hosting your applications in the cloud.
MFA is an easily added layer of security for administrator access. By making it mandatory, we can automatically block many malicious sign-in attempts.
One of the most effective and easy-to-implement best practices is to enforce multi-factor authentication (MFA) everywhere
Regulated industries such as financial services, healthcare, and e-commerce industry verticals are under regulatory pressures from several bodies (such as PCI, HIPAA, PSD2, DFARS, NIST, etc.) to implement MFA for privileged access. MFA is now mandatory for cyber insurance requirements to prevent unauthorized access to servers, workstations, and remote desktops. And of course, MFA is an integral component of best practices such as zero trust and zero standing privileges.
According to Gartner, enterprises that rapidly expand remote access without implementing MFA will experience five times as many [account takeover] incidents as those that use MFA.[1]
Improper configuration and maintenance of critical accounts in the multi-cloud environment can lead leave your organization vulnerable to cyberattacks. Implementing a modern MFA across your on-premise and cloud environments is an effective defensive layer against account compromise. With a rising demand for cloud-based MFA solutions and services, it helps to gain deeper insights into how different forms of MFA can increase your cybersecurity maturity.
Adaptive and Behavioral MFA
As we double down on cloud cybersecurity with multi-factor authentication, it is essential to know how you do MFA can make a difference in finding the right balance between security and usability.
Are you following the traditional MFA approach, or stepping up to adaptive and behavioral MFA?
- Traditional or legacy MFA solutions use static rules to define the MFA prompts that lack the ability to authenticate in the dynamic context. The static approach forces everyone to follow similar rules under all circumstances and fails to measure risk accurately.
- Then we step ahead to contextual MFA where the context needs to be defined, such as from which location, device, or network you're logging in. This method requires more care, feeding, maintenance, and upkeep, and all possible risky conditions may not have been considered.
- A much more innovative and secure approach is behavioral MFA that adapts to the changes in user session behavior to block or grant access. Delinea Server PAM solutions also support risk-based MFA using modern machine learning algorithms and behavioral analytics to carefully examine a privileged user's behavior and identify "anomalous" or "non-normal" (and therefore risky) activities. Machine learning can scrutinize millions of events continuously, which would never be achievable by manual forensics. This analysis is fast, allowing Delinea’s Server PAM solutions to determine risk and react in real-time.
Adaptive and behavioral controls not only notify of risky or rogue activity in real-time but are also able to actively respond to incidents by cutting off sessions, adding additional monitoring, or flagging for forensic follow-up.
Besides applying MFA across the different privileged activities, organizations should also enable MFA across all sensitive resources like password vaults, firewalls, network devices, workstations, and servers that reside on-premise or in the cloud.
Let’s dig into the where all MFA enforcement is a must-have.
Mandatory MFA at depth
When you think of MFA, the first use case that pops up is admin access. MFA must be mandatory for IT admins or privileged users who have access to sensitive data and systems.
A best practice is MFA that supports the National Institute for Standards and Technology (NIST) Authenticator Assurance Level-2 (a minimum of two factors) and ideally Authenticator Assurance Level-3 (one of the factors is a hardware crypto device) for admin functions.
Many PAM vendors only support MFA at vault login. However, MFA at password/secret checkout, server/system login, or privilege elevation is far more secure, reducing the risk of privilege abuse. If an adversary manages to obtain a valid ID and password and use it to log in to a server or elevate privilege, MFA can stop that attempt in its tracks. While in possession of the valid credentials, it’s unlikely the attacker (human user or bot) will have also compromised the second factor, such as a mobile phone or YubiKey dongle. Thus, enforcing MFA at all main access control gates will reduce the risk of an attack succeeding.
Enforcing MFA at all main access control is a reliable deterrent and ultimately minimizes the risk of lateral movement of threat actors
Many organizations use MFA products from different vendors deployed in different places. This results in inconsistent policies, gaps in security, and administrative overhead. Delinea’s Server PAM solutions mitigate these risks by providing a centralized management UI for MFA policies. MFA policies for server login and privilege elevation can be centrally defined and managed and enforced on the server by Server PAM clients.
Our Server PAM solutions support all the leading vendor solutions such as Duo, YubiCo, and RSA, with built-in support for common protocols such as RADIUS and FIDO2 and a Delinea app that supports push notifications and OATH OTPs. Support for a broad range of authenticators provides flexibility to your IT staff, and supports MFA across the enterprise for access to AWS infrastructure, at password checkout, session initiation, server login, or when elevating privilege.
Check out our MFA demo—Vault Login to Server Login—to see how multi-factor authentication can be used wherever access control decisions are made.
MFA is one of the most effective and easiest on-ramps for PAM, providing a lot of value with minimal effort. MFA also continues to evolve, offering peace of mind that critical administrative access points are well protected. By adopting an approach where MFA is used everywhere possible, organizations can establish a reliable deterrent and ultimately minimize the risk of lateral movement of threat actors across their networks and add an effective identity assurance layer to cloud security defense.

Not all MFA solutions are created equal
Additional resources:
Best Practices for Verifying Privileged Users with MFA at depth
Adaptive Multi-Factor Authentication for Privileged Access (PDF)
________________________________________
[1] Gartner, “Enhance Remote Access Security with Multifactor Authentication and Access Management,” Ant Allan, Michael Kelley, Rob Smith, 06 May 2020.