Granular Access Controls or Productivity? You don’t have to choose
Let’s talk Multi-Factor Authentication (MFA), stolen credentials, and evolving expectations. With bad actors doubling down on accessing your system with stolen passwords, you can no longer rely on credentials alone to verify users.
But what’s the alternative? MFA with every click? You get an MFA challenge, and you get an MFA challenge, and you get an MFA challenge—everyone gets an MFA challenge! Not a great way to keep teams productive and users efficient.
So, what are you supposed to do? If users get hit with an MFA challenge for EVERYTHING, at every click, it becomes too difficult, too cumbersome, and too inconvenient.
Users are likely to circumvent those cumbersome processes. Security protocols only work if they are followed. As a result, an increasing number of organizations are adjusting how they think about secure privileged account access with a strategic mindset.
Secret Server’s MFA on Secrets is a new direction to ensure organizations remain seamlessly secure
Granular privileged access controls with purpose
According to the State of Authentication report, 84% of IT professionals consider authentication & access management one of their top priorities. With 80% of cyberattacks focusing on privileged credentials, it’s no wonder IT teams are worried about getting authentication right. Organizations need to look beyond credentials.
But what if credentials became less of a worry? What if stolen privileged account credentials were just a big issue and not a path to a catastrophic and costly breach? What if you could have seamlessly adaptive and dynamic granular access controls on designated privileged accounts based on specific triggers?
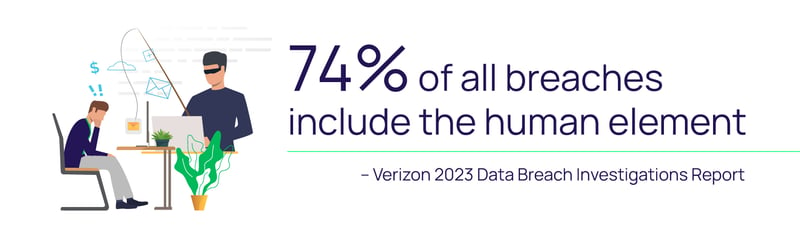
All of this can be achieved with a strategic and balanced authentication process.
As we move forward with granular access controls and beyond traditional MFA expectations, your privileged credentials vault should lead the charge. And you all have an easy-to-use PAM vault implemented and in place—right?
MFA on Secrets is the next level of granular secure access controls. By putting layers of authentication between bad actors and your designated privileged accounts at the secrets level, your teams will experience seamless continuity.
Gone are the days of privileged credential vaulting for vault’s sake—no one has the time or the budget for a ‘one hit wonder’ in their tech stack. Your Privileged Access Management vault should seamlessly push out an MFA challenge based on the Secret being accessed while keeping users productive and efficient. Granular access controls on the Secret level does just that.
IT security should be easy. We'll show you how
Granular access controls when and where needed
According to the Verizon 2023 Data Breach Investigations Report, using stolen credentials remains the most popular entry point for a breach. Stolen credentials, along with bad actors using MFA bombing, SIM-swapping, and man-in-the-middle attacks make it difficult for organizations to stay secure with confidence.
Overusing authentication at every turn to keep your organization secure can kill productivity and innovation, leaving gaps in your attack surface. Granular access controls in Secret Server on the Secret level give you the best of both worlds—secure complex and, at times, invisible credentials, plus next-generation MFA with granularity and seamless implementation for the user.
MFA on the Secret level puts your team back in control of secure privileged access for your most highly privileged accounts without slowing them down. An extra layer of protection with focused and strategic implementation is a good thing. With increasing cyber insurance requirements, having strong controls and layered authentication is an advantage.
So let me paint a picture: a bad actor steals credentials, and to their excitement and surprise, they are credentials to a highly privileged account. As the bad actor is typing in the password to execute their nefarious plan, they are thinking about all the cryptocurrency they are about to steal. But wait! The bad actor launches the Secret, and they get another MFA challenge. This one is different from the MFA at login that they already bypassed—their attempt has been thwarted!
The Delinea team is laser-focused on keeping you ahead of bad actors by keeping you faster, more secure, and more innovative than they are. Granular controls that you implement when and where you need them is another way we simplify PAM security with the least privilege policy on Secrets in Secret Server. It allows you to configure MFA on Secrets as needed to align with or distinguish from other MFAs used. MFA on Secrets offers a passthrough with a restricted timeframe. Even with all these granular controls, your teams stay productive.
 Delinea leads the innovation front, according to the Frost RADAR report
Delinea leads the innovation front, according to the Frost RADAR report
Granular access controls can co-exist with productivity
OK, let’s bring it all together now.
Secret Server continues to lead the innovation front for PAM vaulting so you can stay focused on securing what you need to—how and when you need to.
We all know that if security measures are not easy to work with, users will attempt to bypass them. This is where the rub is—the more authentication you have, the more secure you are, but productivity and efficiency suffer, which means users will circumvent that security! We have elevated what the market expects from PAM and what IT and Security leaders expect from their PAM vault.
You don’t have to choose between security on a privileged account and productivity—you get them both with seamless MFA on Secrets. MFA on Secrets in Secret Server on the Delinea Platform adds that extra layer of protection. If/when credentials are stolen, and traditional MFA is exploited, there is another stopgap in place to ensure organizations remain secure, productive, and resilient with granular controls. Secret Server works the way you work, keeping you seamlessly secure.
Watch our webinar to learn how Secret Server stops stolen credentials with MFA on Secrets:
Secret Server Stops Stolen Credentials in their Tracks


