Endpoints, the devices people use to access company resources, are a weak spot in corporate security. Compromised endpoints are primary access points that cybercriminals use to infiltrate a network.
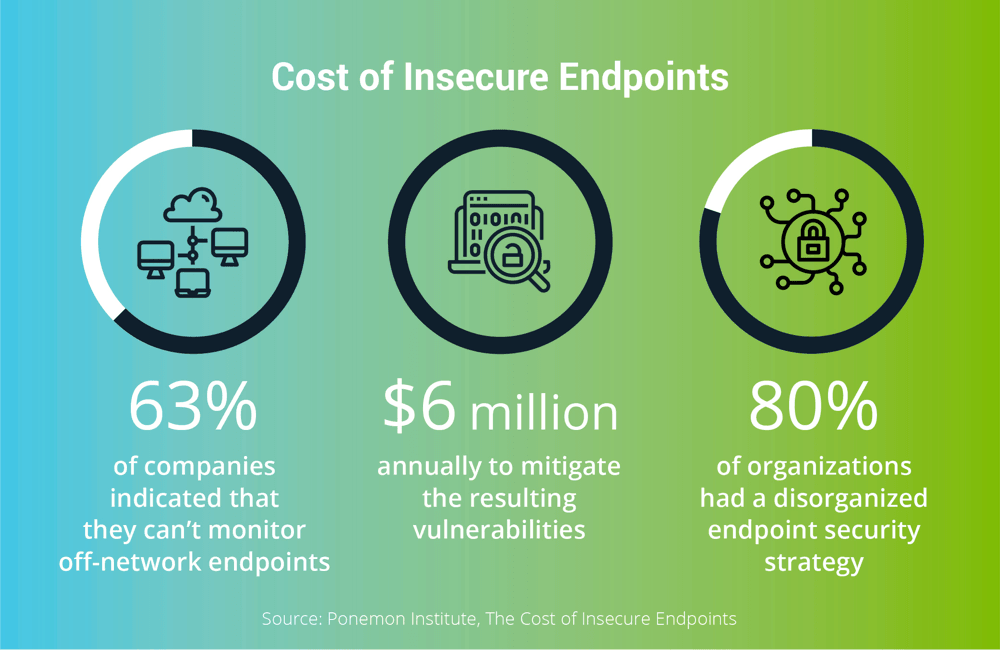
Two-thirds of companies are compromised by exploits that originate with an endpoint. The volume of endpoint attacks is rising, as is the sophistication of attacks. There’s a marked spike in criminals using advanced persistent threat (APT) techniques, in which an attacker uses one compromised endpoint to move laterally throughout a network by taking advantage of known vulnerabilities, elevating privileges, and persistently hacking once they’ve managed to get inside.
There are many reasons cyber criminals love endpoints
Most endpoint users aren’t technically inclined, nor do they feel the urgency or personal responsibility to prioritize endpoint security. The sheer variety of endpoints, including desktop computers, laptops, and mobile devices, all with different operating systems, versions, and browsers, adds complexity to security management and oversight.
Endpoints are typically compromised by either malware or non-malware attacks.
- Malware includes viruses and other rogue programs installed on an endpoint, which may cripple the endpoint or grant an unauthorized user access to it.
- Non-malware attacks exploit vulnerabilities in programs or applications that may already be installed on an endpoint, such as a word processing program or web browser.
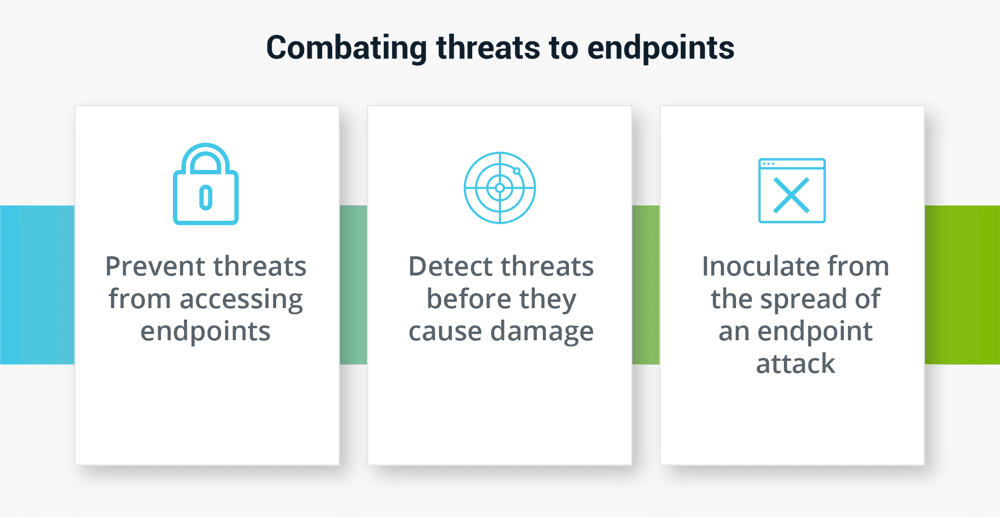
The goal of an endpoint attack is often the same: wreak havoc by taking control or crippling a device, and then progressing from an individual endpoint to other network resources.
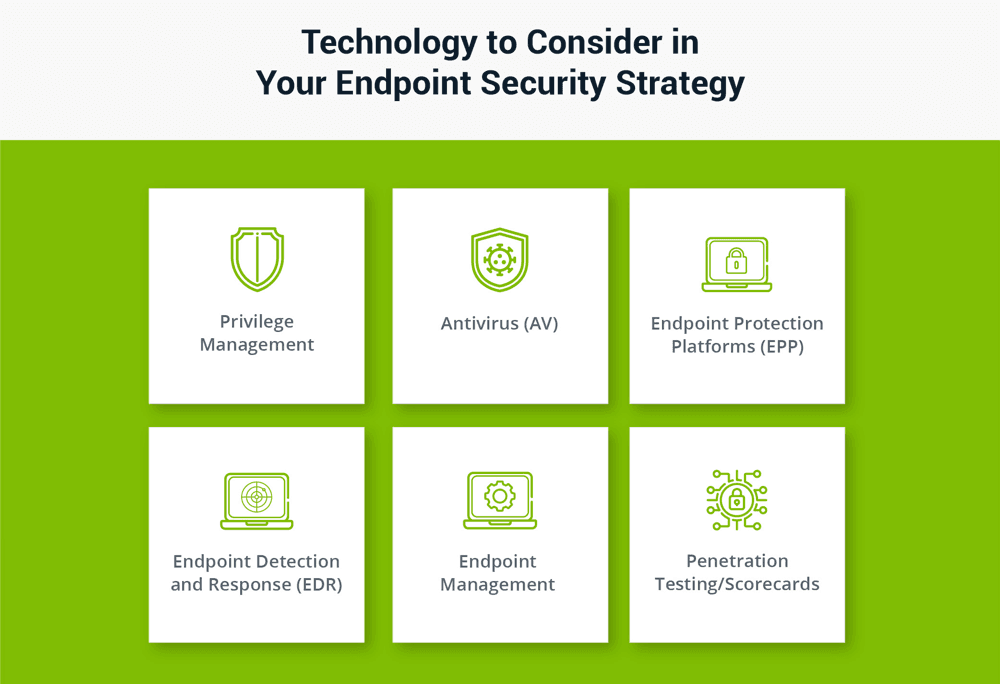
Yet “traditional” enterprise endpoint security, consisting of anti-virus installed locally on an endpoint, locking down or restricting access to potential soft spots, and applying user roles and privileges on a piece-meal, as-needed basis, has proven to be wholly inadequate. An approach like that is difficult to maintain, monitor and scale. It may also be rife with easy-to-exploit holes. That is why a comprehensive approach to endpoint security matters.
Imagine a world where you’re confident employees can access corporate resources without fear, uncertainty, or doubt that they may compromise sensitive systems. Imagine your IT staff has ensured all endpoints attempting to access business resources are secure. Imagine your users don’t feel they need to circumvent security protocols on their endpoints to do their jobs.
It’s possible. You have just imagined the best endpoint security for the enterprise.
Read on to learn about best practices for protecting endpoints and limiting the damage a compromised endpoint can cause. In this blog, I’ll outline how your organization can manage endpoint security effectively and mitigate the risk of compromised endpoints.