Cloud Server Privilege Management for Dummies eBook
The first half of the year saw an increase of 75% in ransomware attacks that target Linux-based servers compared to the first half of last year.
~ TrendMicro report
Cloud server breaches are on the rise. Servers housing critical data are falling prey to increasingly sophisticated cyberattacks. Enterprises are continuously challenged with server access vulnerabilities, ransomware, supply-chain attacks, and securing remote access in the hybrid cloud security landscape. Adding to these challenges, most organizations are understaffed in security. They lack the process and technology to protect their servers in the cloud, making them even more vulnerable to security incidents.
45% of businesses have experienced a cloud-based data breach or failed audit in the past 12 months.
~ 2022 Thales Cloud Security Report
80% of companies reported they lack a dedicated security team responsible for protecting cloud resources from threats.
~ State of Cloud Security Maturity 2022
Critical to server security is securing accounts and their associated entitlements for logging into machines, as well as running privileged commands and applications. Your systems and data will be at great risk should these privileged accounts fall into the wrong hands. It only takes one compromised privileged credential to inflict extensive damage—from reputation, cost, intellectual property, personally identifiable information, protected health information, and even market/shareholder value.
With the growing frequency and sophistication of ransomware attacks, businesses can no longer afford to be passive with their cybersecurity. In the complex and heterogeneous server environment, you must implement proactive security solutions to discover, track and manage privileged access across all servers.
Shifting from reactive to proactive security
Visibility is the cornerstone of proactive security. You cannot protect what you cannot see. Native (traditional) tools do not provide the required visibility and granular controls into permissions to facilitate proactive risk mitigation. Modern Privileged Access Management (PAM) is a proactive solution whose architecture aligns with NIST’s zero trust Architecture and provides essential visibility into privileged sessions and permissions. These permissions dictate who has access to the servers and grant users access only for the time needed to get the job done.
If an attacker makes it past an organization’s cyber defenses, the typical attack chain includes account takeover, workstation compromise, privilege escalation, and vertical movement to the server network. On the server, which houses your critical data, privilege elevation and lateral movement are other common tactics leading to data exfiltration or encryption for ransom.
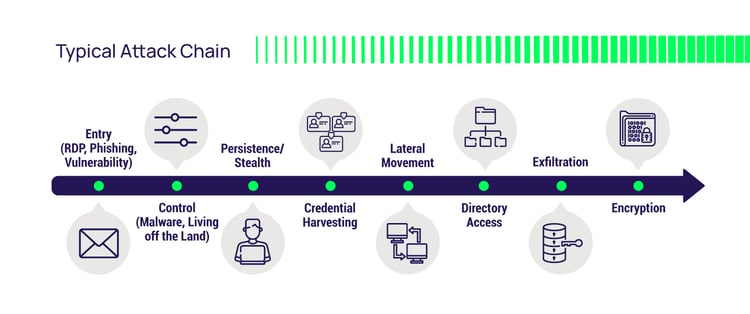
Attackers need elevated privileges to move about the server network, scan for critical info, disable security services, reconfigure backup software, encrypt and exfiltrate data. Stopping the attack chain and the attacker’s lateral movement requires a concerted effort between several initiatives, including:
- taking away implicit trust
- enforcing least privilege
- consolidating identities
- implementing MFA at depth
Cloud and on-premise server access must be secured with proactive access controls at every touchpoint to reduce risk and ensure compliance. In the overall cybersecurity modernization roadmap, your Privileged Access Management (PAM) solution must keep pace or greatly increase your risk of cyberattack.
What proactive hybrid cloud security looks like
Modern PAM is a proactive solution that organizations implement to reduce the risks associated with privileged credentials and help address their regulatory and cyber insurance requirements.
For best practices and deeper insights into cloud server privilege management security, download our latest eBook—Cloud Server Privilege Management for Dummies. As you build your structured security program to protect your cloud and on-premise servers, this eBook will help inform your decision.
"Privileged access" includes not only who can access what but also what they can do with that access and when they can do it. In this book, you’ll learn how stronger and more granular authorization controls protect servers from cyber attackers and rogue insiders. Use our PAM maturity model as a prescriptive approach to maturing your organization’s PAM capabilities, helping you reduce risk across hybrid clouds and distributed IT architecture, as well as securing remote, 3rd party, and other identities.
The Cloud Server Privilege Management for Dummies eBook explores the attack chain to better understand the modern cyber criminal mind, tactics, techniques, and procedures they use daily to circumvent your server defenses. You’ll learn what lies beyond a password vault and how more advanced PAM capabilities can improve your organization’s resilience to breaches while aligning with zero trust best practices.
You'll be better positioned to prevent, detect, and respond to attacks resulting from typical server attack vectors
Armed with this eBook’s knowledge, you and other IT managers, systems administrators, cloud architects, and security professionals will better understand the cyber attacker’s mind and methods. You’ll be better positioned to prevent, detect, and respond to ransomware attacks, data breaches, and supply-chain attacks.
The eBook explains new and better ways to fortify your IT server infrastructure and layer obstacles in the attacker’s path—forcing attackers to give up after circumventing these obstacles and making them implement riskier tactics to bypass your cyber defenses. Additionally, this eBook dives into the importance of server PAM and the risks involved if your business does not take the next step in PAM maturity.
Leveraging the PAM Maturity Model into your security modernization roadmap
Delinea developed the PAM maturity model based on conversations and engagements with over ten thousand customers. The PAM maturity model’s goal is to ensure your organization’s successful PAM adoption by helping you understand the steps you must take.
This model enables your organization to take an identity-centric approach to security by extending privilege management across all identities within the organization. The further your organization is along the PAM maturity model, the more dynamic, automated, and integrated your approach to PAM becomes.
For more details—whether you are only just starting on a PAM journey, looking to replace an incumbent PAM solution for a cloud transformation project, or want to know how to manage and secure diverse, distributed server environments—please check out our Cloud Server Privilege Management for Dummies eBook.