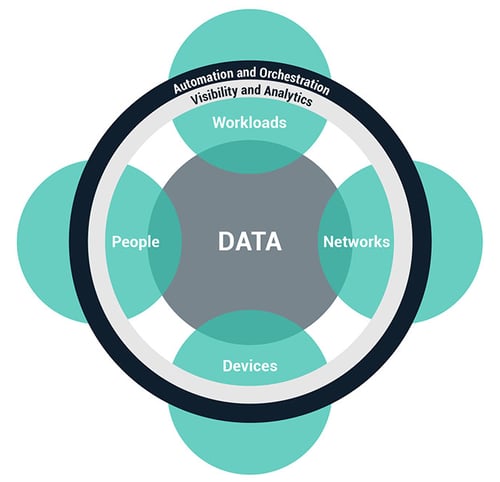
You Can’t Buy Zero Trust
Zero trust is not a product. It’s a model, concept, or framework. It’s incumbent on vendors such as Delinea to incorporate its principles and guidance into their products.
PoLP As the Glue Between Zero Trust and PAM
Zero trust and PAM align on the concept that humans are the weakest link. We make silly mistakes, fall for social engineering attacks, can be bribed and blackmailed, and generally don’t have strong password hygiene. Therefore, it makes no sense to trust human administrators with routine use of “keys to the kingdom” credentials. By doing so, we’re increasing our risk of a critical outage, a data breach, or a ransomware attack.
We can resolve this through the principle of least privilege (PoLP), a core concept in zero-trust security and PAM. PoLP advocates eliminating implicit trust in users, having them routinely go about their day using an individual (not shared) account with minimum rights. If they legitimately need more, we must verify the user and the request, granting only what’s necessary for a limited time. Thus, if the user identity is compromised, the blast radius is contained and lateral movement within the network prevented.
Trust but verify is now never trust, always verify
This is a way of saying, “let’s not implicitly trust our admins to do the right thing with privileged accounts,” because history tells us that’s not a great idea. It is a one-eighty from the days when admins had carte blanch access to superuser accounts such as root, local administrator, oracle, cisco, sa, admin, and other built-in administrator accounts. The old security tenet of “trust but verify” goes out of the window, replaced with “never trust, always verify.”
Things to Look for in a PAM Solution
You must critically assess the competence of your PAM solution to support zero-trust across two fronts. One is its ability to support least privilege. The other is whether the PAM vendor designed it to support cloud-based hybrid IT infrastructure.
There are two critical moving parts of PAM. Gartner defines these as Privileged Account and Session Management (PASM) and Privilege Elevation and Delegation Management (PEDM). Simplifying, PASM allows you to put shared privileged accounts in a secure vault for emergencies only, taking them out of play. PEDM is the part that enables a user with minimum rights (i.e., least privilege) to elevate and perform privileged tasks. They work in concert, so your PAM solution needs both for zero-trust security, but a vault alone is insufficient.
Next, with IT infrastructure no longer contained by a defensible perimeter (your data center), legacy PAM solutions built for that paradigm are unsuitable and can’t adapt. What’s required is a modern SaaS platform for centralized PAM policy management plus distributed clients to enforce the policies in your distributed VPCs, VNets, and multiple clouds.
With this, the result is a PAM solution that supports modern cloud-based use cases aligned with zero trust principles that protect your critical IT infrastructure and data from identity-related attacks.
For more details – whether you are only just starting on a PAM journey, looking to replace an incumbent PAM solution for a cloud transformation project, or simply trying to figure out how zero trust fits into PAM – please check out our Zero Trust Privilege for Dummies eBook.