Risk-based authentication: A pillar of a zero trust strategy
I’m betting your organization looks very different from what it did even a year ago.
Like most companies, you’ve got new business initiatives, tools, workflows, and people—a third of the workforce changes jobs every year! You’ve also got new security worries as cyber criminals hone their strategies to steal credentials and leverage AI to impersonate legitimate users.
When your risk profile is constantly changing, security controls can’t be static. You can’t wait for an infrequent manual review to change a security policy that’s no longer sufficient to protect you.
Adopting a risk-based approach to cybersecurity helps you navigate an unpredictable future in which change comes quickly. Risk-based authentication (RBA) is a prime example of this flexible, dynamic approach to managing identity risk.
In this blog, we'll cover:
- How risk-based authentication reduces your risk of identity-based attacks
- How to implement risk-based authentication without causing friction for your users
- Examples of risk-based authentication in action
What is risk-based authentication (RBA)?
Risk-based authentication is the process of verifying user identities using tactics that match the level of risk. It entails detecting potential identity-related risks, intelligently matching those risks to authentication requirements, and responding appropriately to minimize the risk of identity-based attacks.
Risk-based authentication is intelligent and adaptive. It automatically creates a behavior profile for each identity over time and compares activity with that baseline to determine a risk score. As the risk score increases, authentication requirements become more stringent, essentially raising the fence higher and higher. Users must meet those authentication requirements before accessing resources or conducting other privileged activities.
Think of risk-based authentication as a “continuous polygraph test for access.”
Benefits of risk-based authentication
By combining risk-based authentication with least privilege access policies, you can more effectively safeguard sensitive data and reduce the risk associated with compromised privileged credentials.
In addition, risk-based authentication's flexibility allows you to provide a better user experience. In most situations, authentication can be simple and seamless, so users don’t get frustrated or annoyed with multiple verification requests. Users will only be asked to perform more authentication steps when high-risk scores warrant additional requirements.
Examples of risk-based authentication in action
When and where should you apply risk-based authentication?
You can and should apply risk-based authentication at every access control point in the attack chain. This includes initial login to systems, privileged command or application execution, and privilege elevation.
Privileged identities may access every type of IT resource in your environment—your password vault, workstations, databases, servers, applications, etc.—both on premise and in the cloud. Therefore, your risk scores should account for behavior within each of those systems as well as when users move from one system to another. That way, if an attacker gains privileged credentials and escapes initial detection, you can interrupt lateral movement before they continue to do damage.
Not all privileged users or privileged behaviors are created equal. Risk-based authentication considers the context of an access request, based on numerous factors.
For example:
- The type of data the user is attempting to access. Is it confidential business information or sensitive PII subject to privacy rules?
- User status. Is the user an internal employee or an external vendor or contractor?
- Potential business impact: What would happen if the system or data being accessed were altered or damaged?
- The nature of behavior. Is the behavior unusual for this identity, or for identities with similar profiles? For example, are they on a new device, or logging in at an unexpected time of day, after a long time, or from an expected place?
If any of these answers are “yes,” risk-based authentication would override standard authentication rules, policies, or entitlements and prompt the user to meet additional requirements to verify their identity.
For example, a user logging in from the corporate network on a managed device might be granted access with a single factor, a password. However, a user logging in from an unknown network on an unmanaged device might be asked for a second or even a third factor.
In addition to the above examples, risk-based authentication solutions are developing abilities to learn from past behavior and recognize risky patterns that humans can’t anticipate.
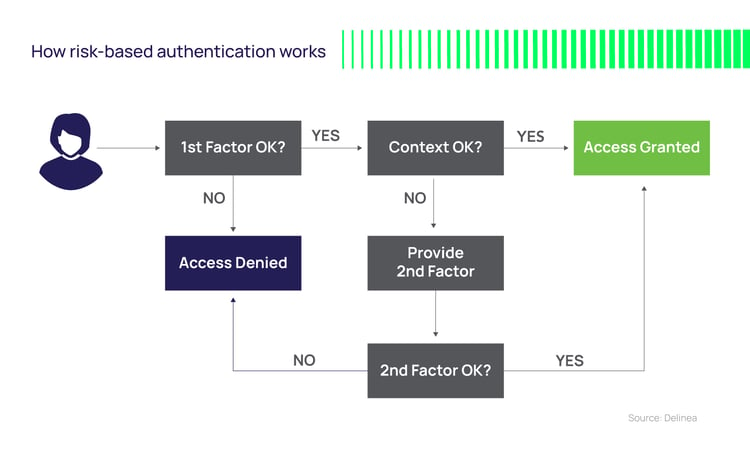
Types of risk-based authentication
There are a wide range of methods you can include in your risk-based authentication strategy, including:
- Hardware Tokens: These are small hardware devices that a user carries to authorize access. They come in different forms, including smart cards, key fobs, and USB devices. The hardware device generates a one-time password (OTP) that the user enters when prompted.
- Single-Factor Cryptographic Devices: FIDO U2F and its passwordless successor, FIDO2, are authentication standards driven by the FIDO Alliance. They are designed to be open, secure, private, and easy to use.
Hailed as the next-generation Two-Factor Authentication, FIDO U2F, and FIDO2 include heightened security, as public key cryptography protects against phishing, session hijacking, and malware attacks, as well as ease of use and high privacy. - Soft Tokens: These are software-based tokens or applications that generate a one-time password (OTP). They are typically mobile apps installed on a smartphone and can use push notifications for improved user convenience. The widespread adoption of mobile devices has made soft tokens a popular option.
Soft tokens have two main advantages over hardware tokens. First, users are less likely to lose or forget their phones than a single-purpose hardware token. Second, soft tokens are easier and less expensive to distribute to users. - SMS/Text message: An OTP can be sent to a phone via SMS. Once received, the user enters it into the login screen.
- Phone call: A user receives a phone call to a registered phone number (landline or mobile number). The user then provides the correct response to the voice prompt to complete authentication.
- Email: A user receives an email with a link to verify the authentication request. Clicking on the link completes the authentication process.
- Security questions: Instead of tokens, users provide answers to security questions. These questions can be pre-defined, or the user can define their own questions.
- Biometric: These methods include fingerprints, retina scans, facial recognition, and more. Many of the latest smartphones support biometrics such as Touch ID on iPhones and Fingerprint for Samsung Galaxy devices. The latest FIDO2 standard includes the ability to use on-device biometrics such as Microsoft Hello or Apple FaceID.
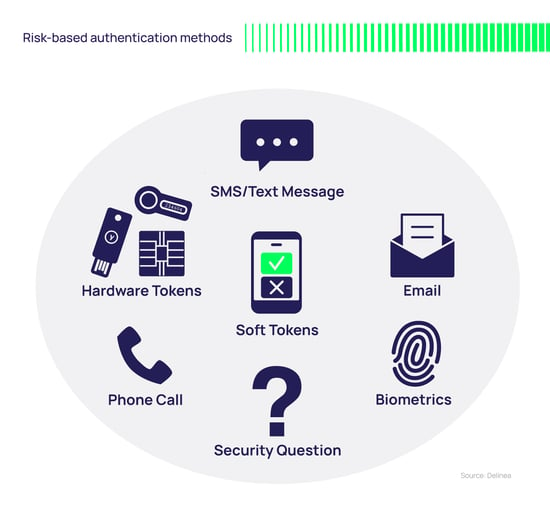
Some authentication methods require two-way interaction with human users (they must respond to a question or click a button).
Others can happen behind the scenes to verify machine identities. Incorporating a wide range of authentication methods gives you flexibility and choice, which is especially important as workplaces evolve toward a passwordless future.
Risk-based authentication and zero trust
Zero trust is a cybersecurity strategy that operates on the principle of "never trust, always verify." This strategy ensures that no one is trusted by default, inside or outside the network, and verification is required from everyone trying to access network resources.
This approach is crucial for risk authentication as it minimizes the attack surface, improves compliance visibility, and reduces the risk of data breaches by requiring strict user and device verification, context-aware access controls, and least privilege access enforcement.
What makes a good risk-based authentication solution?
A strong risk-based authentication (RBA) solution balances security with usability, ensuring only legitimate users gain access while keeping friction minimal. The best solutions use contextual data, artificial intelligence, and adaptive policies to assess risk in real time.
The most effective RBA solutions continuously evaluate authentication attempts, analyzing factors such as device type, location, user behavior, and network anomalies. They go beyond static rule sets, applying AI-driven risk scoring to detect suspicious activity without disrupting the user experience. Seamless integration with Identity and Access Management (IAM) solutions is also key, enabling organizations to enforce authentication policies consistently across applications.
User experience is just as important as security. A well-designed RBA solution minimizes unnecessary authentication steps for low-risk scenarios while triggering step-up authentication only when needed. It should also support compliance with security frameworks such as GDPR, PSD2, and Zero Trust models. Continuous monitoring and analytics help refine authentication policies over time, improving both security and usability.
With these elements in place, organizations can implement RBA that strengthens protection without creating unnecessary roadblocks for users.
MFA at Depth
One way companies are implementing risk-based authentication is by requiring Multi-factor authentication (MFA) at every access gate, to verify users’ identity regardless of which system they are accessing.
With the Delinea Platform, you can implement consistent MFA challenges and requirements for identity assurance at multiple levels: when users access the vault or request a shared credential, at asset login, and at privilege elevation. IT and security teams maintain full visibility across all MFA enforcement requirements, challenges and activity leveraged across all solutions in the Delinea Platform in a single view.
Frequently Asked Questions
How does one implement risk-based authentication?
Implementing risk-based authentication starts with defining the key risk factors that determine whether a login attempt should be trusted or challenged. These factors typically include device attributes, geolocation, behavioral patterns, and network reputation. Organizations then integrate an RBA engine within their Identity and Access Management (IAM) framework to analyze these signals in real time and apply adaptive authentication policies accordingly.
Over time, continuous monitoring and AI-driven analysis refine these policies, improving both security and the user experience.
How is continuous authentication different from risk-based authentication?
Risk-based authentication focuses on assessing the risk of a login attempt at the moment of authentication, determining whether additional verification is needed before granting access. Continuous authentication, on the other hand, monitors user behavior throughout an entire session, analyzing keystroke dynamics, mouse movements, and other behavioral signals.
If suspicious activity is detected mid-session, continuous authentication solutions can prompt the user for re-authentication or terminate access altogether. While RBA determines access at the start of a session, continuous authentication ensures security remains dynamic throughout.
How is dynamic authentication different from static authentication?
Static authentication relies on fixed credentials, such as passwords or PINs, that do not change based on context. Dynamic authentication adapts security measures based on real-time risk signals, such as unusual login locations, device changes, or deviations from typical user behavior.
Risk-based authentication is a form of dynamic authentication because it adjusts security requirements based on contextual risk assessment rather than relying on a one-size-fits-all approach.
What is the difference between risk-based authentication and step-up authentication?
Risk-based authentication assesses the likelihood of fraud before determining the appropriate level of security enforcement. Step-up authentication is one of the mechanisms triggered by RBA when a login attempt is deemed high-risk. For example, if an RBA system detects a login from an unfamiliar location, it may prompt for multi-factor authentication (MFA) as a step-up measure.
In short, RBA is the decision-making framework, while step-up authentication is the action taken in response to elevated risk.


