Ethical hacker tips for securing the cloud
Is the cloud safer than traditional on-premise computing environments? Can the cloud be hacked? Is it safer to use the cloud as storage for all things digital? These questions are asked all the time by people inside IT and out.
The truth is simple—the cloud is never 100% secure. Protecting the cloud from cyber attacks is centered around available security controls. Security control availability and how these controls are enabled and used are key to making it as difficult as possible for unauthorized users and attackers from gaining access to your infrastructure, whether in the cloud or on-premise. Business resilience needs to be a top priority for every organization across the globe.
I’m going to take you through what the cloud is, the cybersecurity risks affecting the cloud, and how to reduce those risks with the right security strategy and controls. I’ve included at end of this blog a list of AWS and Microsoft Azure resources for you to use as cheat sheets and for further reading.
Index to each section
1. What is the cloud, really?
2. Cloud is a top target
3. Cloud Models
4. Type of cloud services
5. What is the value of cloud?
6. Compliance, regulation and cyber insurance
7. Top tips to protect and secure cloud environments
8. Useful cloud resources
What is the cloud, really?
Popular culture treats the cloud as some mysterious, amorphous place where data is stored and shared. The truth is companies have historically trusted the cloud in varying degrees. While the early adopters launched headfirst into the cloud as soon as they could, other companies have been more cautious, observing the cloud from a distance and deliberating their foray into the cloud. Today, many organizations are in a mixed cloud environment, meaning digital resources are on-premise and other resources are spread across multiple clouds.
It is important to be clear about what cloud is and what it is not. To illustrate, this is NOT cloud computing!

So, what is the cloud?
The cloud is simply someone else’s servers in a certain location that allows you to use those resources when required
Think of it like electricity: you don’t need to own a power station to receive electricity, you just need to be connected to the grid or network. When you flip a light switch, the lights will come on and you get charged for consumption. The cloud functions similarly, consisting of on-demand connected computer resources on shared networks. The data does not reside in the cumulus clouds across the sky.
From this point onwards when I refer to “the cloud”, I will be referring to actual servers and services running in a data center. Some of the largest public clouds are Amazon AWS, Microsoft Azure, Google Cloud Platform, IBM Cloud, and Alibaba.
This is where your data would be—Real World Cloud Computing
Due to the Covid-19 pandemic, cloud adoption has quickly accelerated in the past few years as organizations were forced to adapt their workforce for remote work. To migrate to the cloud as quickly as possible, organizations prioritized speed, leading to misconfigured cloud environments resulting in weak cybersecurity. Misconfigured cloud environments provide inadequate defenses and leave cloud environments open to cyber attackers.
Cloud is a top target for cybercriminals
According to the 2021 Verizon DBIR (Data Breach Investigations Report), cybercriminals targeted assets on the cloud more than assets located on-premise. According to the report, many of the data breaches and security incidents were the result of poorly or misconfigured cloud environments. To learn more about the Verizon Data Breach Investigations Report, check out 3 Top Takeaways from the 2021 Verizon Data Breach Investigations Report for the report’s key highlights.
Cyber attackers are looking to take advantage of organizations hastily moving to cloud environments. Organizations rushing their cloud migrations may not have the time or skilled resources to put the right security controls in place. As a band-aid, organizations may try to implement inadequate legacy security controls and force them to work in cloud environments. Security controls that are not optimized for the cloud cannot provide the appropriate defenses that organizations with cloud environments require.
What are the different types of cloud computing?
The different categories of cloud refer to whether you have a dedicated environment if it has shared resources, and whether it spreads across different locations or in multiple cloud infrastructures and services. Previously, cloud computing types were based on ownership and location. Today cloud classification is far more complex.
Here are the 4 common cloud types:
- Private cloud – your own infrastructure running in a rented data center
- Public cloud – someone else’s infrastructure which you are sharing with other tenants
- Hybrid cloud – a combination of private and public clouds
- Multi-cloud – a combination of various cloud services from different vendors
Clouds can be controlled using Managed Service Providers (MSPs), which provide skilled personnel to help manage, deploy, configure, maintain, and secure infrastructure. Due to the global shortage of skilled workers in the security field, MSPs are a needed and common means for many organizations to obtain skilled resources.
What kind of services can you get with cloud computing?
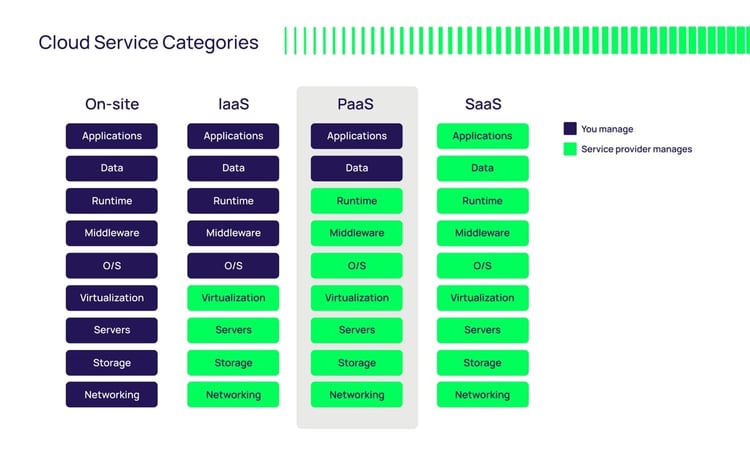
Today there are many different types of cloud services available, from all-included infrastructure to simple services such as storage or software.
Cloud services can be broken down into the following primary categories - other service types exist and more will be introduced in the future:
- IaaS—Infrastructure as a Service – the entire infrastructure stack is provided from servers, network, virtualization, and storage. You manage the software and data along with the operating systems and middleware.
- PaaS—Platform as a Service – in addition to servers, networks, virtualization, and storage, you also get the operating systems and middleware. You manage just the data and software.
- SaaS—Software as a Service – the vendor takes care of everything in all aspects, including maintenance, updates, and availability. All you do is use the software.
Why do organizations adopt the cloud?
Cloud services have many benefits for organizations, and organizations are increasingly moving and adapting to the cloud as cloud value and security benefits can be significant.
Here are several cloud computing benefits:
- Easily Scalable OnDemand
- Virtualization
- Out of the Box Backup and Recovery Strategy
- High Availability
- Flexible Cost Models
- Fast Deployments
- Distributed Environments
- Reduced Environment Footprint
- Automated Software and Security Updates
- Disaster Recovery
- Access Remotely from any location
- Out-of-the-box security
- Immediate Service and Business Value
- Managed Services
What about compliance, regulation, and cyber insurance?
Before moving to the cloud, you need to know what data is regulated and what boundaries restrict where the data can be located. This determines the cloud type and geographic locations that can be used. Cloud type and data location may have a tangible impact on your cyber insurance policies.
It is important to perform a complete Data Impact Assessment and ensure that access to sensitive data has full access audits. After conducting an impact assessment, I recommend performing a Data Classification, which identifies sensitive data and the different types of data found.
I have used a similar process to Data Center Classification that determines the data in relation to its importance and the data’s alignment with the Confidentiality, Integrity, Availability (CIA) Triad. Once you classify the data into confidentiality, integrity, or availability, you must then align the data to security and access controls based on the risk to ensure adequate security is applied.
The Data Impact Assessment and Data Classification will help an organization determine what type of data might be impacted by compliance and regulation, as well as whether that data is permitted to be stored outside of the country’s borders. These steps should not be overlooked by organizations migrating to cloud environments.
In the Cloud, it is important to know what you are responsible for and understand your service agreements
What are my top tips to protect and secure the cloud?
Ok, so now you understand the basics of the cloud. Organizations cannot move their on-premise traditional security tools and force them to work in the cloud, as this creates security gaps and misconfigurations. It’s important to understand what security solutions and tools are available for cloud environments and know which of those security solutions are tied to a specific cloud type. Some security solutions do not work across multi-cloud or hybrid cloud environments, so it is critical to select the appropriate cloud security solutions for your organization’s needs.
Many organizations occasionally find themselves in a situation where they are using different security solutions for the same purpose of managing each cloud environment. This results in multiple dashboards, different configurations, and inconsistent security controls, which makes it easier for attackers to find gaps in cloud security configurations.
As part of your cloud security strategy, you need to consider a plan on how you are going to protect and secure the infrastructure that supports your business. Many infrastructure components can be broken down into a few items and each component needs a cybersecurity strategy that effectively reduces cyber attack risks:
- Data – the vital data that critical business decisions and value depend on
- Encrypt your data
- Back-up your data
- Manage access to your data
- Apps & Code – the software that enables and powers the data
- Infrastructure – the infrastructure that supports the data and apps
- Networks – the communications highway and access to the data and apps
Most organizations break down cloud security into the following elements:
- Identity – users, machines, services, applications, or code
- Access – security controls in place to verify authentication
- Authorization – security controls in place to control privileged actions
- Devices – devices, policies, and configurations permitted to access the cloud
- Location – does the business restrict access based on IP or location?
- Audit – ensures compliance and non-repudiation
What are priority security strategies for cloud protection?
 Protect your Keys and Secrets
Protect your Keys and Secrets
– Manage Privileged User Access
In the cloud, privileged accounts are the keys to the kingdom. Once an attacker has access to your privileged keys and secrets they can move around freely, deploy ransomware, lock you out of your own environment, or other serious damage. Make sure to protect your keys and secrets with a Privileged Access Management solution across multiple or hybrid clouds and SaaS environments.
PAM solutions ensure only those with authorization can obtain privileged access to your cloud by having consistent security controls in place, transparent auditability, and automation. Implementing the Principle of Least Privilege will enable a zero trust security model, helping you enhance your organization’s cybersecurity on the cloud.
To learn more about the Principle of Least Privilege, check out Delinea’s Free eBook—Least Privilege Cybersecurity—that will lead you on the path the Least Privilege Security.

Start your least privilege journey here
Help reduce cyber fatigue by moving passwords into the background with a combination of single sign-on (SSO) and privileged access management (PAM). The use of SSO and PAM enables seamless access to your cloud environments for business managers and developers. Using a PAM solution will reduce the number of human-created passwords and ensures that each cloud environment or application has a strong and unique system-generated password that is significantly more difficult to crack.

Multifactor Authentication Everywhere
You can’t rely on passwords being the only security control. Context-based security is the next security level: when the threat landscape increases, multifactor authentication is forcibly implemented to ensure that user or machine identity is authentic and trusted.

Audit and Visibility
Ensure that all access and changes are audited and centralized so that you have full visibility into what is happening in your cloud environment. Typically, not only will this make it difficult for attackers to be stealthy and hide, but it will also ensure that employees do not take risky shortcuts.

Test your Security
Have a Zero Assumptions security approach that always assumes a breach. This includes making sure to test and assess your security controls periodically. Utilize expert pen testing and red teams to test your security controls to the limit. This extreme security testing ensures that during a real attack your controls will alert you promptly, giving you the time to protect your business and keep attackers out of your cloud environments.

Security Automation
The most valuable resource in the world is time, and automation helps businesses reduce wasted time. By eliminating repetitive and redundant tasks through automation, businesses can bolster cloud security and reduce the possibility of misconfigurations. These misconfigurations are one of the top causes of cloud data breaches and security incidents.

Data Encryption
Make sure your data is protected by encrypting the data. This means not only securing and controlling access but also using encryption to mask data so it cannot be viewed or read by people or systems without the appropriate privileges.

Backup and Recovery Strategy
A backup and recovery plan is only as good as the backup strategy underpinning the plan. While most organizations focus only on redundancy, it is important to also have a backup plan that incorporates resiliency against ransomware. A ransomware backup strategy consists of a strong segmentation of production network backups along with comprehensive access controls. These backups should implement different privileged accounts that are used to regulate backup access. Consider protecting your backup privileged accounts in a Privileged Access Management solution that includes strong security controls and auditing.

Business Resilience Plan
This is the big “what if” question, the disaster scenario. What if the cloud provider goes down? What if the cloud provider is the victim of a security incident or goes out of business? Always have a business resilience and contingency plan that can be triggered in the event of a disaster. Having redundancy for important business services in place allows business operations to operate nominally.

Invest in your Employees
Organizations must invest in their people to maintain a robust cloud security strategy.
Your cloud security strategy will only be as good as the people who manage, configure, deploy, and use your cloud. A strong cloud security strategy is a combination of technology, process, and people. Choosing a managed service provider may reduce the overall resources required to run the cloud, but it is also important that your business has strong experts to know that the right security controls are in place and that operational security practices are being met.
To help you on the path to cloud security check out my Privileged Access Cloud Security free eBook.

FREE EBOOK
Increased cloud adoption poses greater security risks to your IT and business users
Some best security practices & resources to help protect your AWS and Azure cloud
To help you get started with securing your cloud environments, I have provided some resources I use frequently. These resources are very helpful as I can never remember all the configurations and commands. Keep these resources easily accessible for when you need a quick reference, such as checking a command line flag.
These resources for AWS and Azure include security best practices, terminology, guides, and a Command Line Interface cheat sheet.
Resources For AWS
Amazon Web Services best practice rules
Best Practices for Security, Identity, & Compliance
AWS Glossary
Your Guide to AWS Terminology
AWS CLI Cheat Sheet
Resources For Azure
Azure security best practices and patterns
Defense and Detection for Attacks Within Azure
PowerZure
Microsoft Azure Glossary
Azure CLI 2.0 Cheatsheet