Service Account Management 101: Back to Basics
Service accounts don’t have to be a nightmare. You can get them under control now.
In this blog post, you’ll learn the basics of service accounts, including the different kinds of service accounts operating in IT environments, their importance, and the challenges they pose for cybersecurity. You’ll understand examples of risky service account practices and learn best practices for setting up, managing, and securing service accounts so you can save time and lower your risk.
What is a service account?
A service account is a special type of privileged account used by an application or IT service instead of a person. Service accounts provide an identity for IT services running in on-premise and cloud environments, such as web servers, databases, and email communications.
A kind of machine account, service accounts are non-human accounts not tied to a specific person. They are used for machine-to-machine interactions and integrations in order to run critical applications, services, scripts, and automated tasks that interact with sensitive data and business processes.
Service accounts are usually created manually during software installation. On Unix and Linux systems, service accounts are often known as init or inetd.
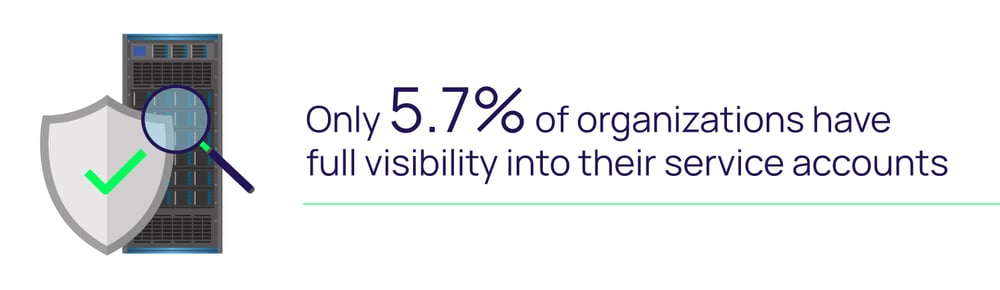
What types of service accounts are most common?
Most organizations have more service accounts than employees, sometimes up to five times as many! Businesses use many types of service accounts throughout the IT ecosystem, including:
- Local service accounts - Accounts built into Windows computers, including LocalService, LocalSystem, and NetworkService
- Domain service accounts - Domain user accounts used to run services across a network
- Cloud service accounts - Accounts for cloud hosting, development, and infrastructure such as AWS, Azure, and GCP
Why are service accounts so important?
Service accounts are important for running critical business applications and services that need to operate continuously or perform tasks automatically.
Key uses include:
- Running websites, databases, APIs, batch jobs, and scripts
- Providing an identity for a service to access resources like databases
- Facilitating integration between applications
- Operating as a proxy to perform actions on behalf of users
- Providing identity and authentication for AI agents to access resources like data, models, and infrastructure
The challenges of service accounts
Service account management is a task that’s often overlooked. Ideally, service accounts should be uniquely created and used only to run one specific service. However, creating and documenting service accounts is time-consuming. To save time, some organizations repurpose regular user accounts as service accounts.
Because service accounts are often managed manually from cradle to grave, they are prone to errors. Monitoring service account activity and detecting misuse when handled manually is challenging.
Outsmart Cybercriminals
Challenges of service account password management
Like any type of privileged account, access to service accounts should be managed by complex passwords that are stored securely and regularly rotated to avoid credential theft and misuse.
That said, creating and regularly rotating passwords for hundreds or thousands of service accounts can quickly get complicated. Changing a service account’s password introduces the risk of breaking dependent applications or services, thus disrupting business-critical operations and revenue-generating activities.
 Administrators can’t safely change a service account password if they don’t know where it’s used. Figuring out the origins and credentials of a service account can quickly become an unpleasant can of worms. Frequently, in software installations, the password for service accounts either remains the default vendor password (easily found on the internet) or resides in the memory of the consultant who installed the software and is now long gone. Service account owners often change. As a result, there is no owner accountable for ongoing management of that service account password.
Administrators can’t safely change a service account password if they don’t know where it’s used. Figuring out the origins and credentials of a service account can quickly become an unpleasant can of worms. Frequently, in software installations, the password for service accounts either remains the default vendor password (easily found on the internet) or resides in the memory of the consultant who installed the software and is now long gone. Service account owners often change. As a result, there is no owner accountable for ongoing management of that service account password.
I have seen many incidents where the IT Operations team is running around trying to figure out the service account password during a failed upgrade, patch deployment, maintenance mishap, or even worse—during a major security incident. At this point, it’s already too late, and users and the executive team are screaming for answers.
To save time and avoid the risk of interrupting services, many organizations set their service account passwords to never expire and never update them, which is not much better than having no password at all. Failing to change service account passwords represents a significant security risk because service accounts are often over-provisioned with excessive or standing privileges to sensitive data and systems.

An example of a service account risk
A state-of-the-art power station once hired me. The station was relatively new and fully automated with remote controls. They wanted me to review its cybersecurity posture.
The physical security was impressive. The security system could tell when visitors were five minutes away, and gave advanced warning for when visitors would arrive, what they would be driving, and how many people were in the vehicle. If visitors arrived one minute before or after the prediction, they would have to deal with armed guards.
All physical doors had access controls, including the engine rooms. Inside the engine rooms, each engine had its own control valves to change pressure and water flow physically.
Operational Technology (OT) was also highly secure. Command and control via the programmable logic controllers (PLCs) and SCADA control systems all featured the latest and greatest threat protection, with millions spent to prevent cybersecurity attacks.
They'd built themselves a fortress.
Not so for service account security.
Sitting on the table next to the controls was a printed page. It contained all the IP addresses, usernames, and passwords for each control station and the associated service accounts. These had not been changed in more than four years and had all been installed by the manufacturer with default vendor credentials.
Anyone could have made copies of this list: visitors, disgruntled employees on their way out the door, or even contractors moving on to other projects. Anyone could have taken a photo with their smartphone and later launched an attack. The power station would never have seen it coming.
A privileged service account with a default vendor password can mean the difference between a cyber catastrophe versus a simple perimeter breach
Don’t be another statistic. Get in control of governing your service accounts right away. Prioritizing service account management will not only save you time and money but will also reduce your risk of a cyberattack.
How to get started with an effective service account management program
Control your service accounts through every stage of the Privileged Access Management Lifecycle.
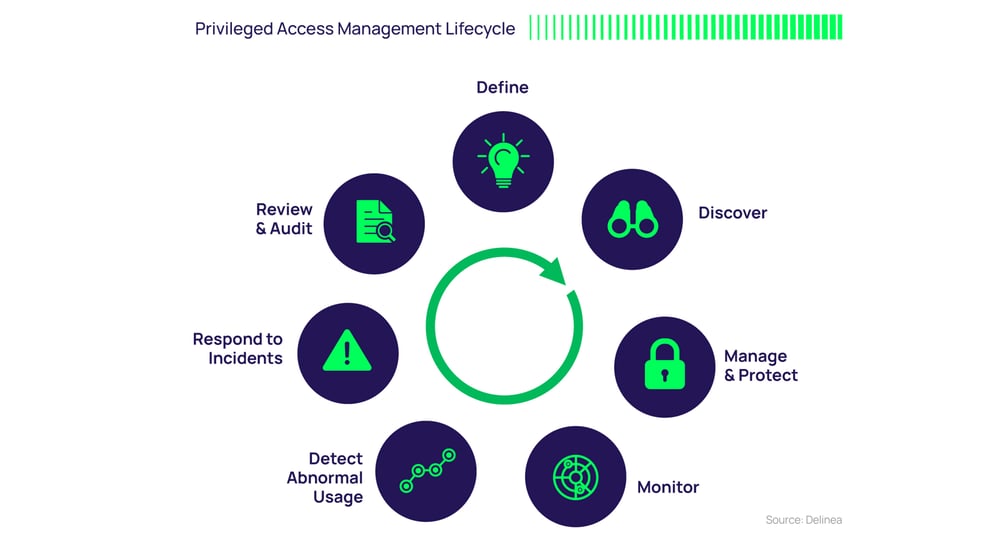
Like any IT security measure designed to help protect critical information assets, managing and protecting service accounts requires both an initial plan and an ongoing program.
Define
Define and classify service accounts. Start by identifying which service accounts should be a priority in your organization. Map out what important applications and programs rely on data, systems, and access to those service accounts. One approach is to reuse a disaster recovery plan that typically classifies important applications and specifies which need to be recovered first in case of attack. Make sure to align your service accounts to your business risk so you know which ones are most important to generating revenue and serving customers.
As part of this process, document the owner of each service account and all the dependencies associated with it. As you move forward, this should be part of the process for provisioning all new service accounts.
Discover
Discover your service accounts. Use Privileged Access Management (PAM) software to identify your service accounts and implement continuous discovery to curb service account sprawl. This helps ensure full, ongoing visibility of your service account landscape, which is crucial to combating cybersecurity threats.
Try our free Service Account Discovery Tool
Measure the state of privileged access entitlements in your Active Directory (AD) service accounts and understand areas of the highest risk.
You may find:
- Aged service accounts and passwords that are no longer needed
- Expired service account passwords that require changing
- Service accounts and passwords without expiration requirements
- Services that share privileged credentials, violating least privilege policies
Manage and protect
Protect your service account passwords. Proactively manage, monitor, and control service account access with Privileged Access Management (PAM) software. Your solution should automatically discover and store service accounts; schedule password rotation; audit, analyze, and manage activity; and monitor password accounts to detect and respond to malicious activity quickly.
Service accounts should be provisioned with limited access, rather than broad, standing access.
Monitor
Monitor service account activity. Your PAM solution should be able to monitor and record service account activity. This will help enforce proper behavior and avoid mistakes by employees and other IT users because they know their activities are being monitored.
Detect abnormal usage
Track and alert service account behavior. Ensuring visibility into the access and activity of your service accounts in real time will help you spot suspected account compromise and potential abuse. For example, you may want to know that a service account has been used to log on to a critical system with sensitive information during unexpected hours or an unusual number of times.
Respond to incidents
Prepare an incident response plan in case a service account is compromised. When a service account is breached, simply changing service account passwords or disabling the service account is likely not sufficient. Cybercriminals may already have installed malware and even created their own service accounts or other privileged accounts. You’ll need to follow their tracks to see how they traveled through your IT environment.
Review and audit
Audit and analyze service account activity. Automated reports help track the cause of security incidents and demonstrate compliance with security policies and regulations. As part of your review process, determine if service accounts are still required, confirm security controls are working as expected, and update expiration dates. It’s likely that you’ll be able to deprovision unneeded service accounts to reduce your attack surface.
Ready to get started? Watch our webinar: Service Account 101: How to Start Managing Your Service Accounts, and don't forget to download the free eBook: Service Account Security for Dummies.
For seamless service account management from discovery and provisioning through decommissioning, try Account Lifecycle Manager for free:
Account Lifecycle Manager


