Privileged session monitoring and recording: what you should know
Accountability is not a bad word! It goes hand in hand with PAM security—no matter what vertical or size of an organization. Every privileged account needs to be secured.
Session recording provides the visibility and accountability to keep users and organizations protected while shining a light on nefarious acts within privileged accounts—even if that is a legit user. Privileged session recordings allow people to view sessions in real-time and review previous sessions to examine the why, the who, and the how privileged accounts were accessed.
First, let’s make sure we’re all talking about the same idea here.
Session monitoring and recording is a feature of a PAM solution that allows organizations to monitor and record the activities of privileged users. Specifically, users who have privileges to access business-critical sensitive systems and data. This ensures that privileged users are not misusing their access or that bad actors are not working in the dark attempting to compromise the system’s security.
How Session Monitoring and Recording works
Session monitoring and recording tracks and records the actions of privileged users accessing a specific privileged account. This includes logging keystrokes, capturing screen activity, recording file transfers, and system configuration changes.
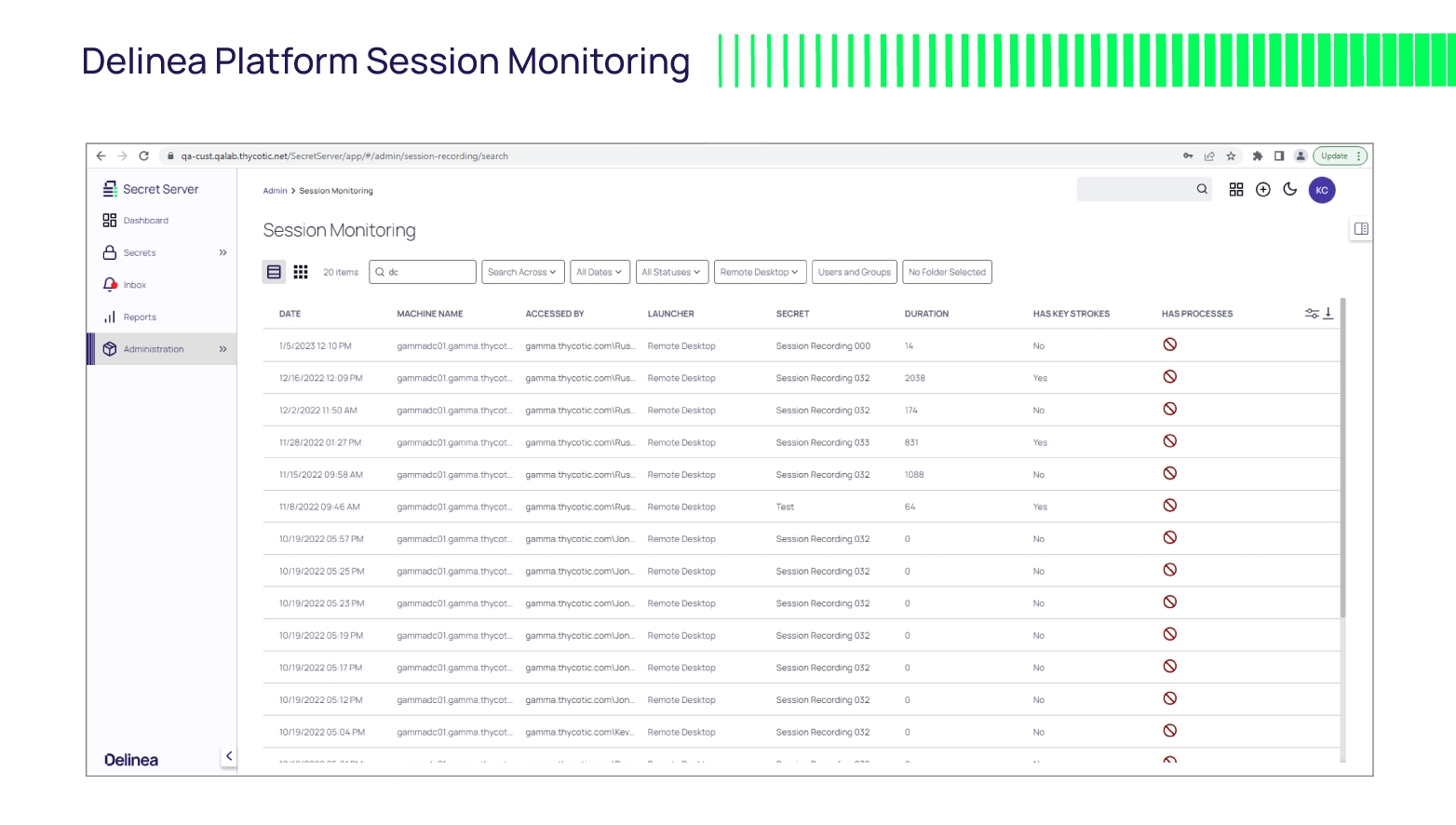 Quickly find recorded sessions
Quickly find recorded sessions
Let’s take it one step further.
If a privileged user launches an application locally, the session recording will capture whatever the user accesses, providing you with a viewable recording of the user’s session activities. These session recordings are auditable, meaning a session recording can be reviewed and connected to a user, accessed accounts, and what the user did during the session. It’s important to note that video recording is the critical component here.
Capturing keystrokes during session recording in locally accessed applications should be done with caution because you risk recording keystrokes not intended for that session which could be a liability.
If a privileged user accesses an application using an SSH proxy or RDP proxy, the session recording captures the screen activity in real-time, along with keystrokes. Keystrokes are captured in this use case as proxy access ensures that all activity is specific to actions on that privileged account.
Please note that with any session monitoring and recording feature, you should be able to customize what you capture. It is critical that session recording features can be customized to meet an organization’s specific needs, such as by enabling or disabling certain types of data capture. For example, disabling keystroke capture for specific sensitive applications.
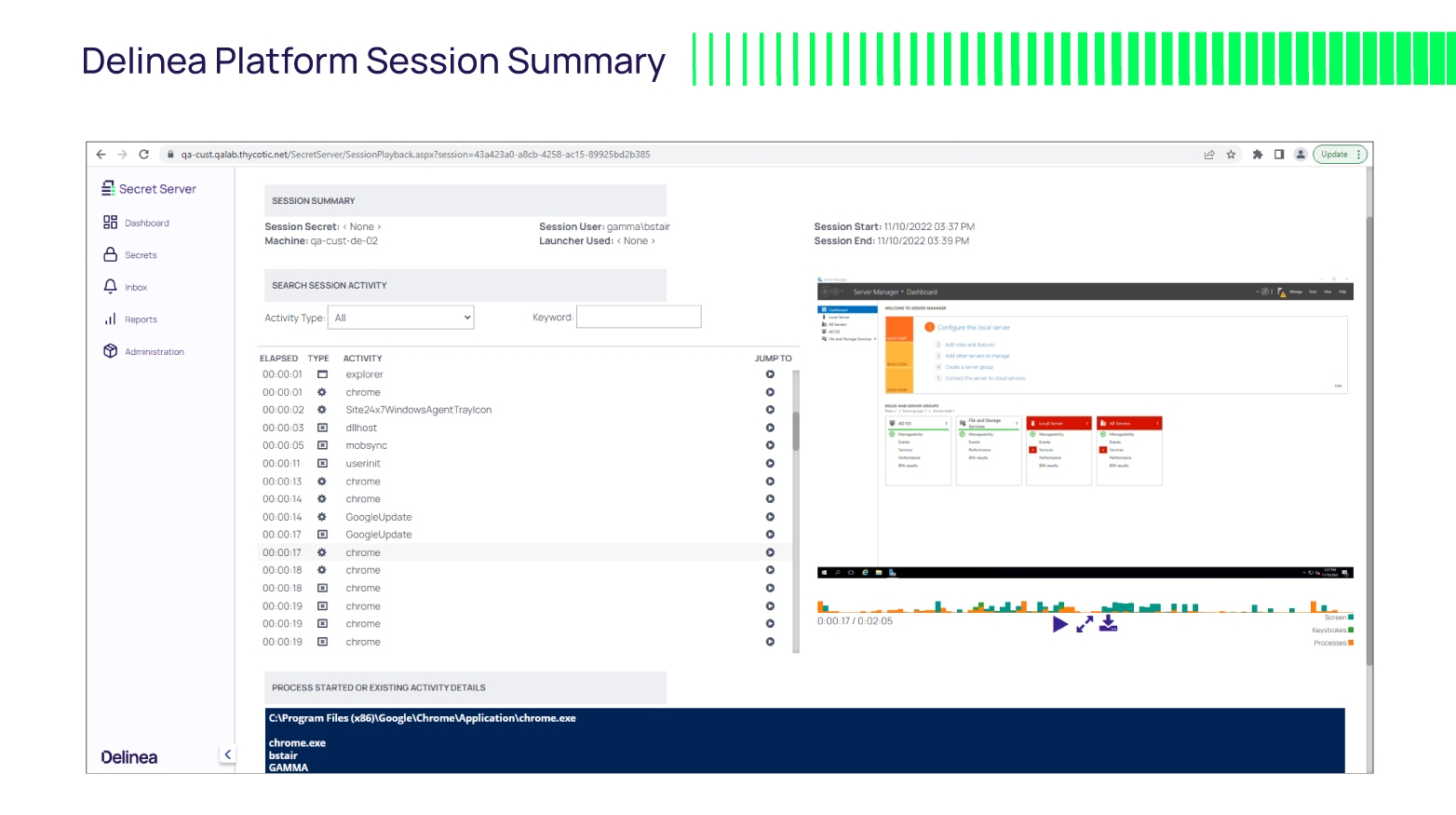 Session Summary provides the admin context, such as activity heat map, processes ran, keystrokes, and metadata on the session itself
Session Summary provides the admin context, such as activity heat map, processes ran, keystrokes, and metadata on the session itself
Method Options
There are options when it comes to capturing activity by privileged users who access business-critical systems and data. Each option comes with advantages and disadvantages.
- Agent-based session recording: In this method, agent software is installed on each system that needs to be monitored.
- Client-based session recording: A client software is installed on each system that needs to be monitored.
- Proxy-based session recording: In this approach, a proxy server is placed between the monitored system and the network.
The session data from any of the above methods is typically stored in an audit log, which can be reviewed and analyzed to identify any suspicious or unauthorized activity. It offers accountability for each user on each session and protection for the user and the organization.
Session monitoring and recording can also help organizations comply with regulatory requirements, improve security, and reduce the risk of data loss or security breaches. It can also be used to troubleshoot issues, perform incident response, and support compliance reporting.
It's critical to understand that recording everything is not best practice. Those who have experienced a compromise may think recording everything is the best approach, but doing so would create an unmanageable amount of recorded data to comb through. Storage and labor costs to review all this data would not be feasible for most organizations.
Pros of privileged session monitoring and recording
Session recording has several benefits that far outweigh any cons when recording privileged sessions.
- Improved security: By monitoring and recording the actions of privileged users, organizations can identify and prevent potential security threats or misuse of privileges.
- Compliance: Session monitoring can help organizations comply with regulatory requirements by providing a record of privileged user activity that can be used for auditing and compliance reporting purposes.
- Risk reduction: Session monitoring can help reduce the risk of data loss or security breaches by providing visibility into the actions of privileged users and suspicious activity.
- Incident response: Session monitoring data can be used to investigate and respond to incidents involving privileged credentials, such as security breaches or data loss.
- Troubleshooting: Session monitoring data can be used to troubleshoot issues related to privileged user activity, such as system configuration changes or file transfers.
- Improved operational efficiency: By automating the process of tracking and recording privileged user activity, session monitoring can help organizations improve operational efficiency and reduce labor costs.
Cons of privileged session recording
Although the benefits of privileged session recording outweigh the negatives, it's important to note them.
- Cost: Implementing and maintaining a privileged session recording system can be costly, particularly if it involves deploying software agents or Remote Desktop Service (RDS) Hosts on multiple systems.
Note that some PAM providers require you to use an RDS Host proxy which drives up costs, so make sure you ask your rep (Delinea does not require this). - Complexity: Privileged session recording systems can be complex to set up and manage, particularly if they involve multiple systems and types of data capture.
An easy way to avoid this is to make sure it's part of your PAM security solution – like Delinea’s easy-to-use Secret Server. - Privacy: Some users may be concerned about their privacy if their activity is being monitored and recorded, especially if the recorded data is being stored and potentially shared with others.
Training privileged users and session recording customization are essential for reasonable, effective privilege session recording. - Performance: Capturing and storing data about privileged user activity can place additional demands on system resources, impacting performance.
Monitor and record highly privileged accounts to better manage the data captured and reduce performance issues. - Storage: Storing recorded data about privileged user activity can require a significant amount of storage capacity, which can be expensive to maintain over time.
Make sure your PAM provider can do this for you with little to no additional cost.
While privileged session recording can provide valuable benefits in terms of security, compliance, and risk reduction, making it much more beneficial for the user and the organization, it’s important for organizations to carefully consider both pros and cons when implementing and maintaining a session recording system.
Session Recording Best Practices
Here are best practices that can offer guidance in recording and monitoring privileged sessions:
- Manage: Understand which accounts are highly privileged and make sure those accounts are included.
- Define: Clearly define and document each user's privileges and take a least-standing privileged approach to each identity.
- Enforce: Enforce strong authentication protocols for privileged users, such as Multi-Factor Authentication (MFA).
- Audit: Implement audit logs to track and record the actions of privileged users.
- Review: Regularly review and analyze the audit logs to identify suspicious or unauthorized activity.
- Plan: Establish policies and procedures for responding to incidents involving privileged users, such as revoking their access or escalating the issue.
Overall, session monitoring and recording gives organizations visibility and accountability into the actions taken by privileged users in privileged accounts. This helps improve security, compliance, and operational efficiency. An organization should provide training and guidance to privileged users on how to use their privileges responsibly with established policies and procedures to support privileged account use.
Risks from bad actors are constant- session monitoring and recording features are valuable in the fight to mitigate risk. To learn more about session monitoring and recording Delinea offers, click here.
IT security should be easy. We'll show you how


