PAM cloud architecture for cyber resilience
To achieve cyber resilience, the name of the game is service availability. Can you continue to operate and provide services 24 hours a day, seven days a week, 365 days a year?
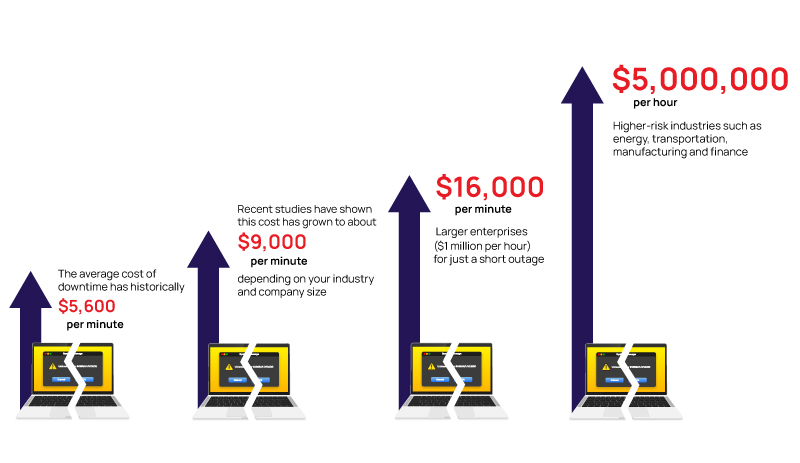
The average cost of downtime has historically been about $5,600 per minute, but recent studies have shown this cost has grown to about $9,000 per minute, depending on your industry and company size. For larger enterprises, the downtime can cost over $16,000 per minute ($1 million per hour) for just a short outage.
For higher-risk industries such as energy, transportation, manufacturing, and finance, the average cost of downtime tends to be over $5 million per hour.
A cloud-native architecture can improve cyber resilience for organizations—as long as certain conditions are met. Cloud computing offers a highly scalable and flexible infrastructure for IT and security operations. Cloud-native architectures have the potential to improve disaster recovery and business continuity by providing continuous backup, failover, and data recovery.
However, if core infrastructure components that integrate with your cloud architecture cannot support your need for scalability, flexibility, and redundancy, then you are not as resilient as you may think. Non-cloud-native components can introduce friction and slow you down. These components may introduce vulnerabilities that can open the door to cyberattacks. Most importantly, they increase the likelihood and scope of downtime for your critical IT systems and business operations.
To protect your organization from disruption, cloud architects must create a robust and reliable architecture that can withstand challenges and support business needs. Specifically, the core cybersecurity components that underpin your architecture—including PAM—should be cloud-native. Only then can you ensure that your organization can continue to access systems and contain the damage when under fire.
Critical components of a resilient PAM cloud architecture
A well-designed PAM cloud architecture, such as the one we've built at Delinea, starts with the basics: access control and authorization policies, encryption, and monitoring. And, in fact, most PAM solutions on the market will have fundamental security controls in place.
![]() A robust encryption mechanism can provide an additional layer of security, making it harder for cyber attackers to access sensitive data. Data should be encrypted in transit and at rest.
A robust encryption mechanism can provide an additional layer of security, making it harder for cyber attackers to access sensitive data. Data should be encrypted in transit and at rest.
![]() Robust monitoring tools and mechanisms can detect and respond to unauthorized access and anomalous behavior.
Robust monitoring tools and mechanisms can detect and respond to unauthorized access and anomalous behavior.
![]() Isolated cloud infrastructure, redundancy, multi-tenancy, and the ability to scale each helps you meet compliance requirements, isolate business units, minimize attack vectors, and scale to keep up with demand.
Isolated cloud infrastructure, redundancy, multi-tenancy, and the ability to scale each helps you meet compliance requirements, isolate business units, minimize attack vectors, and scale to keep up with demand.
That said, make sure your architecture is set up to ensure the highest levels of availability and uptime of 99.995% or higher. You need to make sure your systems can continue to operate even if one or more components fail power outages, are hit with cyberattacks, or other natural disasters.
What makes a cloud PAM architecture redundant and resilient?
A key tenet of a redundant, resilient architecture is implementing failover mechanisms to distribute and protect workloads. There are several factors to consider.
Availability zones vs. regions
A cloud architecture that uses availability zones can be less resilient if the same availability zones in one region share common services with the other availability zones. For example, if a shared service that spans multiple availability zones goes down in one zone, it goes down for all zones. In contrast, cloud regions are more isolated from other regions and therefore are more resilient to service outages.
Load management and failover
Proper load management can route requests to distribute workloads efficiently. For example, should region 1 be busy and region 2 not as busy, you can decide to shift the workload. What’s more, if region 1 is not operational, traffic can route automatically to region 2.
Additionally, services should be able to scale independently and automatically. With proper load management and auto-scaling services, the system can scale to meet the demands and ensure performance.
Delinea’s cloud architecture uses active-active clusters, where all services have a minimum of two active nodes in each cluster. This is more resilient than an active-passive or active-standby approach because there is no lag time for failover. It happens automatically and is seamless to the service consumer (human or machine).
Learn more about how Delinea cloud architecture enhances scalability.
Monolith vs. microservices
There are different ways to architect cloud services like PAM. One option is to create a single service approach in which everything about that solution happens within that same service. With that approach, if one part of that service breaks, the whole monolith goes down.
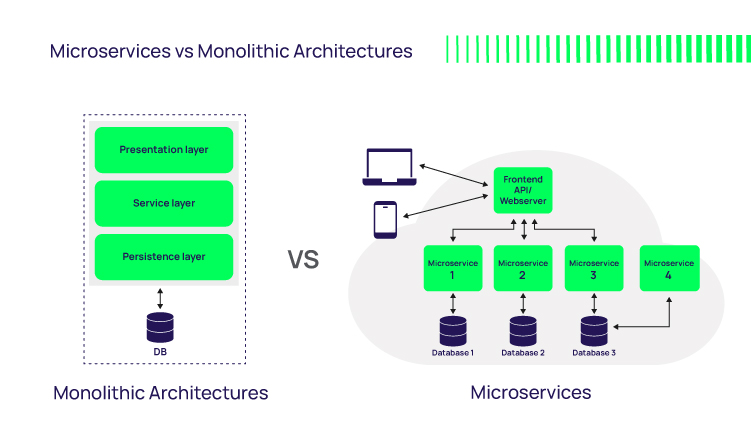
In contrast, the Delinea PAM solution is broken into more than 70 different services. Each one of the services is completely isolated and independent from the other services. With this model, if one of those services crashes, the other services continue to operate.
For example, let’s say the Delinea Marketplace goes offline briefly. Users can still log into the Secret Server application. They can still get to their secrets, and still provide remote access because those core services are separate and independent. This model also allows us to auto-scale up and down at the microservice level, using nodes as needed to support the required capacity.
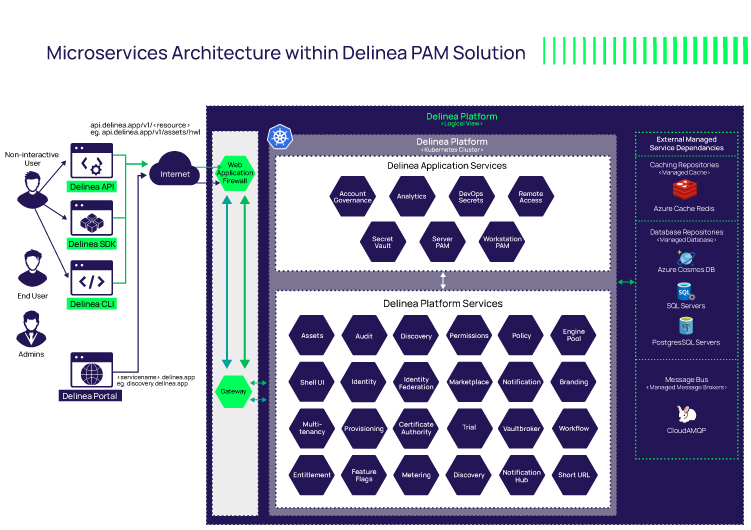 Because of this architecture, customers receive zero downtime upgrades and updates. We can perform continuous micro-releases and system-level upgrades without any downtime, and no professional services are needed to support you.
Because of this architecture, customers receive zero downtime upgrades and updates. We can perform continuous micro-releases and system-level upgrades without any downtime, and no professional services are needed to support you.
Again, if any of the critical services in your PAM architecture aren’t truly cloud native, you’ll need to bake downtime for updates into your planning. If you need to plan outages to run vulnerability scans, upgrade to new software versions, or apply patches, you are less cyber resilient.
While planned outages may be fine 90% of the time, Murphy’s Law says that 15-minute window is when an important customer is depending on access to your systems, or when a cyberattacker will strike. Hit a snag, and 15 minutes could easily turn into an hour of downtime.
Back-up secrets vault
Imagine a cyberattack hits your cloud PAM solution, including your enterprise password vault. Your incident response team is struggling to respond and contain the damage, but they can’t get access to critical systems because the attacker is blocking them. That’s why as part of a cyber resilient PAM solution, you need a back-up vault.
Delinea Secret Server offers cyber resilient secrets, functionality that automatically gives you access to a back-up vault so you can get the access you need to combat the attack and get back to business.
We’d be happy to share the architecture of Delinea’s cloud PAM with you to ensure it meets your uptime and cyber resilience needs. Let us know if you’d like more information from one of Delinea’s cloud architects.
PAM in the Cloud. Powerful. Secure.


