What do Equifax, HBO, Uber and Yahoo all have in common?
A consumer rating agency, a cable network, a transportation company, and a web services provider. What ties them together? Sure, they were all impacted by very high-profile security breaches. But, if you dig a little deeper, you’ll find these organizations had a lot in common before, during, and after their respective breaches. And those commonalities can teach us valuable lessons.

A quick recap
Equifax became the latest poster child for cybersecurity after it announced criminals had gained access to the financial data of 143 million people. The massive breach led to 23 class-action lawsuits, a $4.3 billion loss in market cap, and the departure of senior execs.
Equifax inherited the “poster child” title from Yahoo, which suffered an attack back in 2013 and took the following four years to come to the conclusion that every last user account--including Yahoo mail, Flickr, Tumblr, and Fantasy--had been compromised. All three billion of them.

Other companies newly inducted into the Fox Business Cyber Hack Hall of Shame include HBO, where cyber criminals claim to have stolen 1.5 terabytes of proprietary data, and Uber, where cyber thieves taxied away with 57 million users’ personal information.
So, what did they all have in common besides the obvious? Three key elements:
All the Breaches Were Avoidable
All these breaches, no matter how sophisticated the attack, could have been prevented. Whether due to a lack of interest, focus, urgency or all three, bad decisions were the key culprit behind these breaches and thousands of others occurring every day. According to IT analyst Forrester, two-thirds of all companies have breached an average of five times, despite spending $80 billion on security last year.
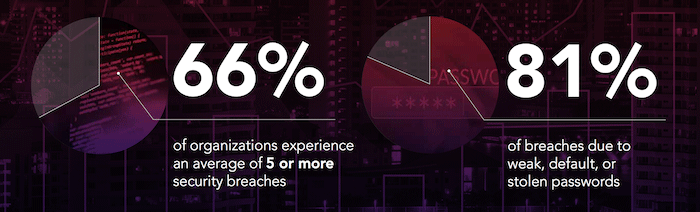
Those numbers tell us something: We’re not setting priorities effectively. Protecting the data of our organizations and our customers must be paramount to all other business issues, every single day. And it’s not. Companies take an average of 193 days to patch known vulnerabilities, which is the very reason Equifax was breached in the first place.
Second, it tells us that the vast majority of organizations are taking an outdated approach to cybersecurity. In lieu of stringently following best practices, we’re throwing vast amounts of money at the problem. We’re carpet bombing and crossing our fingers rather than responding with effective surgical strikes. That’s expensive and ineffective.
All the Breaches Had an Identity Component
While most media reports focus on how the initial breach occurred, they’re missing the most crucial part of the story. The great majority of successful breaches leverage compromised identities.
Access is just the first step. Once inside, cyberthieves install malware that listens for privileged user credentials. Once they have those, they can move unfettered throughout the network, gaining access to companies’ most valuable information. It’s the credentials—and the privileged access that comes with them—that count.
According to Verizon, compromised identities were responsible for 80 percent of all data breaches in 2017. It’s time to pull the focus off the point of entry and start severely limiting the damage cybercriminals can do once inside.
Is security having an identity crisis?
Despite cybercriminals’ focus on identity, most organizations aren’t making the connection between breaches and compromised credentials. In 2017, companies spent less than five percent of their total security budgets on identity and access management—the very technology that would help prevent these breaches.
All the Breaches Were Poorly Managed
Hollywood and the political arena aren’t the only places where bad behavior has led to serious repercussions this year. Once the neglect had resulted in a worst-nightmare scenario, Equifax turned itself into a case study in poor decision management and harebrained leadership. It took weeks to announce the breach had even occurred and what followed was a comedy of errors that would make Shakespeare cringe.
Yahoo’s timing was far worse—it took them years to come completely clean. They managed to frustrate millions of users who, had they been given the truth, could have addressed problems with their email accounts before any additional damage was done. It’s inexcusable to not adequately protect your data in this day and age, but the response here was beyond reproach.
Is there a way out of this mess?
The best way out of the current situation is a program of shared responsibility:
Companies should implement a Zero Trust model which assumes users inside a network are no more trustworthy than those outside. Everything (users, endpoints, resources) is untrusted and must be verified. Security vendors should implement machine learning for behavior-based fraud detection that assigns a risk level of each individual transaction and responds accordingly. Consumers should demand multi-factor authentication for every single account, or find new vendors that offer it. This is something that’s going to take the entire village working together to solve. The sooner we get started, the better.
This article first appeared in VentureBeat.

Start your least privilege journey here


