Why organizations need adaptive Multi-factor Authentication (MFA)
We hear about high-profile security breaches frequently. Most of these breaches exploit the system login credentials of end-users to get into the company’s network. Leading organizations are recognizing this and are beginning to focus on better securing end-user identities. Multi-factor Authentication (MFA) is becoming a very popular method for doing this as MFA requires a user to provide more than just a password to access the network. These additional factors of authentication require the user to provide something that only the user knows, has, and is.
As a best practice, when implementing MFA, it should be set up across the entire company enterprise, not just in small groups. All applications in the cloud as well as those on servers inside the company network should use MFA. It should also be deployed for users who access the company network from remote locations, as well as any business partners who require access to company information.
What is adaptive Multi-factor Authentication?
MFA also has the ability to be configured as "adaptive," meaning it can require a user to use certain factors to authenticate based on how the user is logging in, be it from an unknown device such as a new mobile phone, at a different time or from a different location than usual. MFA can look at these different contexts and require more difficult factors to ensure the user is who he or she says.
This is how adaptive MFA works:
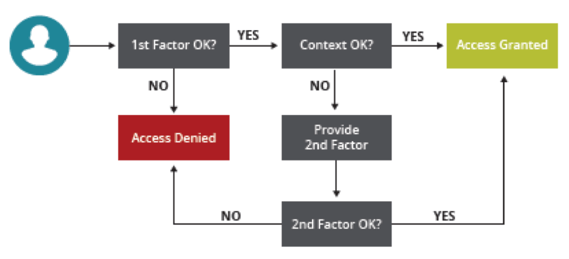
One of the main benefits of adaptive MFA is that it improves the experience of the user. Instead of the user always being asked to provide multiple authentication factors, the user will only be asked for an additional factor when necessary. For example, a user logging into the corporate network from a corporate managed computer will only be asked to provide one factor of authentication -- a password. However, a user logging into an unknown device from an unknown network will be asked for multiple authentication factors.
Multi-factor Authentication options
For MFA to be successful, the user experience is critical and organizations must balance user convenience and security. There are several authentication factors to choose from and the organization implementing the MFA solution can decide what factors they want to use and which ones they don’t. The authentication methods currently available include:
- Hardware Tokens – These are small physical devices that a user can carry that helps with authentication. They come in many forms like smart cards with a card reader, key fobs with a changing authentication code, or a USB device that will generate a one-time use passcode that the user enters when prompted to do so.
- Soft Tokens – These are software-based applications that generate one-time-use passcodes and are usually found on mobile devices. They use technology where a notification is sent to the mobile application and the user can press a button to approve or decline the authentication request based on whether the user made the request or not. Soft tokens are generally cheaper and easier to use than hardware tokens.
- SMS/text message – A one-time use passcode is texted to the user’s mobile phone and the user can then submit the passcode into the network login screen.
- Phone call – With this method, a user receives a phone call to a number that the user pre-registers. If the user provides the correct response to the voice prompt, authentication will continue.
- Email – The user will receive an email with a link to verify the authentication request. If the user clicks the link, authentication proceeds.
- Security questions – In this case, users are given pre-defined security questions to answer in order to proceed with authentication.
- Biometric – These include fingerprint recognition, a retina scan, facial recognition, and so on. Most smartphones have these methods built into them so they are very popular options for MFA.
When an organization offers a choice of MFA options to their user population, the users can decide which ones work best for their situation which improves user experience and promotes corporate data security.
Single Sign-On (SSO) and least privilege
MFA is a very secure method of protecting corporate data and networks but combining it with other identity security solutions such as Single Sign-On and least privilege access allows for even better security.
SSO is helpful in that it helps users avoid having to create and remember passwords for each application -- especially since those passwords will often be created quickly, causing them to be weak and easily guessed by an intruder. SSO is most commonly used in a cloud computing environment. SSO and MFA combined help create more secure cloud applications and data.
By implementing least privilege access into the network, users are provided with the least amount of access rights to data that they need to perform their duties. When this is in place with MFA, it will further protect data from the risks associated with compromised credentials.
When implementing MFA, it should not be considered a completed setup. As networks, applications and user populations change so do security vulnerabilities. Because of the constant change, organizations should periodically reassess their MFA technology to ensure it continues to meet the needs of the company and entire organization and that it is applied and working properly.
5 best practices of MFA
In conclusion, MFA has become an essential security tool for data protection. Because of this, Delinea recommends the following best practices:
- Implement MFA at depth – Partially deploying it in organizations does very little good in protecting important applications and data.
- Use adaptive MFA – This will make for a better user experience and security.
- Provide a choice of MFA methods – By giving users several options to choose from, the user experience will be more positive for different user populations.
- Combine MFA with SSO and least privilege access – By combining multiple levels of security, the risk of compromised data is even lower.
- Continuously re-evaluate MFA – Verify that the deployment continues to meet the needs of the organization and its users. Make changes as necessary.
Learn more about securing end-user access in our Definitive Guide to Securing Privileged Access.

Not all MFA solutions are created equal


