In recent macOS releases, Apple has been drawing attention to third-party software that uses technology like kernel extensions and system extensions. This technology allows users to install components or apps that extend the native capabilities of the macOS operating system.
Apple’s deprecation of kernel extensions (KEXTs) and introduction of Endpoint Security Enabled System Extensions (SYSEXs) as a replacement means big changes for security in macOS platforms.
The shift to SYSEXs significantly reduces attack vectors
It’s important to understand the implications of Apple’s security shift when it comes to third-party software. The difference between the two extension systems is that KEXTs execute their code at the macOS kernel level, while the newer SYSEXs run at the more tightly controlled user level. The shift to SYSEXs significantly reduces the attack vectors available to cyber criminals because it runs as a user.
This shift also changes the way that Delinea’s Privilege Manager macOS agent operates.
There are a few pertinent topics if you manage macOS endpoints within your environment:
- KEXT vs SYSEX installation on Catalina and Big Sur
- KEXT -> SYSEX and what it means
- Leveraging the authorization database (authorizationdb)
- sudo Plugin
Installation on Catalina and Big Sur
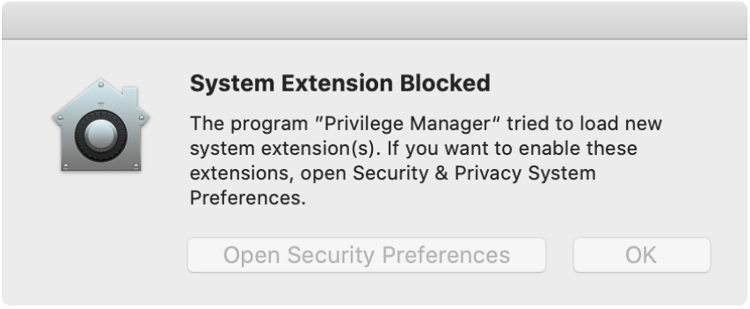
When third-party components or apps are installed on a macOS endpoint, the user is informed that a product is trying to load a system extension and that their consent is required to allow it.
Once Privilege Manager is installed, the end user must allow it to satisfy the Transparency, Consent, and Control (TCC) requirement. This end user approval is required for the product to be fully functional.
The warning dialogs and the need to grant Full Disk Access to the SYSEX on Catalina and Big Sur can be removed through Privacy Preference Policy Control (PPPC) configuration profile payloads.
Using a Privacy Preference Policy Control Configuration Profile Payload
The concept of TCC introduces PPPC configuration profile payloads, which allow for enterprises to manage and simplify the installation process of products that leverage KEXTs and SYSEXs for their end users through Mobile Device Management (MDM). When properly configured, this eliminates the need for the user to deal with the dialogs below.
Delinea can provide the necessary configuration payloads that can be loaded into or leveraged with your MDM solution.
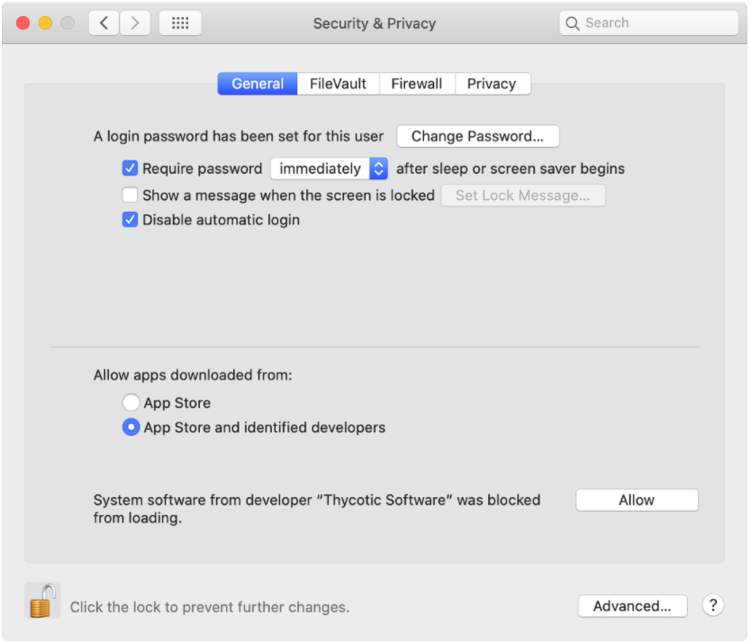
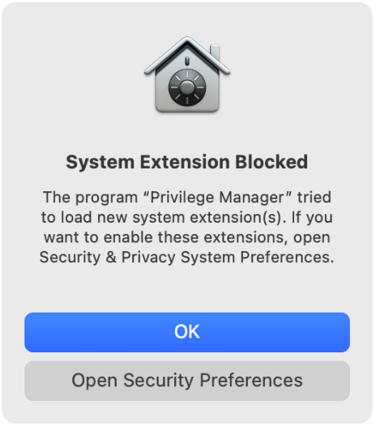
Let’s look at the system dialogs; first the Catalina KEXT warning and Security & Privacy dialog.
Note that this pop-up doesn’t tell the user it’s a KEXT, but that it’s a system extension that will be incompatible with a future version of macOS. Hopefully, Apple fixes this misnaming in future upgrades.
Here, the user needs to click “Allow” so that Privilege Manager’s KEXT can run. No further action is required by the user, but there are some additional steps that need to be taken on the admin side to ensure the product can read from users’ TCC protected folders.
If you prefer to continue using KEXT on Catalina, you can set up a PPPC configuration profile.
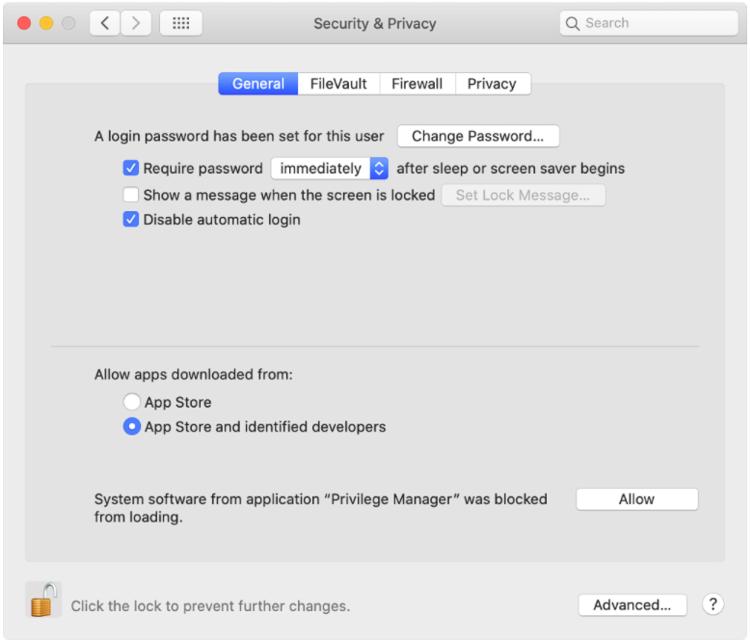
And now let’s look at the Catalina SYSEX warning and Security & Privacy dialog.
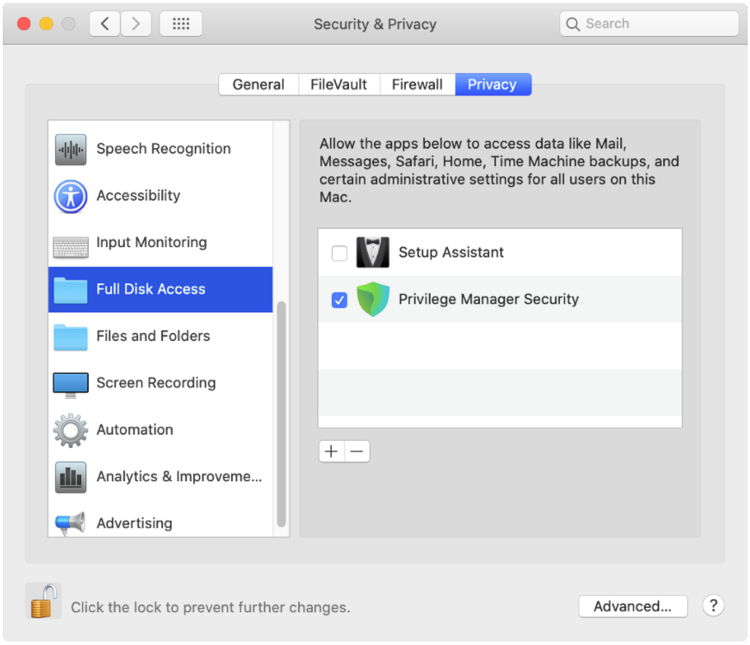
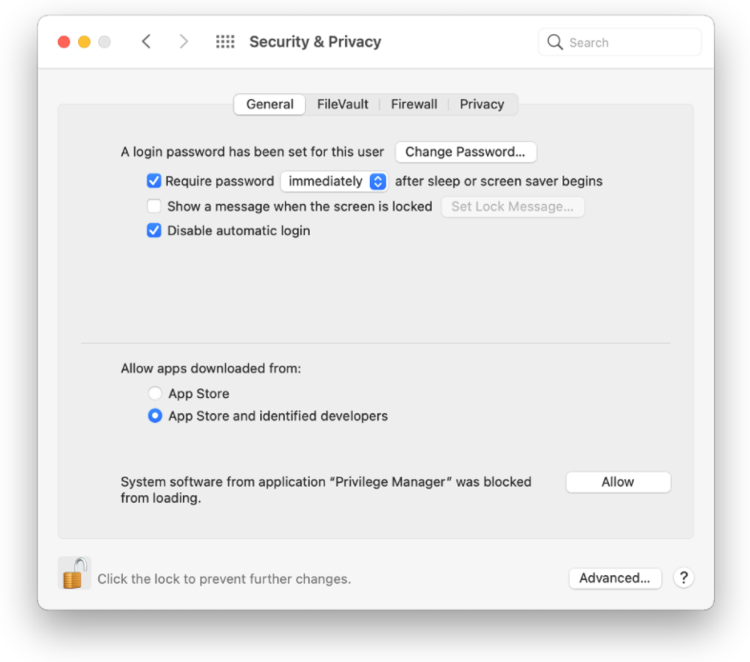
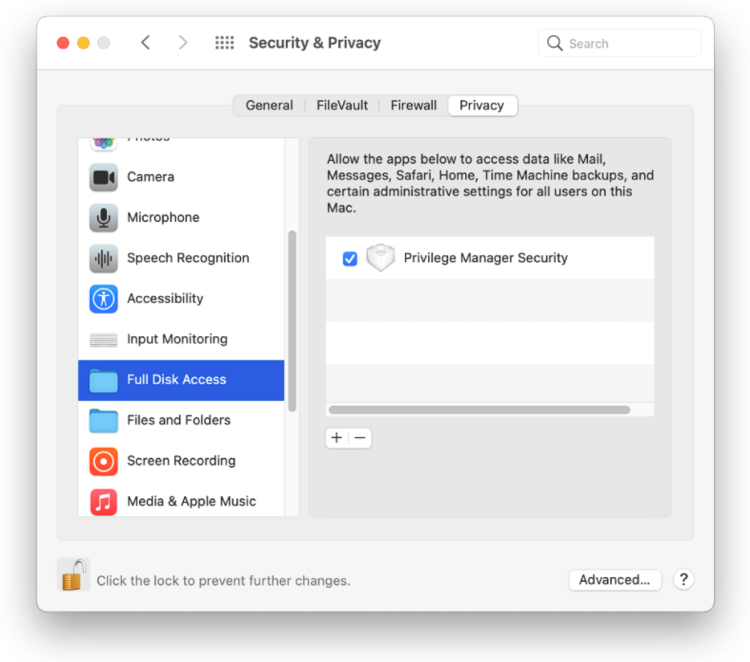
Here, the user needs to click “Allow” so that Privilege Manager’s SYSEX is allowed to run. If you’re not delivering a PPPC configuration profile via MDM to manage this, the user will need to give Privilege Manager Security Full Disk Access, as shown below.
These dialogs change slightly in Big Sur.
Here, the user needs to click “Allow” so that Privilege Manager’s SYSEX is allowed to run. Again, if you’re not delivering a PPPC configuration profile via MDM to manage this, the user will need to give Privilege Manager Security Full Disk Access, as shown below.
Kernel Extension (KEXT) -> System Extension (SYSEX)
The Privilege Manager macOS agent is composed of several components and at the core are the KEXT and ThycoticACSvc daemon. These two work together to allow, deny, and elevate applications according to policy.
With the deprecation of KEXTs in macOS Catalina, we are combining the functionality of these two components into the com.delinea.acsd system extension that is hosted by Privilege Manager.app.
In the KEXT version of the macOS agent, we relied on the KEXT to adjust processes so that they could run elevated. With the SYSEX version, we are no longer able to do that. We now leverage a sudo plugin to provide similar functionality.
Leveraging the AuthorizationDB
Many privileged operations are governed by rules in the authorizationDB and these rules determine what credentials are required to perform certain tasks depending on the right being authorized.
To address restrictions placed on the macOS agent because we no longer have the fine-grained access and control provided by our KEXT, we’re extending how we leverage the authorizationDB to provide least privilege for users. In addition, we’ll be expanding on this to provide coverage for more and more privileged operations.
sudo Plugin
Apple’s Endpoint Security framework is a great leap forward for developers, but it prevents us from performing process elevation of command-line binaries like we have done in the past. To address this, we’ll be replacing the methodology we used in the KEXT with a sudo plugin.
Starting with version 1.8.0, sudo supports a modular framework that allows third-party policy evaluation to govern whether a command is allowed to run. This architecture allows us to extend sudo functionality without replacing it and without introducing too much change to users’ workflows.
If your users are already running privileged commands via sudo and a Privilege Manager policy to elevate it, then there is nothing they need to change. However, if you have elevated some commands specifically via policy and filters, you may need to re-evaluate those and modify them so that your users can use sudo to perform those commands.