Seven reports you can share with auditors and execs to demonstrate proactive privilege management
All major compliance bodies recommend or require a least privilege policy to protect sensitive data. Removing local administrative access on user workstations is a fundamental strategy for endpoint security to protect against both internal and external threats.
Auditors will see that you have implemented a proactive security strategy to prevent malicious activity and accidental data breaches
By removing admin rights—including hidden or hard-coded passwords—you can block malware from hijacking local credentials to infiltrate your IT environment. Adhering to a least privilege policy also demonstrates that you have taken necessary steps to ensure users have access only to the information and systems they require to do their jobs. Auditors will see that you have implemented a proactive security strategy to prevent malicious activity and accidental data breaches.
Simple, sharable reports for an actionable audit trail
Achieving compliance can be a time-consuming process that impacts many parts of your IT operations, from the InfoSec group to systems administrators, desktop support teams, and application developers. Whether you are working to achieve PCI, HIPAA, EUGDPR or any other compliance standards, you are going to need an audit trail that demonstrates the steps you have taken to ensure data security.
Having an effective audit trail means having the ability to easily construct and share reports at any time. It also means being able to explain to internal and external reviewers what the reports indicate and taking action on what you learn.
We built Privilege Manager reports (Privilege Manager is our privilege management and application control software) so that you can easily view, customize and share them with your InfoSec and audit/compliance teams. You’ll be able to demonstrate how you are protecting endpoints by following security best practices for least privilege and application control. On an ongoing basis, reports will help you manage your least privilege and application control policies and enhance them over time.
Reports our customers love
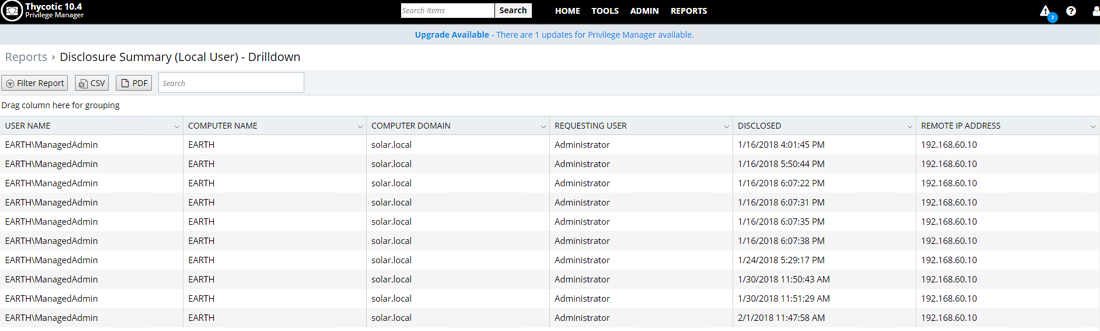
1. Passwords that have been disclosed
Views users who requested passwords, users who disclosed them, as well as date and time.
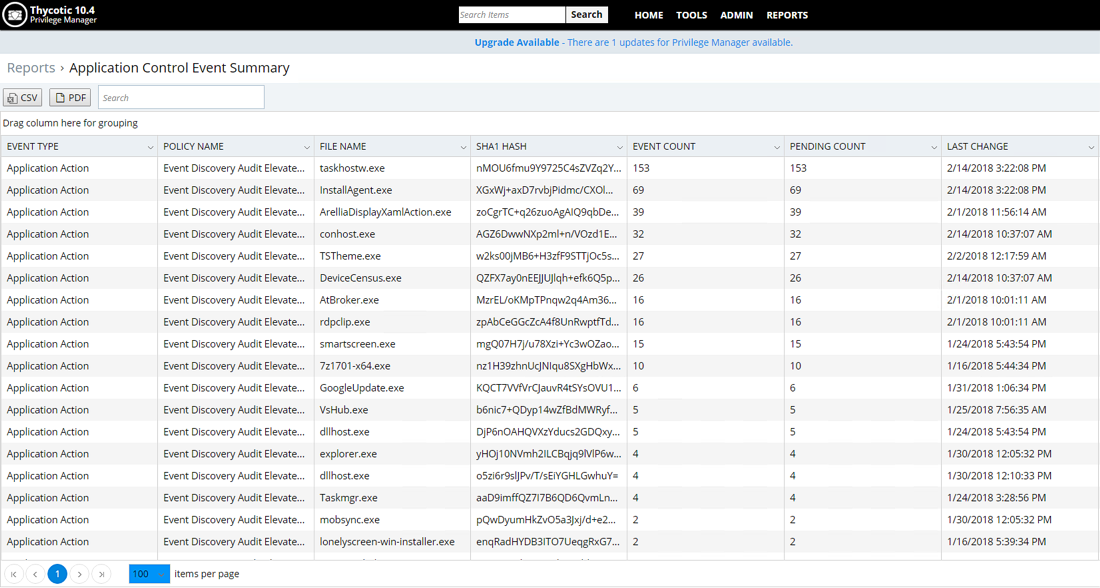
2. All executables across all endpoints
Reports can be customized for certain time periods, publishers, and endpoint/computers.
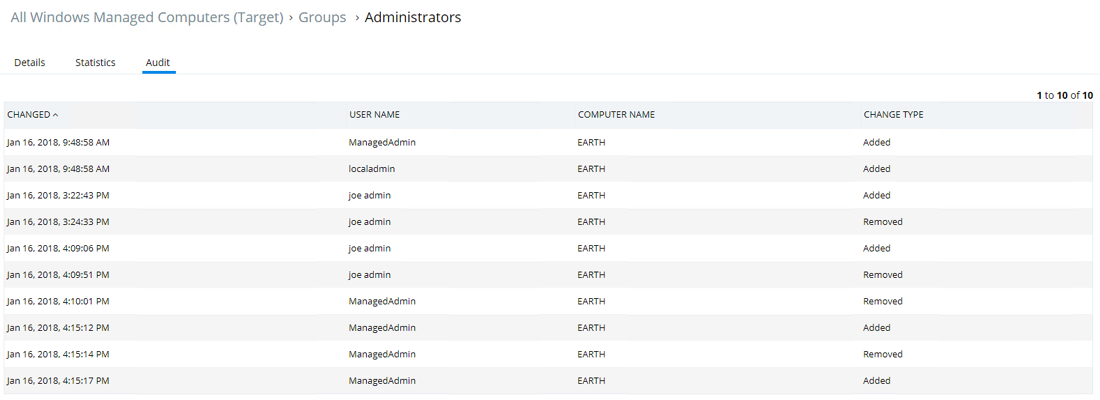
3. Membership audit of all built-in (“well known”) groups and all customer (“non-well known”) groups
This quick report is a good double check to confirm that groups have the correct membership and whether custom groups are being created, possibly with privileged access.
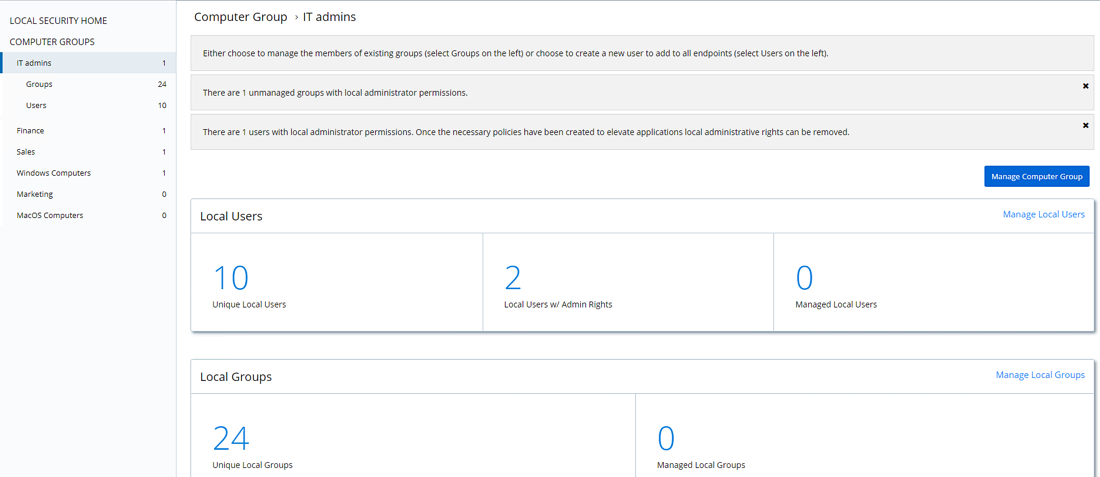
4. Endpoints transitioned to/in compliance with a least privilege policy
This dashboard will show you how many users have admin rights and how many are managed by least privilege and application control policies. Those numbers should be the same to ensure full compliance with least privileged standards. At least one group should be managed (the second row of numbers in the dashboard). At first, that group should be the administrators. As other privileged groups within the organization become managed as well, that number will increase.
Delinea also includes tips on the dashboard to guide users to the administrators’ group and to managing the admin accounts. The tips will disappear once you are in compliance with least privileged best practices.
Implementing Least Privilege shouldn't be hard
5. Applications reviewed and governed by a policy for application control
You can list all applications that have gone through approval workflow, including those applications that have been approved with a valid reason.
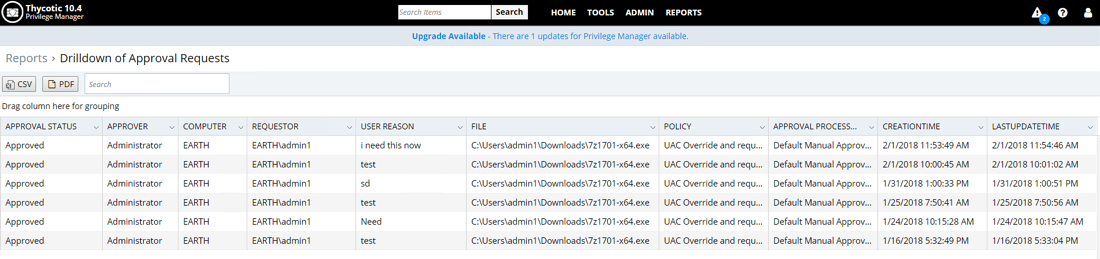
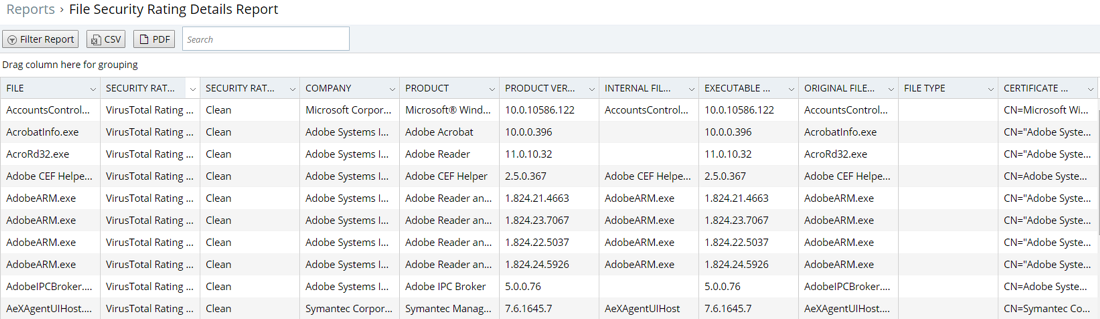
6. Malicious applications successfully blocked from executing
Imagine the latest ransomware attack is in the news and your leadership wants to know if you have been targeted as well? You can demonstrate that your proactive strategy has successfully blocked malware by pulling up the file security rating reputation report.
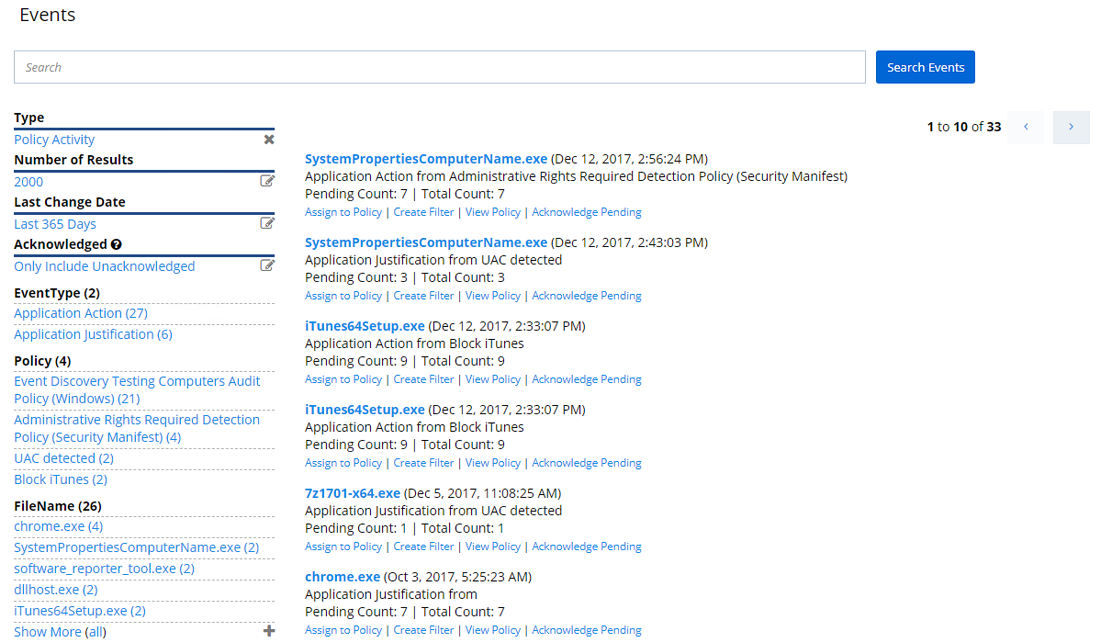
7. Endpoints that are targeted more than average
This report is a great example of actionable insight. An admin can glean info on number of times an unknown application has executed across endpoints or simply a large number of file executions of a particular file on a computer. This could indicate that a particular system needs additional protections, or a particular user needs additional education to avoid being a victim of social engineering.
See for yourself
You can manipulate these reports to track and compare over time to show trends and continued progress.
To get started, run some reports against your own data. Register for our free 30-day trial of Privilege Manager.



