How do CISOs and other IT security professionals make informed decisions about tech purchases? A research survey commissioned by Delinea was conducted among more than 900 CISOs / Senior IT decision-makers across nine countries. The report of survey results takes a close look at how IT and security professionals make technology buying decisions, and what most influences Boards to invest in cybersecurity.
The new report, entitled, Cyber Security Team’s Guide: Balancing Risk, Security and Productivity*, provides several insights into what is driving cybersecurity investments as we head into the budgeting season for the year ahead.
*Please note: the report available here for download is an updated version (2021), and figures may differ from those mentioned in this post.
The good news: The global research study found more than half (58%) of IT security decision-makers say their organizations plan to add more security budget in the next 12 months. Amid growing cyber threats and rising risks through the COVID crisis, survey respondents indicate that boards are listening and stepping up with an increased budget for cybersecurity, with the overwhelming majority, 91% agreeing that the Board adequately supports them with investment. Almost 3-in-5 believe that in the next financial year they will have more security budget because of COVID-19.
The bad news: Even with growing executive management support, CISOs and their security teams must remain vigilant in making their case for cybersecurity investments. Over one-third (37%) of participants’ proposed investments, for example, were turned down because the threat was perceived as low risk or because the technology had a lack of demonstrable ROI. One-third (33%) of survey respondents believe senior management often does not comprehend the scale of threat when making cybersecurity investment decisions.
You can download the full report here*.
Security incidents and compliance help get budgets approved
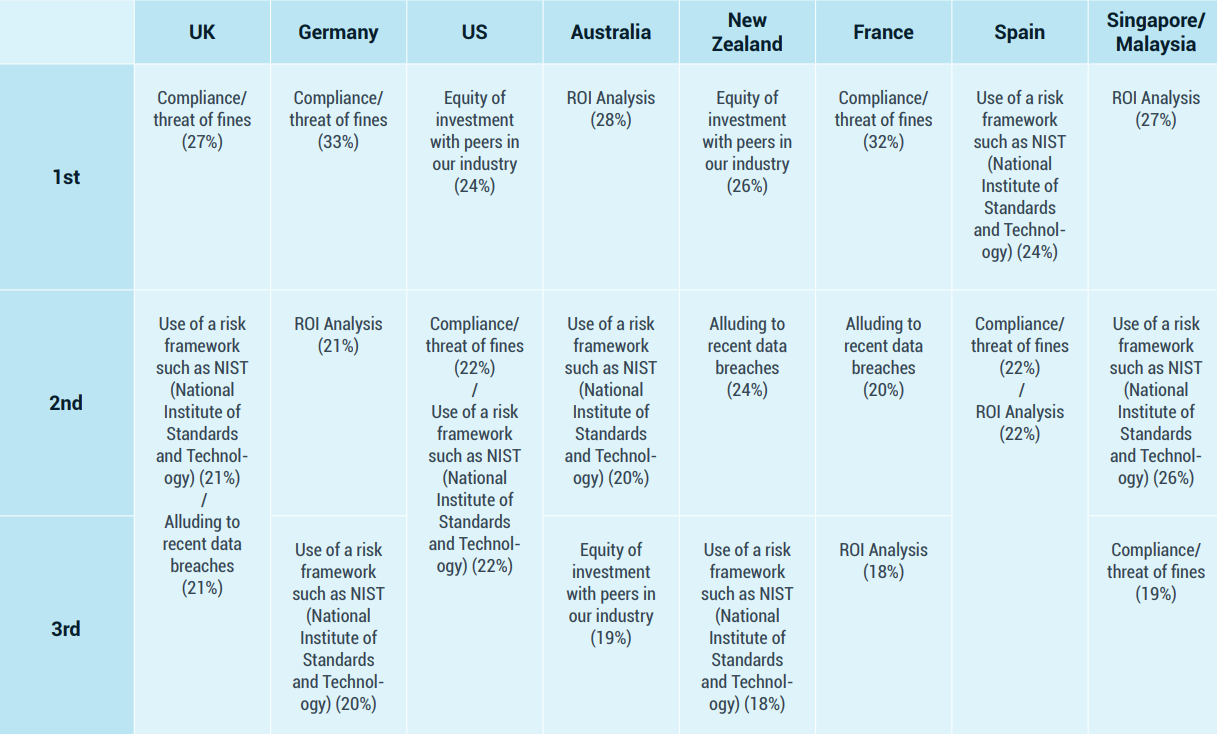
More than three in four survey respondents (77%) said that a security incident at their organization or an audit failure helped convince their Boards to approve investment in new cybersecurity projects. Thus, it is not surprising that compliance appears to be a prime motivator in getting executive management to invest.
Europe, for example, has seen several companies receive significant fines in millions of Euros resulting from a data breach or failure to be compliant with EU GDPR. Here is the breakdown by country.
What to expect going forward
The road ahead for IT and cybersecurity leaders moving into 2022 is complicated. The rapid evolution of threats across perimeter-less networks, along with an ever-growing range of cybersecurity technology choices, complicates IT decision-making.
How do you make real-world decisions about where and when to allocate finite resources that best serve the interests of your organization, both now, and in the future? Are your decisions made on facts versus fear? What kind of evaluation criteria do you want from vendors to help you make the most informed decisions? Here’s what this global survey says about how your colleagues are making technology buying decisions.
Just 17% think their business has its finger on the pulse
Almost half of respondents view their organization as ‘in the pack’ (45%) and only a third consider their companies to be ‘pioneers’ (36%), embracing new technology advancements. Just 17% think their business has its finger on the pulse, prioritizing investment according to the latest security threat.
Sources of information most important to decision-makers
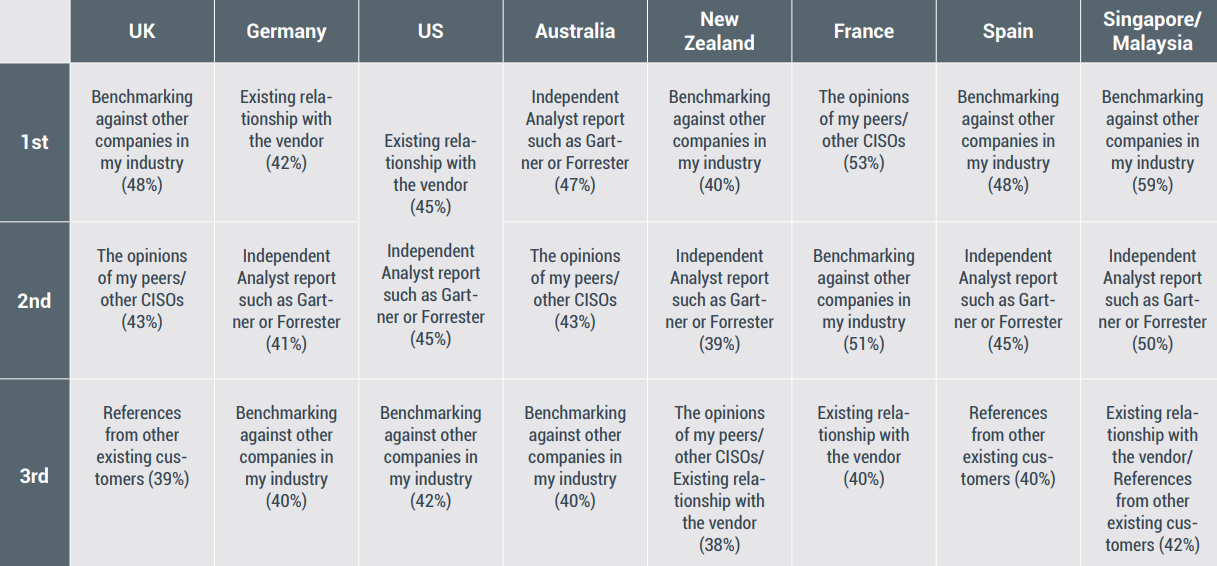
Before purchasing new cybersecurity products, survey respondents highlighted their most important sources of informed decision-making. According to the research, CISOs and other senior IT security decision-makers look most often to their peers for guidance. Benchmarking with other companies in their industry was the top method in decision making with 46% of respondents gauging their efforts in comparison with what their colleagues are doing. Another 43% look to industry analysts as their most important source of information. A significant 39% rely on the opinion of their peers as most important to their decision-making process and 39% rely on existing relationships with vendors.
39% rely on the opinion of their peers as most important to their decision-making process
One of the more interesting aspects of this research is the differences noted between the nine countries involved in the survey. The chart here shows what various countries surveyed indicated as their most important sources of information in making technology decisions.
The UK, New Zealand, Spain, Singapore, and Malaysia, for example, see benchmarking with industry peers as the top source of information in making informed decisions, whereas the USA, and Australia lean toward industry analysts for direction. Germany is a standout by giving important weight to existing relationships with vendors, though all preferences were very close in priority.
What drives the final buying decision?
While product features generally make the most difference when making a final buying decision (44%), it’s interesting to note that 24% of respondents consider the reputation of the company to be the most decisive factor. Another 15% consider their trust in the individual salesperson to be most important in the final decision.
Even though we all like to think that technology purchases are based strictly on rational criteria, it is clear from the research that a vendor’s reputation and trust in an individual salesperson still play a critical role in many final technology purchase decisions.
… IT Ops has the final say in cybersecurity purchase decisions
One highlight from the survey indicates that IT Operations share a significant portion of the purchase decision-making process with security teams. Among survey respondents, IT Ops has the final say in cybersecurity purchase decisions (38%) compared to the security team and CISO (32%). France appears to counter this trend, where operations have much less influence in the final say (18%).
A warning on cybersecurity investments as we move into 2021
While Executive Board support is expanding and cybersecurity budgets are generally increasing, the research has raised a red flag when it comes to executing the investment decisions we make. That’s because IT and security professionals admit only 50% of their cybersecurity technology investments get fully utilized.
There may be several reasons why our cybersecurity technology investments may not realize their full potential in protecting our organizations. Given the shortage in cybersecurity talent, companies may be frustrated in lacking the staff resources to fully implement solutions beyond their initial deployment. It could also be a sign that too many security technology solutions are still overly complex, or do not integrate well with legacy systems.
In any case, one of the key recommendations in the report emphasizes that a proper Proof of Concept (PoC) should be conducted before making any technology buying decision.
Here are the questions to ask when making your evaluation.
- How easy is it to deploy the solution?
- How intuitive is the User Interface?
- Do I have the skilled resources to operate and maintain?
- Will this require additional professional services? And at what cost?
- What are the underlying requirements or hidden costs?
- Does it work in my specific environment?
- Does it integrate with my existing solutions?
- What kind of support options are available with the solution?
- Can we try logging some support calls just to test the response?
- Will it make our day-to-day tasks easier and more efficient?
- Does it offer more value for future priorities and business plans?
- Will it adapt and scale as our business grows?
In the thick of budgeting season, now, IT Ops and cybersecurity teams would do well to read the survey report and reflect on their own evaluation processes. Sharing the experiences of our peers in this survey report will hopefully make us all better decision-makers.