Delinea endpoint privilege management product release enables even faster deployment
In recent years, CISOs have observed a transition from an office-based workforce to a remote one, accompanied by a growing number of identities that need to be managed due to continuous digitization.
More and more companies are maturing their PAM journey with endpoint privilege management solutions. Some adopt it willingly as part of their comprehensive security strategy, aiming to expand their vault and progress from phase 1 to phase 2 of the maturity model.

However, many customers also find themselves obliged to enhance endpoint security by insurers or auditors so they can qualify for cyber insurance or obtain certification.
Here is a simplified breakdown of the process:
Your systems face risks from ransomware and malware because: You have not eliminated local admin rights from the workstations.
And also: You lack auditing capabilities to generate regular reports.
As a result: Your cyber insurance may not be renewed, or you may fail the audit.
Because of various cyber insurance and regulatory requirements, we have many clients that need to adopt workstation privilege management solutions under tight deadlines.
Privilege Manager is Delinea’s workstation management solution that mitigates malware and modern security threats from exploiting applications by removing local administrative rights and enforcing least privilege on workstations. To speed up and ease the deployment process of Privilege Manager, we have developed a framework that will allow you to create your policies instantly.
So how does the Workstation Policy Framework work?
We have worked with numerous clients ranging from large to small organizations across a variety of industries and geographies to examine which policies are crucial to address the risks of malware and ransomware. As a result, we’ve created a list of the five most commonly used policies by our users which provide a simplified starting point for their endpoint privilege management journey.
In Privilege Manager, users can select one of the four types of policies: block, elevate, monitor, and allow.
When accessing the dashboard, users are presented with the option to select policies from the Workstation Policy Framework. There they can select from the following policies:
- Software Development Tools: This policy targets common software development processes and minimizes delays caused by these processes. This policy will also cause policy evaluation for child processes to be skipped.
- Visual Studio Installers: Silently elevates 4 Visual Studio installers.
- Malware Attack Protection: This policy prevents ‘Living off the land binaries’ from being executed by commonly exploited parent applications.
- Capture Application Elevation Attempts: The policy targets non-Microsoft applications that trigger a UAC prompt and sends policy feedback to the server.
- Allow Microsoft Signed Security Catalog: Allows Microsoft signed security catalog files to run. It can be used in combination with blocklist policies to prevent legitimate Operating Systems Applications from being blocked.
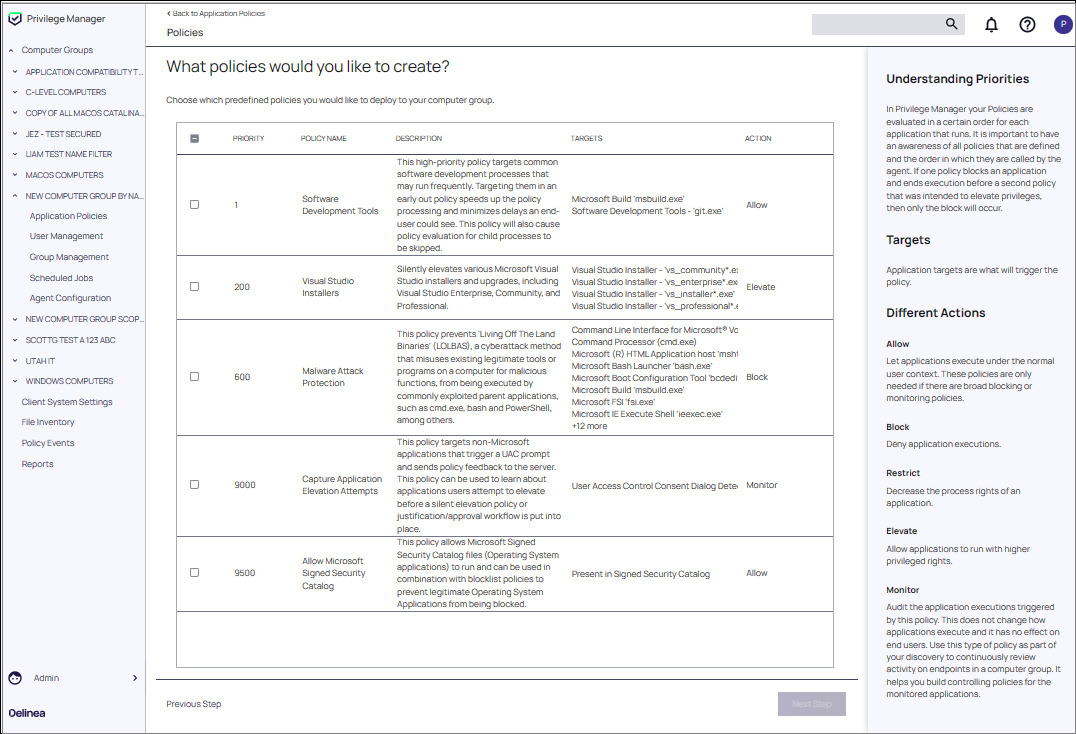
Screenshot of Privilege Manager's policy selection menu
This templated approach allows users to create their first policies and build a foundation for further policies focusing on local admin rights removal.
Endpoint privilege management solutions have become an essential part of cybersecurity strategy for many companies. By adopting these solutions, businesses are aiming to reduce the risk of ransomware, improve IT efficiency and obtain cyber insurance. However, many users find it difficult to deploy these solutions successfully. Our latest addition to Privilege Manager removes complexity and enables users to create and deploy their first policies with ease.
View Privilege Manager's features and sign up for a free trial.
Implementing Least Privilege shouldn't be hard


