Compliant user provisioning
Fastpath Access Provisioning
Automate compliant user provisioning for critical business applications to improve efficiency and reduce risk
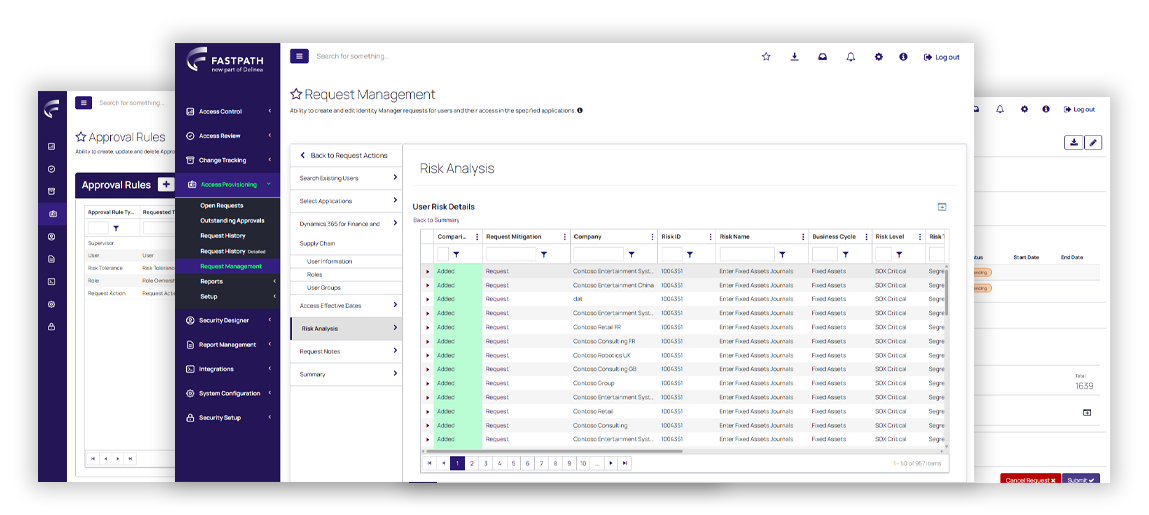
Ensure compliant access provisioning to minimize risk in critical business applications
Automate provisioning requests
Efficiently route access requests from business application owners directly to reviewers for approval, eliminating back-and-forth emails and IT intervention.
Proactively detect SoD risk
Analyze user access rights down to the lowest securable object using out-of-the-box or custom SoD rulesets to identify risks before access is granted.
Assign temporary access
For users requiring elevated privileges, automate provisioning for emergency access using scheduled start and stop times.
Define approval workflows
Create approval rules based on role ownership, risk level, or business policies, with support for multi-level management approvals.
Request access changes
Submit and schedule access requests for employee onboarding, role changes, or terminations, including time-bound temporary access.
Proactively prevent risk
Gain visibility into Segregation of Duties (SoD) and sensitive access risks before access is granted.
Automate provisioning
Reduce manual effort with automated provisioning and de-provisioning of access to critical business applications.
Validate changes
Ensure access removal with out-of-the-box reporting along with a full audit trail of changes and approvals.
Want to learn more about Fastpath Access Provisioning?
For more information about Fastpath Access Provisioning, including features, specifications, pricing, and availability, please fill out the form.

Request Information

Making Identity Work: Ensure a Successful Identity Project for Risk Management
Learn how a fast, easy-to-set-up solution can help build a strong identity and access risk management strategy in your organization.

Automating Your Control Environment: Get a Clear View of Access Risk Across Multiple Applications
