Privileged Access Management is Evolving to Extended PAM
Cyber risks and operational expectations are accelerating. But traditional PAM can’t keep up. Extended Privilege Access Management (XPM) is the only way forward.
XPM treats identity as the common thread for authentication and applies policy-based authorization controls to meet Zero Trust and least privilege best practices across your entire IT environment. Adaptive controls prevent bad actors from gaining access, moving laterally, and escalating privileges. Here we explain why enterprises are shifting to a new type of PAM.
Hi there, I’m Sam. My organization is facing 3 key challenges to protecting ourselves from security breaches. These may sound familiar to you.
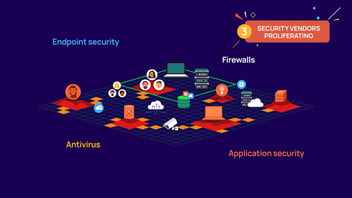
The first challenge is IT complexity: In the past, only admins had privileged access to sensitive systems and data. Now all users in my IT environment have some level of privilege. On top of that machine identities connect automatically. Without careful management our critical systems and data are vulnerable to unauthorized access, and our IT resources are spread over data centers and multiple cloud providers.
Second, because of this IT complexity and remote work styles, our threat landscape is expanding. Attackers are innovating, ransomware is spreading, and with automation comes more attack potential.
And third, there are so many vendors out there with a variety of technologies to solve part of my problem—but none take a holistic view of my entire environment. I see attacks increase globally and I worry our security solutions aren’t enough to protect us.
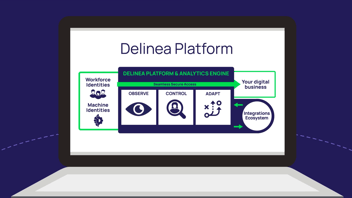
Delinea stood out because they have a different point of view. They believe identity is the common thread to these challenges, and their approach is Extended Privileged Access Management.
So, what is Extended PAM? Extended PAM starts with authentication to validate identities.
Then, policy-based authorization controls are applied across diverse IT environments to meet Zero Trust and least privilege best practices, reducing the attack surface across my entire enterprise.
DevOps, Cloud Infrastructure, Remote Work and SaaS become more secure with: Extended PAM. Extended PAM helps to prevent identity and credential theft by increasing visibility and discovery across all identities so that you can establish control over all privileged access to restrict lateral movement.
With analytics-informed policies, we can limit escalation by adapting access when and where it’s needed.
Delinea is the first vendor to extend PAM across the enterprise ensuring consistent authorization is applied to human and non-human identities. They secure secrets with an enterprise-grade vault, provide just‐in‐time and just‐enough privileges on workstations and servers, and secure credentials in code and service accounts
As a proven PAM leader backed by industry analysts, Delinea helps me protect my organization.
Privileged Access Management doesn’t have to be complex. Contact Delinea to learn how they can help you solve your evolving privileged access challenges.