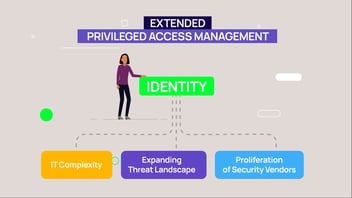
Delinea PAM Maturity Model Overview
See how to build a mature PAM program to safeguard all types of privileged identities and ensure adoption throughout your enterprise. Save time planning with a step-by-step roadmap for security controls and governance processes to help you achieve each stage of PAM maturity as your organization grows and cyber threats evolve.
Protecting my organization from identity-based attacks isn't optional.
It's imperative.
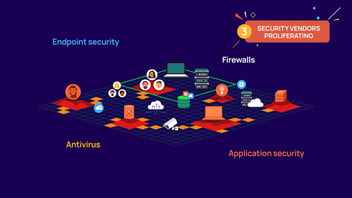
With a diverse environment and an explosion of identities and privileged accounts, we've got multiple
strategies to reduce risk, but we didn't start that way.
It's been a journey.
Initially, we thought storing passwords and credentials in a vault would be enough to prevent unwanted access, but we soon realized people had more access than needed, and we couldn't track what they did with that access.
That's when we turned to Delinea.
They helped us implement privileged access management.
We built a roadmap to reduce risk in phases, so we could see results right away and increase our maturity to meet best practices.
Thousands of Delinea customers have used this maturity model.
It's saved me tons of time!
It equipped me with the business justifications for investment and helped me plan and align with the rest of the executive team.
In each phase, our team adopted PAM policies, processes, and solutions to help us with governance, risk, and compliance, privilege administration, and identity and access management.
First, we set the foundation.
We discovered all our privileged accounts to see which were excessive, unused, or expired, and vaulted the necessary ones.
We limited privileges to reduce our attack surface, starting with domain admins.
Then, we expanded policies to more types of privileged users, business users, developers,
Linux teams, and service accounts.
We layered defenses, so now permissions are required not just for initial access but also for privilege elevation.
We integrated identities and made sure policies were consistent for easier management.
With that experience, we've now automated our policies and made them more intelligent.
Today, we catch suspicious behavior before it does any damage, and reporting and auditing are a snap.
Delinea met us exactly where we stood in our PAM journey and gave us the resources and advice to take us forward.
Plan your path to privileged access management maturity with Delinea.