Privileged Remote Access
Provide privileged users with browser-based, VPN-less secure remote access, delivered on the cloud-native Delinea Platform.
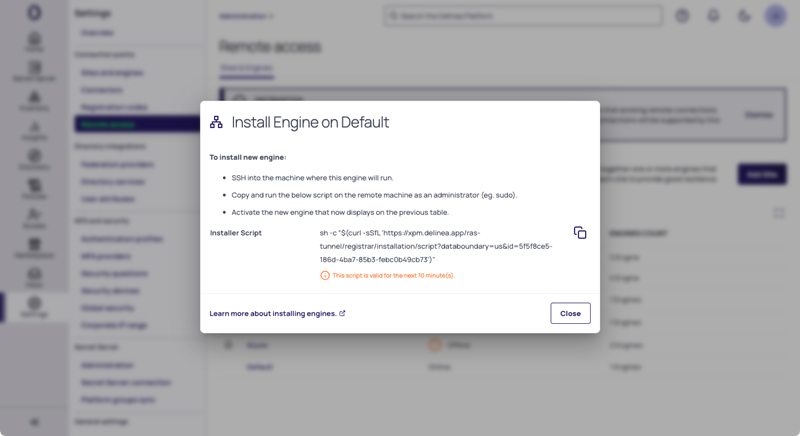

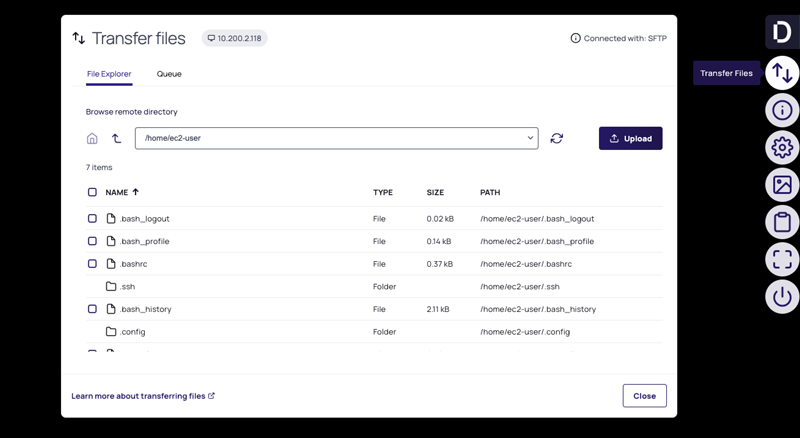
When remote admins, contractors, and vendors connect from anywhere over VPNs, jump servers, and shared accounts, it’s hard to verify identities or enforce least privilege access. Lack of monitoring enables lateral movement, invites credential theft, and leads to failed audits.
Delinea delivers Remote Privileged Access Management (RPAM) through a browser-based, VPN-less RDP and SSH solution, connecting users to critical internal resources without network exposure. Sign in, start a secure session, and get immediate access without seeing a credential. Each session is time-bound and enforces least privilege. Admins have full visibility, and Auditing powered by Delinea Iris AI turns all activity into a clear, reliable audit trail for compliance and fast remediation.

Policy-based controls provide remote users seamless access to resources via their browsers.
Stop exposing credentials to potential theft by injecting them directly from your vault into remote sessions.
Key Features & Capabilities
Centralize remote access policies
Prevent lateral movement
Implement multi-factor authentication (MFA) at depth
Speed audit and compliance
Increase user productivity

Related Demos
Privileged Remote Access
What's trending in identity security
Privileged Remote Access enhances the way security leaders manage remote access. It's a seamless solution that eliminates the need for traditional VPNs.
Read the blog
Jeff Carpenter explains the limitations of traditional VPN technology and introduces a more secure and fine-grained alternative for remote access: Delinea's Privileged Remote Access (PRA).
Watch the video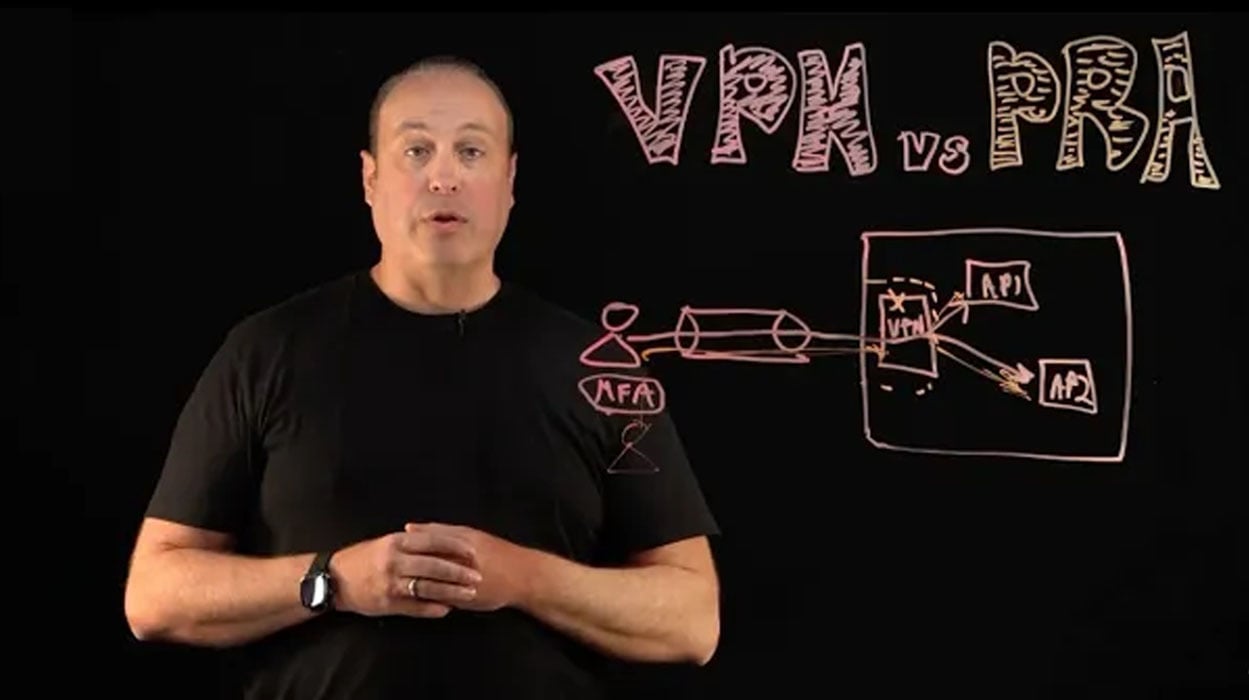
Our eBook, Remote Access Granted: How to secure access to critical data and resources, explores how Remote Privileged Access Management (RPAM) redefines secure access for today's hybrid work environments.
Download the eBook