Delinea Identity Services: Securing Docker and Containers
We are excited to announce that Delinea (formerly ThycoticCentrify)now supports CoreOS Container Optimized Linux which several of our customers are using as part of their adoption of containerization for their application deployments. But first, let’s start with an overview of how Delinea can help you protect access to these containerized platforms and the applications that run on them.
As organizations embrace hybrid cloud environments moving their applications and other workloads to public clouds such as AWS, Azure, and Google, application developers building custom apps inevitably rework their applications to take advantage of the hosting platform capabilities such as auto-scaling enabling elasticity and scalability. This move typically means transforming the app to a microservices architecture via containerizing applications to achieve the flexibility necessary to enable the desired capability the business requires.
As app developers make this transition to containerized applications, the operations team needs to ensure that they can both enforce the required security for these applications as well as to support the operation of the application in production. This is where identity, access, and privilege management come in. Delinea has been working with several of our largest customers to secure both their containerized applications and the hosts they run on. And many of these deployments will have either an orchestration system or container management platform to manage the containers which also needs to be secured for appropriate DevOps staff access.
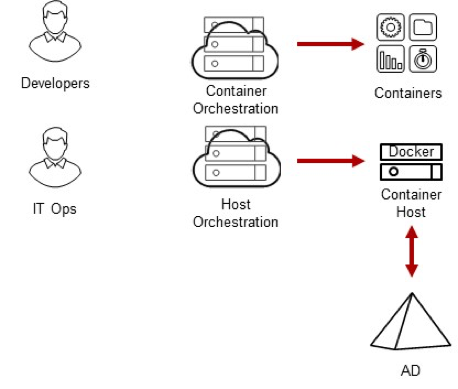
Privilege Management for Container Hosts
We start by securing the container host, which typically runs Docker in order to ensure the platform on which the containers run is secured and you are able to centrally manage user access rights and privileges. Privilege management is essential for ensuring IT Staff and Developers that manage different sets of containers do not compromise the security of the host or the containerized applications of other teams.
- Delinea Infrastructure Services provides identity, access, and privilege management for Linux docker host or CoreOS container Linux in order to enable IT staff and DevOps the ability to login to these hosts even if they are automatically managed and ephemeral. Login rights, MFA policies, privileges, and session audit policies are all centrally managed and enforced locally.
- For Docker specifically, Delinea Infrastructure Services enable centralized management of the Docker group and the users who are a member of the group which enables execution of docker commands.
- If you would rather provide granular privileges to execute specific Docker commands, then you should not put users into the Docker group, instead, use Delinea privilege elevation service to control which users can execute specific Docker commands on individual or groups of Docker hosts.
- Additionally, it is a best practice to apply access and privilege policies across logical groups of Docker hosts leveraging Delinea zones to segregate applications or projects and the DevOps staff who need to access them.
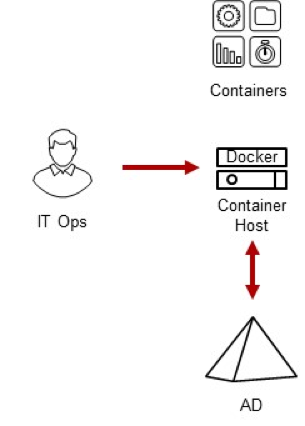
IAM and AAPM for Containers
Many applications that run within containers may need PAM or NSS services to access or authenticate an account for networked access to other services or containers and in some cases, you may also need Kerberos services for stronger authentication than passwords or static keys for these accounts. Delinea provides security services to run within the containers running applications on these hosts providing both identity and access management (IAM) as well as application account and credential management.
One use case is to enable developers to log in directly to the containers that Operations creates for them to enable them to manage and troubleshoot their application. All you have to do is to install OpenSSH along with Delinea and your application.
Another use case is to provide application or service account services to support one containerized application to authenticate or login to another service or containerized application on the network. This can be done by either a) creating an account in the container of a server application and vaulting its password so that clients can check it out and log in, or b) creating a network account within AD and then leveraging Kerberos to support network logins to other Active Directory integrated services.
- Delinea provides Identity Broker Services to support PAM and NSS calls within a Container for both Active Directory user accounts and groups as well as for any User the Delinea Identity Platform is authorized to authenticate.
- Additionally, Delinea provides GSSAPI to support Kerberos authentication for Applications that need to support either Active Directory integrated authentication for AD users or for a Service account to be able to access other Active Directory integrated resources on the network.
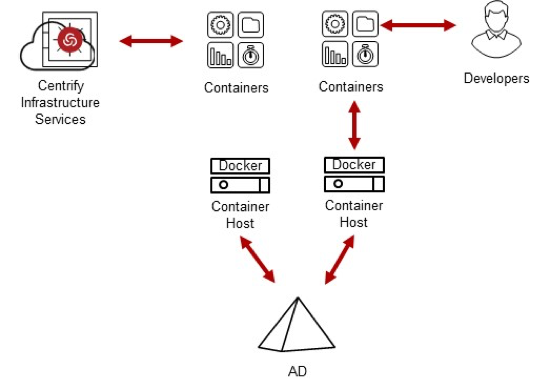
- Containers can be configured to either Join Active Directory to get their own Identity via a Computer Account or they can leverage the host’s account and relationship to AD.
- Additionally, Delinea can join a container directly to Active Directory or enroll for Delinea’s cloud-based Identity Broker Services for an individual account for each container with its own individual access controls. The benefit of this model is that it enables Developers to directly log into their Containers without having to grant them any permissions on the Host, especially important in new deployment models such as AWS Fargate.
- Delinea also provides application password management services to support vaulting of an account’s password as well as check out to support password-based Containerized App authentication between services.
- Once joined to Delinea’s Identity platform, directory-based applications accounts can be used by the containerized application leveraging SAML or OAuth to access other network resources.
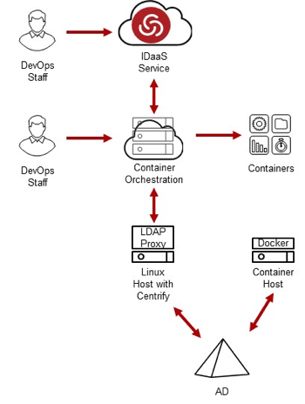
IAM for Container Orchestration Platforms
Most organizations adopting Containers to manage their applications will be using a container orchestration system such as Kubernetes or CoreOS Tectonic. While these orchestration platforms support creating a local account for DevOps staff login, it is always a best practice to integrate these kinds of administrative platforms into your enterprise authentication system. This can be done easily by leveraging either LDAP for integration to Active Directory via Delinea LDAP Proxy to enable multi-domain support or you can leverage SAML or OAuth to support federated login from your enterprise user accounts. Both models are shown below:
Summary
Delinea is working with several of our customers to ensure that they have control over both access and privileges across the Containerized ecosystem as well as providing IAM services for app developers building applications to run within Containers. You can get started by installing Delinea Infrastructure Services on your Docker Hosts running Linux or CoreOS, and if you are running on AWS check out our Tech Center.

Identify and mitigate risks of privilege escalation on Windows and Linux endpoints


