SAMA Cybersecurity Framework: Improving cyber resilience
According to Gartner, cybersecurity is one of the top risks for businesses in the Middle East. Within that region, Saudi Arabia is one of the most highly-targeted countries for cyber-attacks based on its geopolitical stands, its widespread adoption of digital practices, its vast natural resource reserves, and its accumulation of wealth.
Thus, it’s not surprising that a recently published KPMG CEO Outlook survey saw 20% of the CEOs in Saudi Arabia reach a consensus that cybersecurity risks are the biggest threats to their businesses today. In 2018, the same survey ranked cybersecurity risks at sixth position with only 4% of the surveyed CEOs believing it to be a top risk at the time.
SAMA Cybersecurity Framework
To improve cyber resilience, a variety of Saudi Arabian government entities and oversight agencies created mandatory guidelines to strengthen their constituents’ security postures and provide prescriptive measures to defend against today’s cyber threats. For example, the Saudi Arabian Monetary Authority (SAMA) introduced the SAMA Cyber Security Framework, which encompasses best practices from a variety of other government frameworks and industry standards ranging from the National Institute of Standards and Technology Framework for Improving Critical Infrastructure Cybersecurity (NIST CSF), Payment Card Industry Data Security Standard (PCI DSS), and ISO 27001/27002 Information Security Management Standards to Basel II International Convergence of Capital Measurement and Capital Standards.
SAMA avoided the typical pitfall of many other cybersecurity frameworks. Instead of asking banking, insurance, and financial services companies to voluntarily adopt the best practices, it mandated the implementation of the framework to assure the sector can manage and withstand cybersecurity threats.
Overall, the SAMA Cyber Security Framework is very comprehensive and prescriptive by nature, propagating key cybersecurity principles and objectives to be embedded and achieved by each regulated entity. These are broken down in terms of four main cybersecurity ‘domains’: Leadership and Governance, Risk Management and Compliance, Operations and Technology, as well as Third-Party considerations.
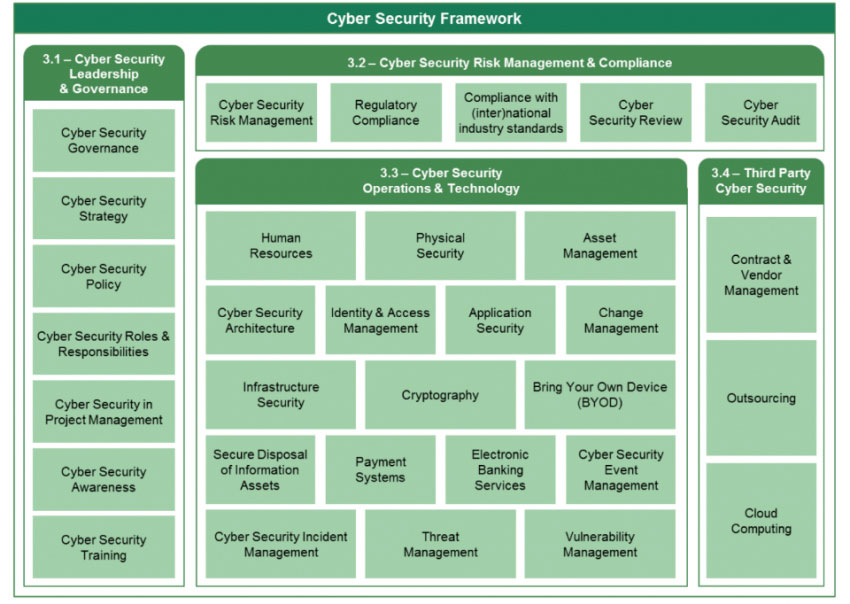
Figure 1: SAMA Cyber Security Framework Structure
Considering that 80% of today’s data breaches involve compromised privileged credentials, according to Forrester, it is refreshing to see that in section 3.3 (Cyber Security Operations and Technology) SAMA provides detailed directives on Identity and Access Management (IAM). Unfortunately, many other industry standards and cybersecurity frameworks fall short when it comes to establishing best practices to protect against credential-based attacks, which is today’s #1 attack vector.
SAMA alignment to best practices
SAMA’s guidance for IAM measures aligns closely with Delinea Privileged Access Management (PAM) best practices:
- Discover and Vault Shared Accounts
Identify all privileged accounts and resources and vault away those privileged credentials so that they are properly managed. Organizations can leverage a Privileged Access Management Solution to establish the core privileged access controls across your growing attack surface.
- Identity Consolidation
Vaulting alone is not enough. Following Zero Trust principles, it is important to establish an identity for users via HR-vetted enterprise directory identities like Active Directory, meaning these identities are automatically disabled when the person’s employment is terminated. Instead of logging into a server with a shared account, superusers would leverage their individual identity to authenticate to the system.
In this scenario, organizations are using temporary tokens rather than static passwords for the authentication process. By doing so, they’re not imposing any behavioral changes by forcing users to log into a vault, and then checking out a password, which often leads to admin users circumventing the approach by for example creating an SSH backdoor key. Password checkouts should only occur in break-glass scenarios – the rest of the time, users should leverage their individual credentials to establish accountability. Authentication Service provides organizations with the needed capabilities to go beyond a password vault and reduce their attack surface by consolidating identities and eliminating local accounts as much as possible.
- Enforce Just-Enough, Just-in-Time Privilege
Least privilege means granting just enough privilege, just-in-time, as well as limiting lateral movement. Just enough privilege to get the job done. Just-in-time privilege based on temporary access through a simple request process and limiting lateral movement by only granting access to the target resources needed to get the job done and no more. Privilege Elevation Service empowers organizations to implement privilege elevation controls as well as workflow for just-in-time privilege access.
- Audit Everything
With a documented record of all actions performed, audit logs not only can be used in forensic analysis to find exactly the issue but also to attribute actions taken to a specific user. Because these sessions are so critical it is also best practice to keep a video recording of the session that can be reviewed or used as evidence for your most critical assets or in highly regulated industries. Compliance and Audit Solution allows customers to fulfill their compliance mandates through auditing and reporting as well as shut down any dangerous workarounds by putting host-based monitoring in place.
- MFA at depth
Both SAMA and Delinea believe that one of the lowest-hanging fruits when it comes to deterring a threat actor is to implement multi-factor authentication (MFA) for all privileged users, everywhere. Modern PAM solutions allow organizations to establish this additional security layer not only at vault check out, but also for server login, privilege elevation, etc.
IT security should be easy. We'll show you how


