Simplifying PEDM with endpoint privilege management
Cyberattackers have breached your IT infrastructure. They've exfiltrated sensitive data and encrypted it in a double-extortion ransomware attack.
How did they pull this off? What more could you have done to prevent it?
Is the front door of your house locked?
To better understand how cyberattackers launch successful ransomware attacks, let's begin by looking along the attack chain at tactics, techniques, and procedures (TTPs) used in a typical ransomware attack playbook.
From initial inception to the end game, attackers exploit weaknesses—including human fallibility, a large attack surface, standing privileges, a wealth of attack vectors, and poor security hygiene.
There are several places where Privilege Elevation and Delegation Management (PEDM) can prevent, detect, or contain an incident to avoid it turning into a breach. However, a band-aid approach to Privileged Access Management (PAM) won't work. Every step of the attack chain needs attention. For this blog, we will focus on the initial entry phase.
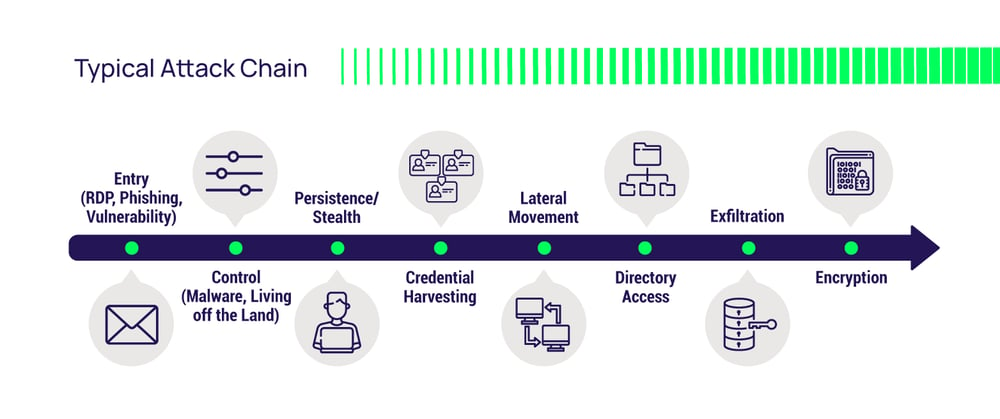 The ransomware attack chain begins with the leftmost point in the chain, the "front door," where cyberattackers obtain their initial foothold. From this base camp, attackers can burrow deep into your networks and systems, jeopardizing your business.
The ransomware attack chain begins with the leftmost point in the chain, the "front door," where cyberattackers obtain their initial foothold. From this base camp, attackers can burrow deep into your networks and systems, jeopardizing your business.
Your employee workstations and local accounts represent the largest portion of the attack surface at this entrance point. The SANS institute tells us that 85% of reported cyberattacks start with a compromised endpoint. Despite the pandemic and travel reduction, lost and stolen laptops contribute to this expanded attack surface.
User workstations blanket your infrastructure, providing multiple inroads. Having an extensive supply chain, outsourced services, or third-party contractors with VPN access to your systems further increases the number of entryways into your IT systems. We use VPNs to access apps and servers remotely. Developers use APIs and CLIs to access hosted instances that run our business apps and store critical data. Threat actors constantly exploit these glaring weaknesses with a remote workforce and home Wi-Fi networks less secure than the office LAN.
As users, we are custodians of these ingress points and the weakest link. We must train users to spot social engineering, like phishing attacks. Even with effective security awareness training, we can't be vigilant all the time. So, it is essential to train users to avoid clicking a phishing link and augment this with training around reporting when we accidentally click the link. Be careful to foster a supportive environment that encourages rapid reporting when we inevitably make mistakes, not an atmosphere of shame and retribution.
MVP endpoint PAM capabilities
So, what can we do at the workstation level to prevent, detect, and contain attacks that get past our initial defenses?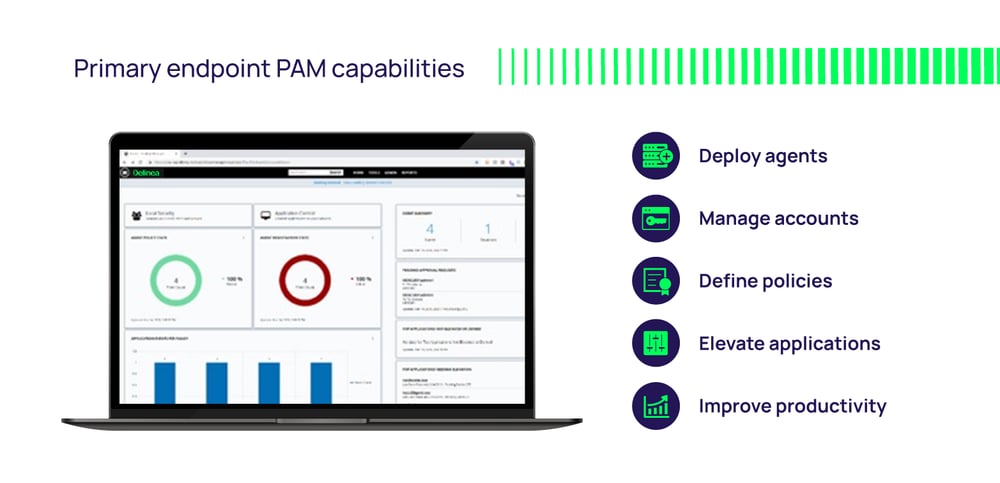 The graphic above highlights what's necessary. Let's spend the rest of this blog reviewing these endpoint PAM capabilities.
The graphic above highlights what's necessary. Let's spend the rest of this blog reviewing these endpoint PAM capabilities.
Manage and vault local administrator accounts
With endpoint PAM, discover local accounts, applications, and processes tied to privileged accounts on workstations joined to a Windows domain or standalone. This is the foundation for building access control policies and enforcing least privilege.
Attackers prioritize account takeover (ATO) to own user workstations. Phishing a regular workstation user account gets a foot in the door, but if the user is logged in as a local admin, the attacker hits pay dirt, inheriting full rights. Make sure to take local privileged accounts out of regular circulation by vaulting them for emergency access only.
Enable scheduled password rotation and strong quality of service to improve resistance to brute-force cracking. Ensure common privileged accounts on workstations, such as local "administrator," have unique passwords. This prevents an attacker from using a compromised password to access other systems.
Recommendation: Look for an endpoint PEDM solution that is standalone. That is, it has all these capabilities built-in, so you don't need a separate, dedicated vault. If later you need more comprehensive and robust vaulting, ensure your endpoint PAM vendor can provide it and that the two products integrate effectively.
JIT workflows
With privileged accounts vaulted, users log in with minimum rights. PAM policies can allow the execution of applications on-demand or require the user to submit a rationale for workflow-based approval. If granted, the application runs with elevated privileges once or multiple times within a custom time window that expires to avoid standing privileges. We mitigate risk since PAM elevates privileges on the application, not the user session. PAM automatically revokes rights when the app quits.
Recommendation: The PEDM solution must support Just-in-Time (JIT) elevation of privilege. Look for elevation policies that can replace the native Microsoft User Account Control (UAC) authentication popup with an alternative custom action, such as asking for justification, requiring approval via workflow, and allowing a help desk admin to enter privileged credentials during a support session.
Managing privileged group membership
Membership of custom or built-in privileged groups like local or domain administrators gives users standing elevated privileges. A threat actor that succeeds in an account takeover (ATO) will also inherit those privileges, giving them an advantage.
Recommendation: Look for a PEDM solution that can remove excess privileges and automatically control members of any local group. If unapproved additions or removals occur, the PAM solution must auto-correct to ensure realignment with policy. Policies must be centrally managed and automatically enforced on every endpoint, thus avoiding security gaps and manual administrative overhead.
Deployment options
Organizations are transforming their business, with IT infrastructure co-existing on-premise and in the cloud.
Recommendation: A modern workstation PEDM solution should offer customers the choice of SaaS or self-managed deployment options. It must support identical capabilities to ensure parity for organizations using both or migrating from one to the other.
Ransomware protection
Ransomware is central to our discussion, so let's take a closer look. Common tactics, techniques, and procedures (TTPs) for ransomware include privilege escalation, downloading tools, moving laterally between machines, and encrypting or destroying data on the disk. PAM can be an effective roadblock by preventing ransomware's ability to escalate and confining it to the machine it's on.
Common tactics, techniques, and procedures (TTPs) for ransomware include privilege escalation, downloading tools, moving laterally between machines, and encrypting or destroying data on the disk. PAM can be an effective roadblock by preventing ransomware's ability to escalate and confining it to the machine it's on.
Recommendation: Ensure your PEDM solution supports the following capabilities:
![]()
Least privilege enforcement
If ransomware can only execute with the rights of a low-privilege user account, this prevents:
- Exploiting local privileged tools ("living off the land") to camouflage malicious activity.
- Common persistence mechanisms being used to maintain a persistent foothold, like services, scheduled tasks, and registry run keys.
- Deletion of Volume Shadow Service copies (snapshots of the disk for backup) before triggering the encryption process.
- Disabling local security software (such as AV, EDR, and firewall).
- Downtime, since ransomware can't tamper with operating system files and installed software.
- Exploiting password hashes thanks to help desk admins not having to log in with privileged accounts.
![]()
Authorized applications
Ensures that only authorized applications can execute, blocking everything else, including ransomware-specific tools.
![]()
Reputation scoring
During a ransomware attack, we may encounter unknown applications lacking an associated PAM policy. Policy integration with third-party malicious code sample databases such as Cylance and VirusTotal allows PAM to incorporate reputation scores into its policy engine, automatically blocking execution in real time.
![]()
Drive-by malicious office documents and file access control
It's a common tactic for malware to run other privileged applications or child processes. For example, an Excel or Word doc could contain malicious code that attempts to spawn a CMD or PowerShell command. Block ransomware by controlling which apps can access specific files, thus preventing malware from deleting or encrypting them. For example, only permit excel.exe to access .xls files and word.exe to access .docx files.
![]()
Catch-all policy
A policy that catches anything not explicitly covered by an allow, elevate privilege, or deny policy—for example, new ransomware not in PAM policies or in the 3rd-party reputation database.
That brings me to the end of this blog. I hope you gained valuable insight that helps you better understand and appreciate the importance of protecting workstations with PEDM.
For more information about our workstation PEDM solution, please view our Privilege Manager.

How many risky applications are running on your high-risk endpoints?


