Any time you want to make a purchase, post a comment in a forum, or even read content on many websites, you’re prompted to create (and remember!) a password.
But what’s really going on when you create a password? And how does this process help keep your information safe? When you create a password on a website, that password isn’t stored verbatim on the website’s server. That’s because your password would be freely available if the security of the server were compromised.
Instead, your password is put through a process called “hashing,” which significantly improves security (provided your password is strong enough).
How does password hashing work?
Password hashing turns your password (or any other piece of data) into a short string of letters and/or numbers using an encryption algorithm. If a website is hacked, password hashing helps prevent cybercriminals from getting access to your passwords. Instead, they just get access to the encrypted unintelligible “hash” created by your password.
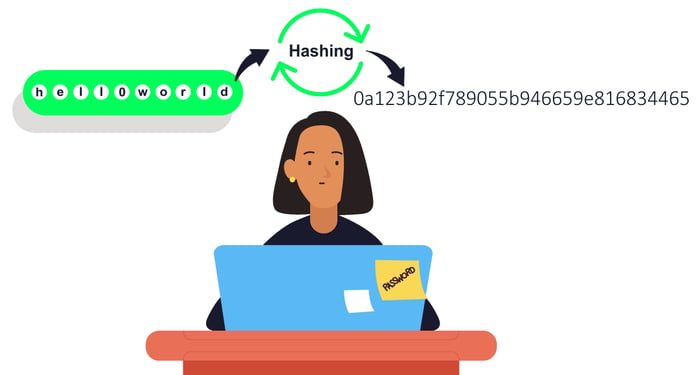
A common hash function is md5(), which returns a 32-character string from any input. Below are a few examples of what a hash looks like:
- md5(helloworld) = fc5e038d38a57032085441e7fe7010b0
- md5(hell0world) = 0a123b92f789055b946659e816834465
- md5(g84js;l238fl-242ldfsosd98234) = 42e7862f4ad5225471866d2023fc4cca#
- md5(helloworld) = fc5e038d38a57032085441e7fe7010b0
From these examples, we can learn several things about hashes:
Small changes matter a lot – Take a look at examples 1 and 2. Just one digit has been shifted, from an “o” to a “0.” This is a very small change, and yet the second output is unrecognizable from the first.
The output length never changes – The input in example 3 is considerably longer than the other examples, yet it produces an output of the same length (32 characters). You could input an entire book into the md5() hash function and you would still get a 32-character string as the output.
Repeatable – An input will always give the same output when hashed using the same function. If this weren’t the case, they would just be generating a random output, which would be useless for passwords. (I included the same function in example 1 as example 4 just to see if you were paying attention.)
Hard to reverse – Even though a cybercriminal may be able to tell the function used to create a hash, it’s almost impossible to reverse that function and generate the password. In fact, it’s so hard that trying millions of combinations to try and produce the same end result (a brute-force attack) is typically quicker than the calculations required to reverse the hashing process.
How is password hashing used for granting access?
Let’s look at how password hashing works in practice:
- Step 1 – A user visits a site and fills in a form to create their username and password.
- Step 2 – That password is put through a hash function and the hash is stored in the database.
- Step 3 – When a user logs in they enter their password again on the site.
- Step 4 – That entered password is run through the same hashing function as was used before.
- Step 5 – The server checks this hash against the one stored for the user in the database.
- Step 6 – If the two hashes match exactly, the user is granted access.
Is hashing sufficient to keep passwords safe?
Knowing that hashes are the same length regardless of the password you choose, you might be tempted to pick a short, memorable password. In fact, you should do the opposite. The password you choose is critical for keeping your data secure.
Once a cybercriminal obtains password hashes from a website, the real process of password hacking begins. This process happens offline, on the cybercriminal’s computer. Cybercriminals put combinations of characters into a hashing function until a hash that matches yours is created.
Because the functions themselves are well known, password cybercriminals can easily calculate hashes for known words and other commonly chosen combinations. Then they match the cracked passwords against these dictionaries.
These dictionaries go far beyond simple words. They include prefixes, suffixes, the practice of changing letters for numbers (e.g. 1 instead of l), and much more. This means weak passwords can be broken very quickly.
You can see how easily simple passwords can be cracked in the blog, Five Most Popular Password Cracking Tools.
For strong password security, you must:
- Create a long and seemingly random password
- Change that password periodically
- Never reuse that password on other websites
Check your password habits against our 20 password management best practices.
Password management and PAM
Human beings struggle to create strong, memorable passwords. When we fail to do so, we put our financial and personal data at risk.
For businesses, the risk is even greater. Even if your network security is strong, if people are using the same passwords for your multiple internal systems, applications, and websites, your network could be breached without anyone hacking in. For example, if a user’s personal email is breached, a cybercriminal might try the same password on their work account, possibly gaining access to sensitive business data.
Privileged Access Management (PAM) solutions automatically generate complex passwords and rotate them regularly. So, even if a cybercriminal gains access to a hash, they can’t easily conduct a brute-force attack. PAM solutions help ensure passwords are unique and never shared, so even if cybercriminals get one password, they are less likely to leverage that password to gain additional access.
With PAM, privileged users don’t need to remember passwords or remember to change them. Your enterprise password management happens automatically, behind the scenes, without interrupting a user’s productivity.
So, that’s how passwords work! Now, learn more about privileged access management.
Related Reading: Why you must NOT store enterprise passwords in Excel.