Passwords. They’ve been around for so many years and yet there’s still so much to be said about passwords and how they're evolving.
In most organizations, passwords are what make the difference between keeping cybercriminals out—and falling victim to a cyberattack. And for the multitude of applications, systems, and infrastructure of so many organizations, the only security control preventing unauthorized access is a simple password somewhere between 4 and 127 characters long.
A password—sometimes called a passcode, passphrase, PIN, or Secret—is used to ensure that only authorized employees or users can access applications and systems. A password is usually combined with an identifier (typically a username or email address) to determine who is accessing the system, to verify the authenticity of that identity. A password should be known only to the user, and never shared. For other password security guidelines, check your password habits against our 20 password management best practices.
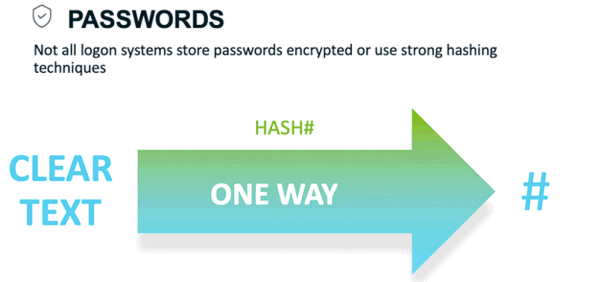
Ordinarily, a password is a set of character combinations such as letters, numbers, and symbols used to authenticate an identity or to verify authorization to access a system or application. But not all login systems enforce the same security best practices. Different authentication systems require different lengths and complexities of password strings, and this presents a challenge. Some systems have set limits on password length, some have set limits on complexity, and some systems even require all lowercase characters.
Another popular login method is the PIN. This typically refers to a number-only password, usually 4 to 6 numbers, and is commonly used on mobile devices. As a best practice, you should know the limitations on login systems so you can ensure the highest possible security is configured and used. And make sure your security solution is usable and not too complex or users will revert to poor password hygiene habits, like reusing passwords across multiple systems and credentials.
So, how do cybercriminals crack your password to gain access to applications and systems?
The majority of cybercriminals will want to use the easiest, stealthiest, and least costly way of stealing your passwords. And one of the easiest methods is phishing—they simply ask you for the password. This technique takes advantage of your trusting nature, and when directed to a fake login website (that looks perfectly authentic) you hand over your username and password to the attacker as you log in. Here are some of the most common techniques for getting passwords:
- Ask the user for their password pretending to be an authentic internet service
- Crack the password using brute-force or dictionary attacks
- Discover a vulnerability in the application, bypassing authentication
Let’s take a closer look at password-cracking techniques:
Before a cybercriminal can get to work on your password, they must first get the hash, which as previously mentioned is the cryptographic store value of your password. There are tools available to get those hashes:
- Mimikatz – a Password Recovery and Audit tool
- Capture Packets – tools such as Wireshark to capture the packets that move around the network
- Metasploit Framework – a security framework that helps security professionals assess and manage security
- Responder – LLMNR and NBT-NS (NetBIOS Name Service) responder
This is what a typical password-cracking flow looks like:
- Steal/Get the hashes
- Organize and format the hashes depending on the tool
- Plan your attack method: wordlist, rules, and masks
- Crack the passwords
- Analyze password’s progress
- Customize your attack
- Repeat
Popular Password Cracking Tools
Kali Linux – Popular Penetration Testing Distribution Tool
Kali Linux is a well-known security tool and it comes in many different bootable options from virtual images to software installations. It even runs on Raspberry Pis. It’s used around the world for penetration testing and by IT security teams protecting their networks or looking for vulnerabilities on their networks. Kali comes with a variety of popular password attack tools out of the box:
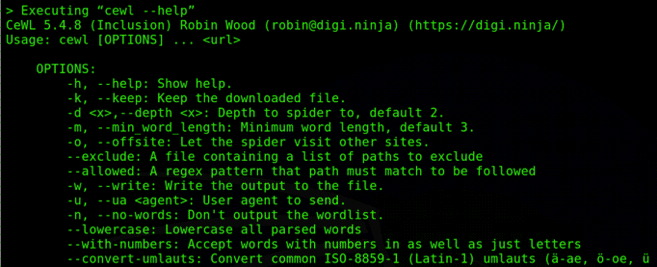
CeWL – Custom WordList Generator
CeWL is one of my favorite wordlist generators. It allows you to create word lists by spidering websites.
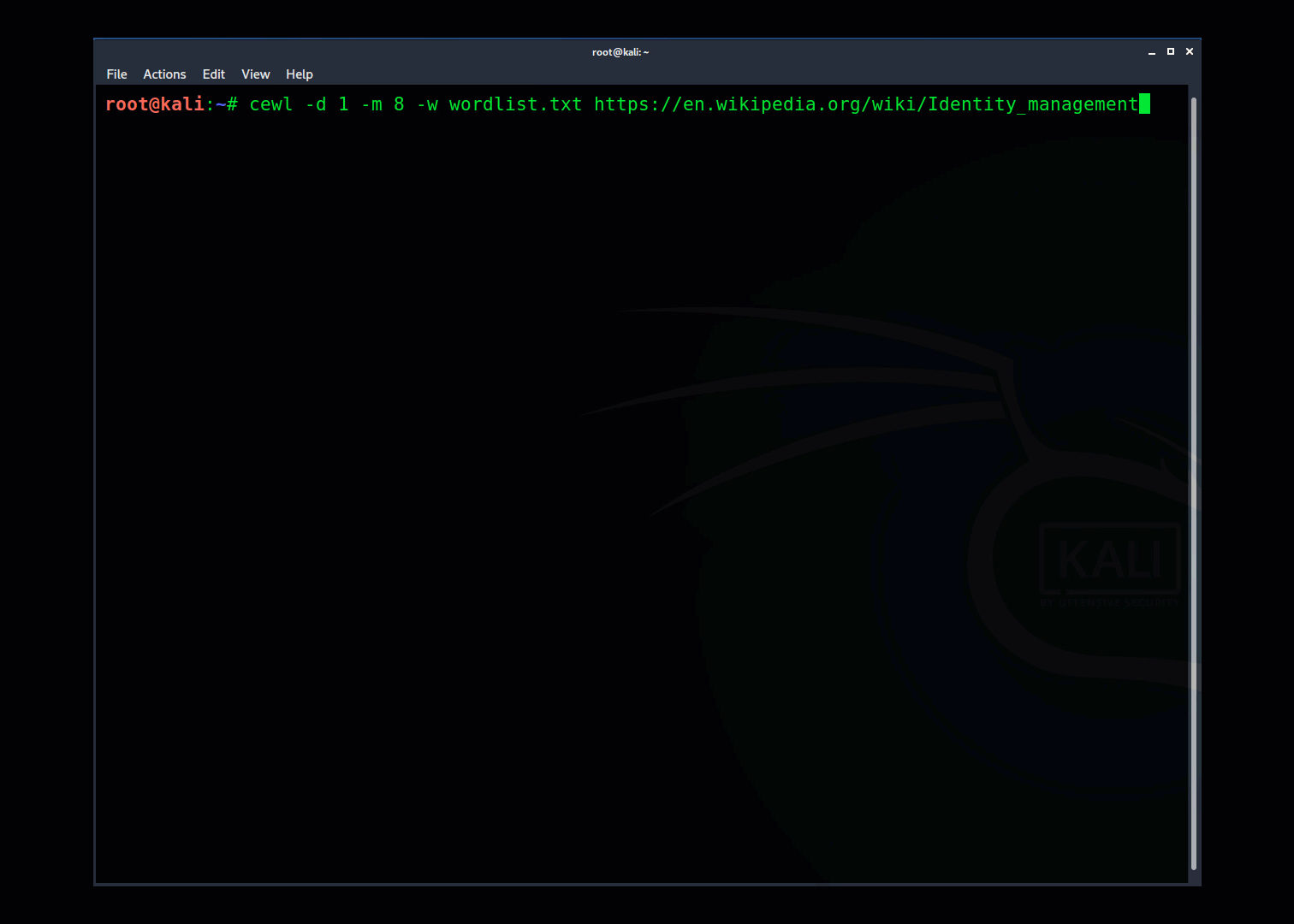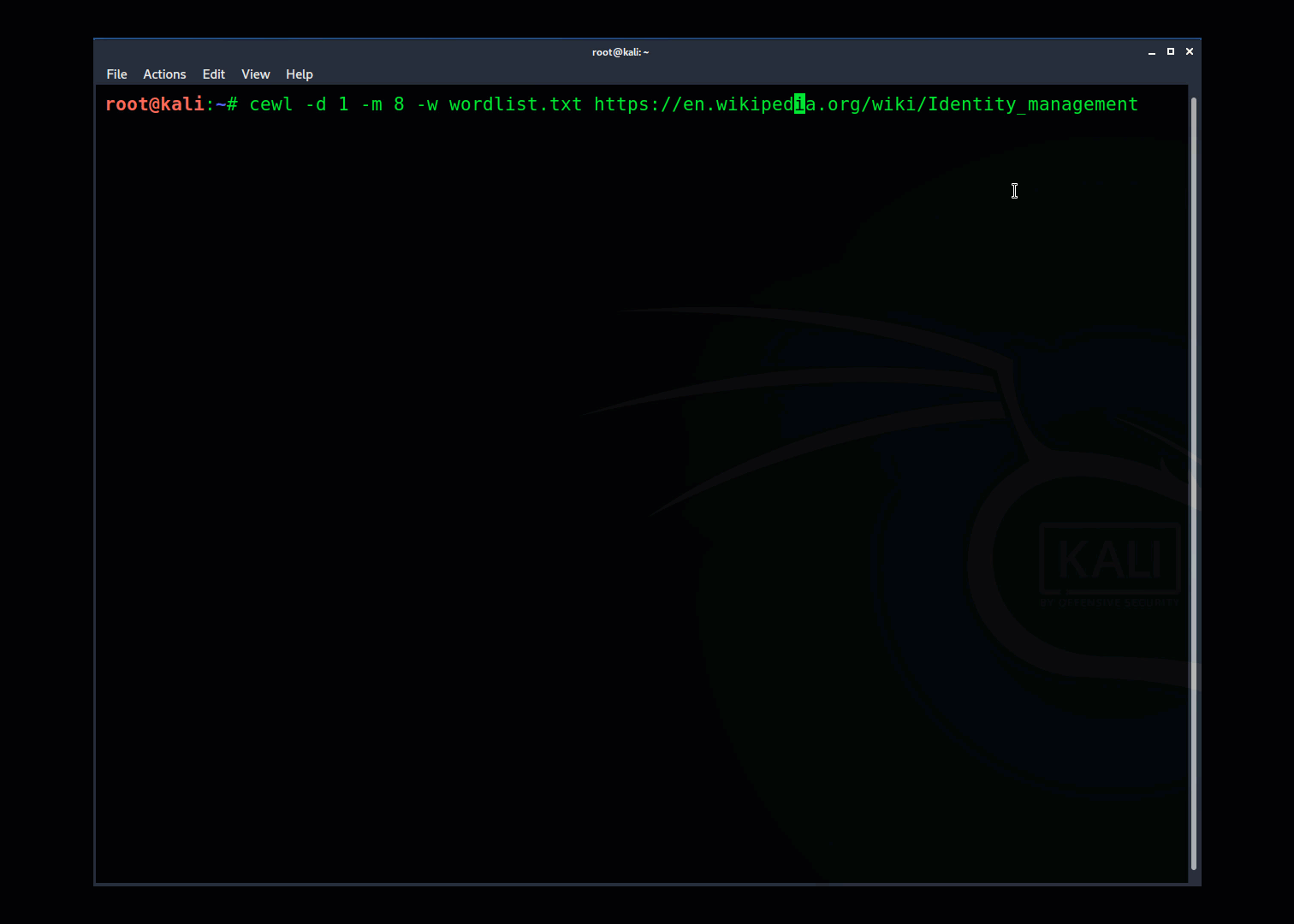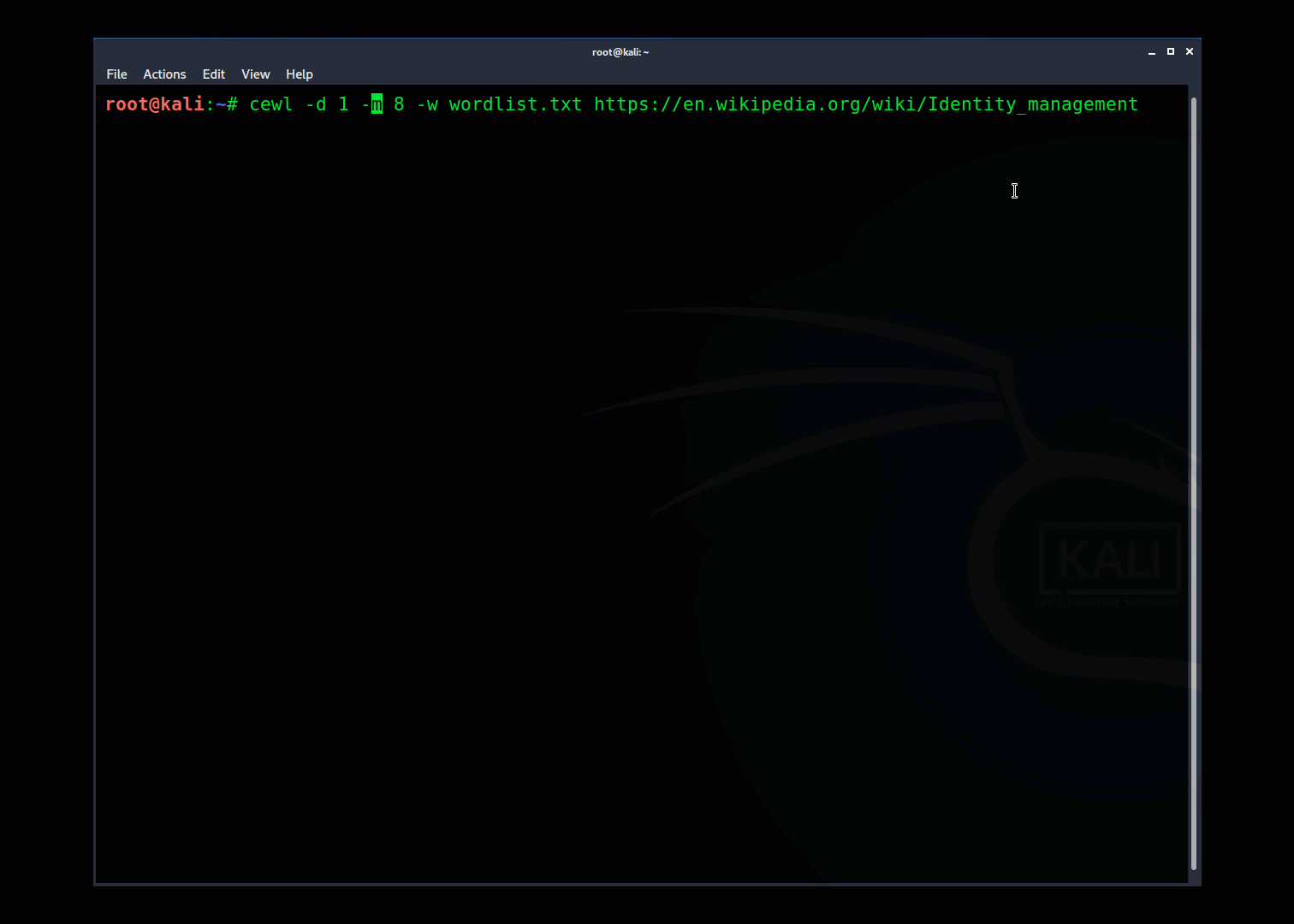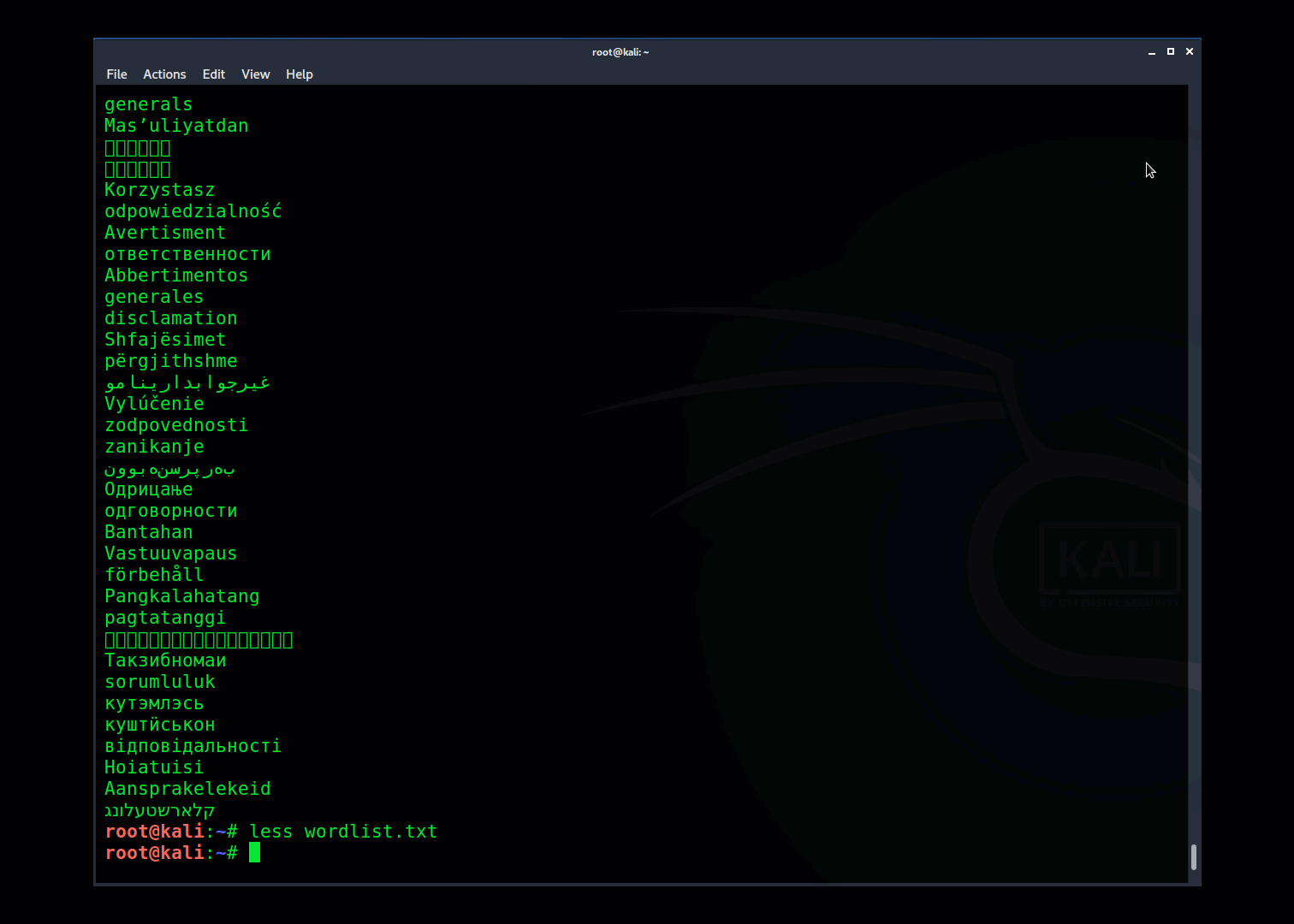
When using CeWL I start with a basic command like this:
The command-line options are:
-h = help
-d = Depth to spider site
-m = Min Word length
-w = Output file
-e = include emails
Mimikatz – Security Audit Tool
Mimikatz is another popular security audit tool to extract plaintexts passwords, hash, PIN code, and Kerberos tickets from memory. It’s mainly used to move laterally around the network elevating privileges one step at a time.
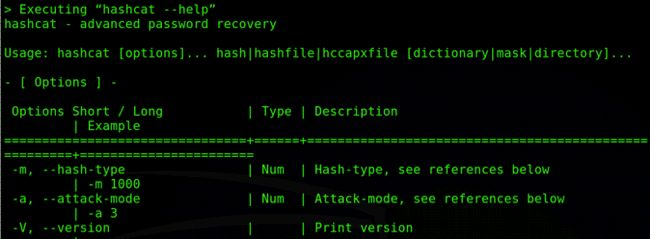
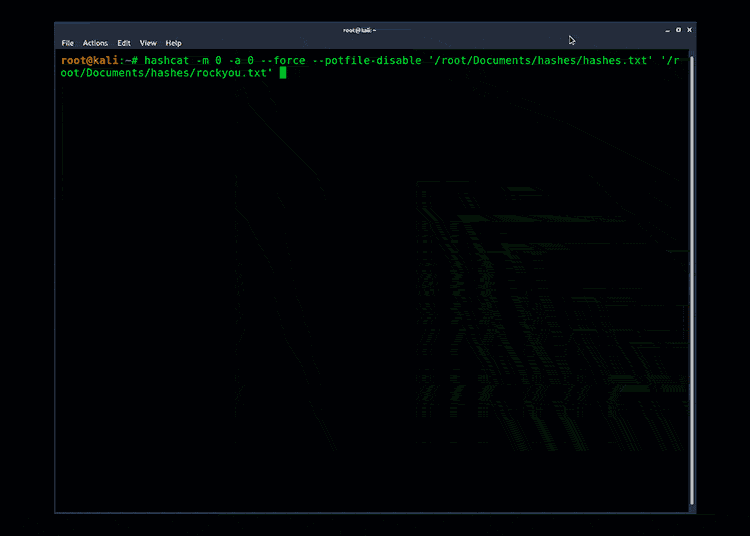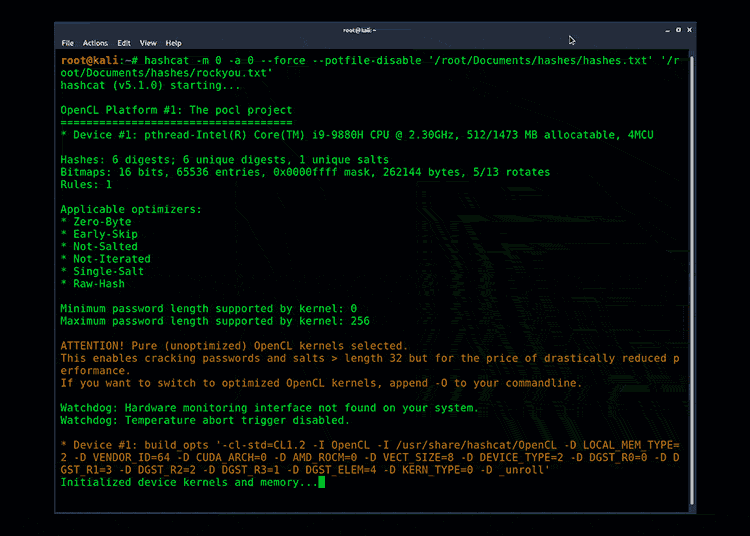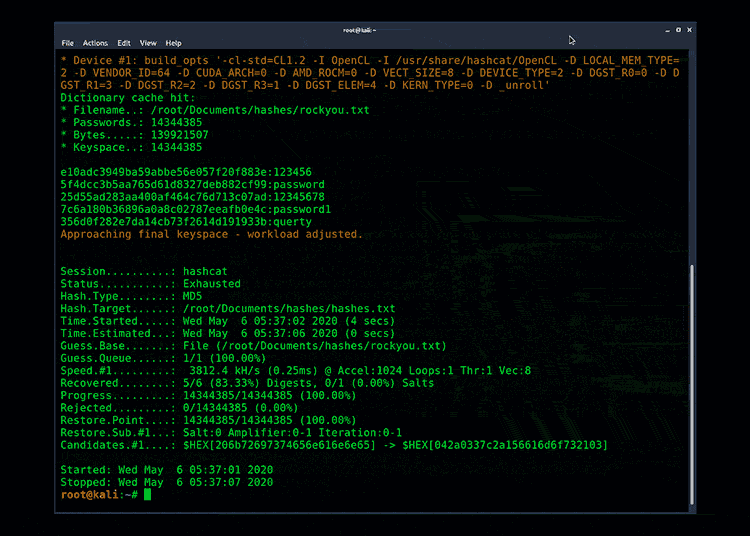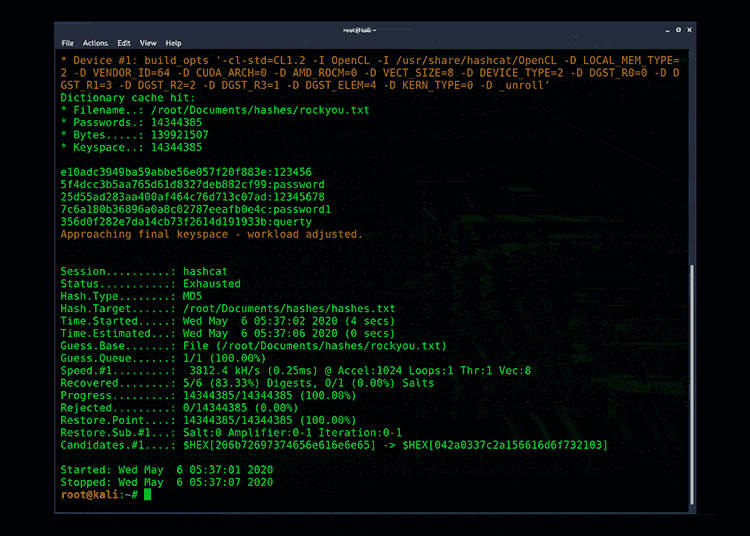
Hashcat – hashcat is the world’s fastest and most advanced password recovery utility
Hashcat is the tool most commonly used to perform different attack modes such as straight, combinations, brute-force, and hybrid attacks.
Hashcat attack mode options:
Example of a hashcat command:
Command line options:
-m = hash type (0 = MD5, 100 = Sha1, 1000 = NTLM)
-a = attack mode
0 | Straight
1 | Combination
3 | Brute-force
6 | Hybrid Wordlist + Mask
7 | Hybrid Mask + Wordlist
Pipal Password Analyzer
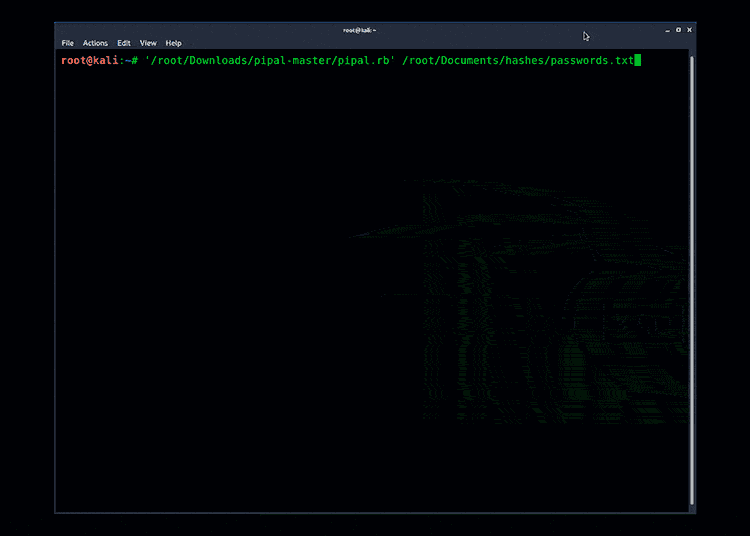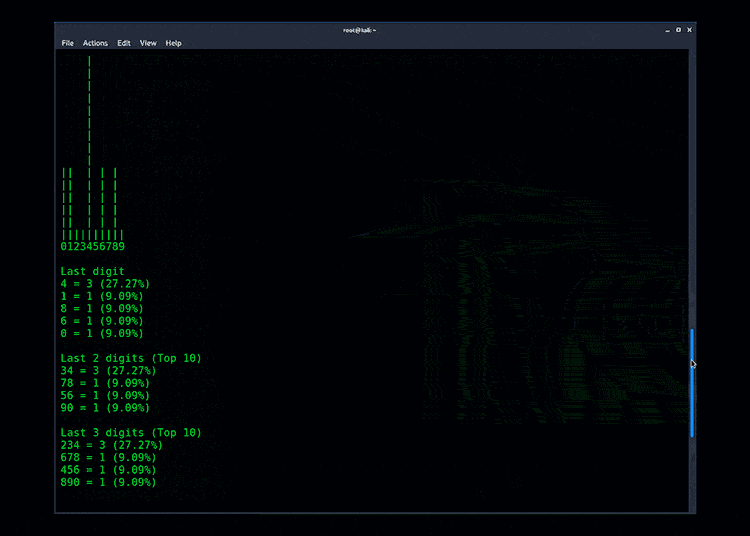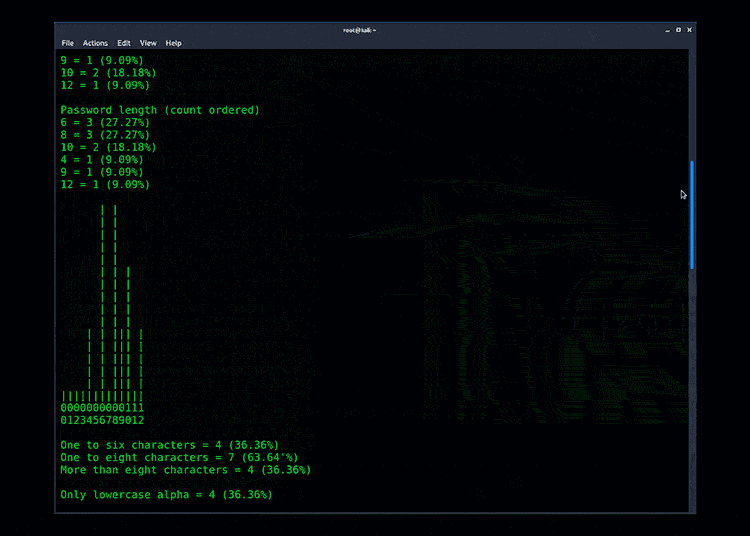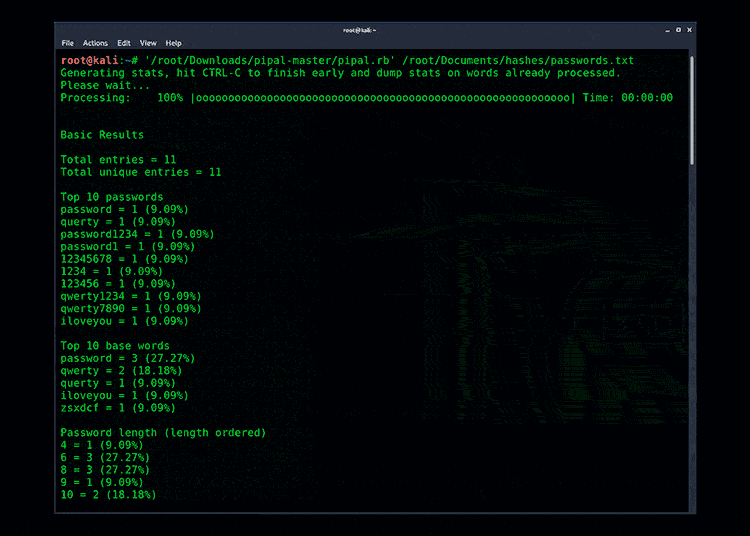
As you’re cracking passwords or analyzing password dumps, a great way to understand the passwords is to analyze them using a password analyzer. There are several excellent tools but Pipal is one of my favorites. It’s quite simple, yet powerful.
All you need to do is run the Pipal ruby against a password file. In the following example I am using the ‘rockyou’ password file:
Example output from Pipal Password Analyzer:
Summary
These are just a few of the top password-cracking tools available and as you can see, a password can be easily cracked. So it’s important to make the task as difficult as possible for cybercriminals and ensure that for critical systems and applications a password is not the only security control protecting your environment.
One of the main issues you’ll face is with your end-users being responsible for creating and maintaining the passwords they use. Make it easier for them by choosing a security solution that’s usable.
With users often having to manage 30 or more different user accounts and credentials, it’s almost certain they’ll reuse passwords or use some variation of the same password. This means once an attacker has compromised one password, it’s only a matter of time before they’ll guess the others too, and with tools like Hashcat, along with good wordlists and rules—it won’t take long!
Ensure that a password is not the only security control protecting your environment
We must educate end-users and make the right tools available to them so they don’t develop bad security hygiene. Let’s make security usable and easy, and empower users to form a stronger front-line defense.
Finally, here are my 10 security tips to help users protect themselves, their families, and the companies they work for. Security starts at home. Users must be educated and empowered beyond the workplace.
10 security tips to reduce your password risks
- Use a strong passphrase
- Log out of systems when you’re not using them
- Don’t reuse passwords
- Use a password manager
- Longer passwords are better if they are also complex
- Rotate passwords
- Use multi-factor authentication, or at least 2FA
- Audit activity
- Don’t be afraid to ask for advice
- And for businesses—familiarize yourself with enterprise password management, and use a Privileged Access Management (PAM) product