This post is part of a series about IoT security risks and how you can minimize them.
Read Part 2 here.
Welcome to the world of IoT (Internet of Things). More devices get connected online every minute, with more than 9-billion devices performing all sorts of tasks and automation. Every day, employees power up their devices and connect to the internet. They check the news, receive and respond to emails, chat with colleagues, pay invoices, work, shop, listen to music, stream the news; the list goes on and on.
The connected world is a reality. In the past few years, we’ve seen new technologies introduced that connect to the internet, collect vast amounts of data and send it across the world to be analyzed, monetized, used to improve our daily social life, and sometimes—stolen. This includes medical and health devices, engines, power stations, wind turbines, transportation, financial applications, CCTV, and even children’s toys.
The Internet of Things in business
The Industrial Internet has smart cities coming online with sensors and data that monitor every move we make, for example, autonomous vehicles communicating with the infrastructure to help manage traffic lights, weather condition alerts, and road traffic to ensure the most efficient traffic flow. Everything from payment systems to medical, energy, and infrastructure systems are continuously analyzing data to improve the services these companies provide and to stay innovative.
The challenge of IoT is that the companies that produce and manufacture the IoT systems including Industrial Control Systems (ICS), Supervisory Control and Data Acquisition (SCADA), Sensors and Programmable Logic Controllers (PLC’s), typically work over a long production life cycle, usually between 7 to 20 years. Ease of use and robust design take priority over security in almost all scenarios, with security an afterthought.
At the other end of the spectrum, consumers must also consider IoT device security. Vendors may eventually stop supporting their smart devices due to IoT security concerns. Security updates end and their devices become vulnerable to cyber-attacks. This has already happened with webcams, mobile phones, tablets, and smart home devices that typically only have a few years of warranty and support. A recent security vulnerability in Western Digital MyBook Live devices resulted in many customers having their devices remotely wiped and sensitive data loss.
Many newer IoT systems and devices are running legacy operating systems, including old Linux versions, Windows 7, and even Windows XP; firmware that contains hard-coded passwords; web interfaces running over HTTP; security controls with a simple PIN; and no authentication integration or encryption. This might have worked for a traditional perimeter security approach that could be controlled and secured from outside abuse. However, with today’s cloud, mobile, and connectivity, it’s nearly impossible to protect systems that are constantly being exposed to the public internet.
The lack of security by design means that risks and threats to IoT devices and systems are very high, and companies thinking of deploying IoT must consider the security challenges and increased risks against the productivity benefits.
In the home, most devices you purchase today come ready to connect with an app to communicate, configure, and connect with your home network, as well as get future software updates online. I’ve seen all sorts of devices that need firmware updates such as BBQs, electric kettles, washing machines, and lightbulbs. You may have several devices connected to the home network that you manage directly from your mobile devices. But how much thought did you give to the challenges of securing your IoT devices before connecting with them?
IoT and the balance of security
The types of functions of IoT-connected devices and the tasks they carry out have changed dramatically. In the past, computers had the ability to be reprogrammed and changed to perform various functions—be it a web application, some type of financial application, or even a database. Today, devices and their associated hardware are now carrying out very specific functions, often for simple tasks. So, we’re seeing many more microsystems and microprocessors being put in place.
IoT devices and systems must be considered from a security risk perspective. I don’t look at an IoT device as simply an IoT device, nor do I treat them all equally. I focus on its function. Is it a data processor? Is it a data collector? Is it a data correlator? I look at what its actual role in the network is.
Taking a risk approach poses a different set of questions. Is it something that could potentially attack the network? Is it something that could have data poisoning? Can the data it is generating be manipulated? Is it providing an access point for an attacker to gain access to the larger network?
Bottom line: We need to do better risk assessments of IoT and our network-connected devices, instead of just looking at them as purely functional connected devices.
What are the Risks of IoT and how are devices targeted?
The Internet of Things introduces several new risks and techniques that enable them to be compromised. The OWASP (Open Web Application Security Project) has created the OWASP Internet of Things Project to help everyone gain a better understanding of IoT security threats. The goal is to ensure that when creating, deploying, or using IoT devices we make better security decisions.
Shown below are the OWASP Top 10 Security Risks for IoT:
Summary of OWASP Top 10 IoT security risks:
- Weak, Guessable, or Hardcoded Passwords
- Insecure Network Services
- Insecure Ecosystem Interfaces
- Lack of Secure Update Mechanism
- Use of Insecure or Outdated Components
- Insufficient Privacy Protection
- Insecure Data Transfer and Storage
- Lack of Device Management
- Insecure Default Settings
- Lack of Physical Hardening
Always perform a risk analysis of any devices that you deploy and use. You need to understand the type of data the devices collect, if the data can be modified, any function changes, how the devices are used, if the devices could be used in a DDoS attack, or if an attacker could abuse the device to gain access to the wider network. Mapping your IoT devices to the OWASP Top 10 is an important first step that will help you determine what type of security controls you need to put in place for each device and system.
Let’s take a deeper look at some of these IoT hacking methods and steps.
Ethical Hacker’s Guide to Minimizing IoT Risks
STAGE 0: Pre-Engagement
The first step in an ethical hack is to determine the goals, target, and scope of your activities. You should always ensure you do no harm. So, make sure your plan adheres to an ethical code such as do no harm, is educational, and stays within legal boundaries.
Confirm you have the proper permission from your organization to run the hacking tools you’ll use. Are you permitted to target employees, or only systems and applications? This typically depends on how closely you want to simulate a real-world attack.
If your organization has a lab environment, test your toolset there first before you begin the active hack. If your actions will trigger alarms, you’ll know security controls are doing their job. If not, there may be misconfigurations that you will want to follow up on.
STAGE 1: Passive Recon
This step applies to practically all engagements. For IoT, this usually means learning about what devices are being used, versions used, locations and configurations. Open-Source Intelligence (OSINT) is a technique that you can use to gather whatever devices you can discover.
OSINT is critical to any risk assessment of a company’s security, especially the hardening of systems and devices. With OSINT, a cyber criminal can obtain publicly available information to gain network access. The more information you gather, the better prepared you’ll be. At times I have found that when one attack path doesn’t work, a solid OSINT review allows me to adapt quickly.
Shodan is another great tool you can use to discover devices connected to the public internet and what ports are open.
STAGE 2: The Hardware – Opening the Devices to Discover What is Inside
Once you have acquired a solid digital footprint on the devices being used, your next step is to learn as much about the devices as possible:
Images and Design
You can learn a lot just by looking at the devices or by searching the FCC.io if you know the FCC ID. This can sometimes show you more information on the images, such as UART (universal asynchronous receiver-transmitter) or JTAG (Joint Test Action Group) ports.
Let’s take a closer look at several devices and some methods to gather information:
- Documentation
- FCC Filings
- Online Reviews
- Patents
- Hands-On
One of my handy tools is an iFIXIT toolkit, several magnifying glasses, and a device holder to keep things steady. Make sure you open it without breaking the plastic clips.
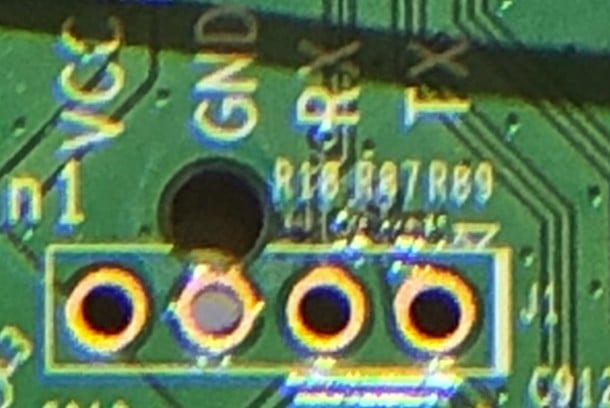
First, identify everything you can see using a good magnifying glass to reveal the small details. Look for possible interface ports, chips, and memory that can help you understand how the device is made. I tend to look for a way to connect directly to the device. You should look for G = Ground, Tx = Transmit, Rx = Receive and V = Voltage. The power supply is typically 3.3v or 5v, but always starts with the lowest voltage; otherwise, you could burn out the device.
The image below shows an example of a webcam that has a UART interface identified by “console.” However, the manufacturer of this device has made it a little more difficult to connect, and this one requires some soldering skills.
Some devices display better labeling and are easier to connect to without requiring soldering. The example here shows how you can simply connect without soldering by using clips or gator grips to ensure you have a strong connection.
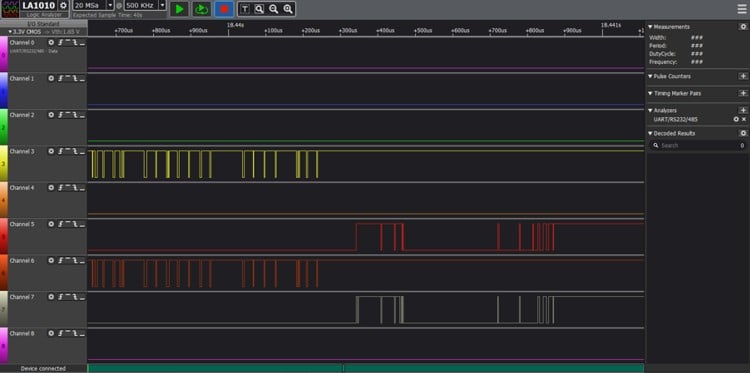
You may also discover devices that do not easily identify their interface, so you will have to conduct some trial and error using a Logic Analyzer or an oscilloscope. I find the Kingst Logic Analyzer sufficient for what I need though there are many choices available. This allows me to identify the interfaces. An example of this is shown below.
The example above shows the data collected from a router UART interface.
- Channel 3 = Yellow = VCC
- Channel 5 = Red = Rx
- Channel 6 = Orange = Tx
- Channel 7 = Grey = Ground
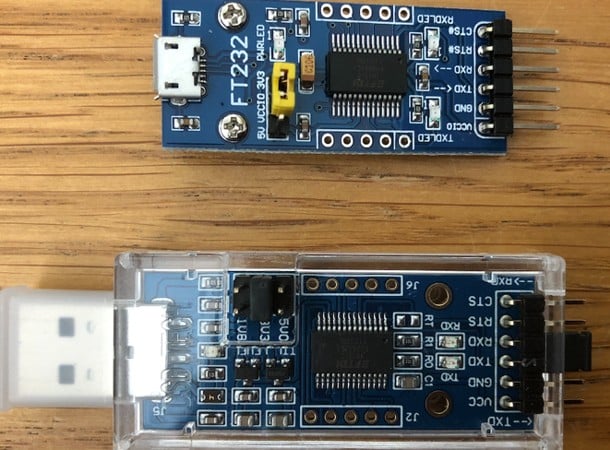
Once you’ve identified the interfaces you can now connect them to an FDTI USB device such as the FT232RL. Connect to the correct pins that you will use to communicate with the device.
In the example below, I have connected my FT232 to the interface on the router after using the Logic Analyzer to ensure I have the correct interfaces. Once connected, I communicate with the device using the command:
The ttyUSBx may be different on your machine depending on how many USB devices you have connected.
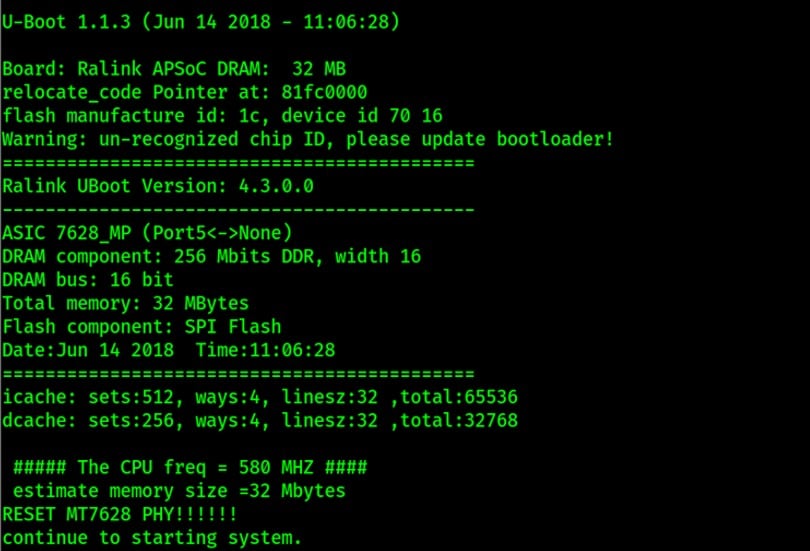
Once connected, I can now observe the device getting booted.
STAGE 3: The Firmware Boot
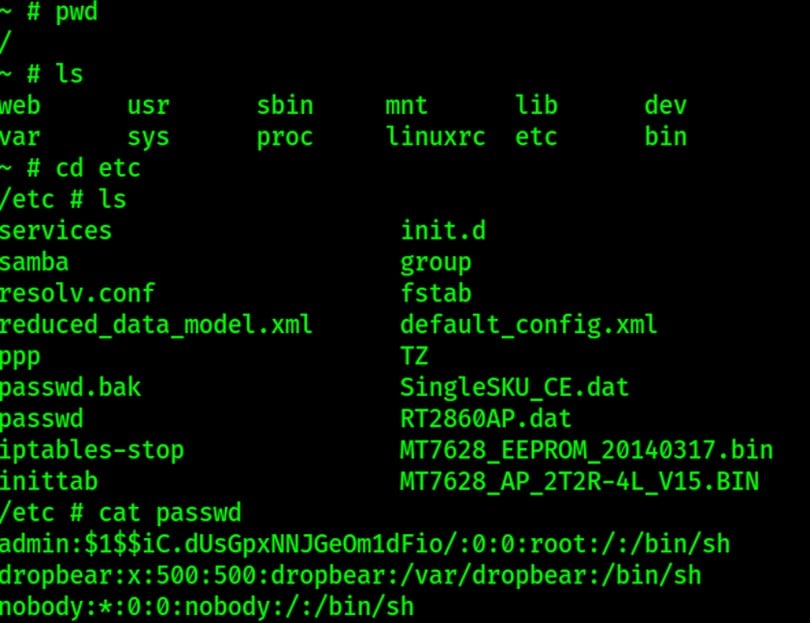
Once booted, I can interact with the device via the command prompt. I can check configuration files, versions, history, and log files, etc. For example, below I have searched the directories for interesting files and found that I can read the passwd file for users and passwords.
Knowing the device users and password hashes, I can take those hashes and if they are weak or previously compromised credentials, they will be easy to crack. Let’s move those to our “kracken” machine and see if we can crack them.
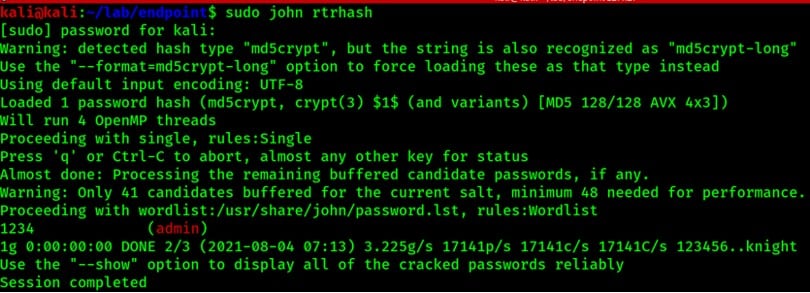
Using John, I can target the discovered hash for the admin user.
As you can see that the password was easy to crack since it was a weak credential that should never have been used in production.
User = Admin
Password = 1234
Recommendation
Far too many organizations make the mistake of not changing default credentials, using easy passwords that can be cracked, or using the same credentials on all devices to make them easier to manage. To keep your organization safe, you must manage IoT device credentials using strong, unique passwords that are different for all devices.
Make it easy on yourself by using a Password Manager or a Privileged Access Management solution to help manage IoT devices throughout your environment.
Check out Part 2 of this series to learn more about IoT security risks and how to manage them.
Interested in learning more? Listen to our recent podcast, Practical IoT Hacking with Beau Woods and Paulino Calderon.